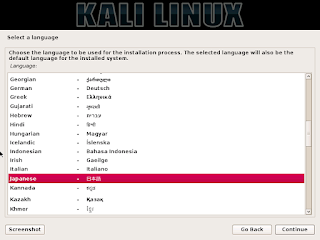
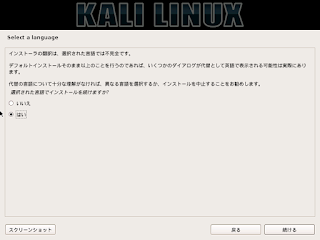
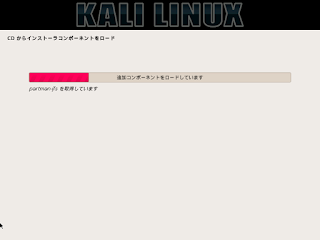
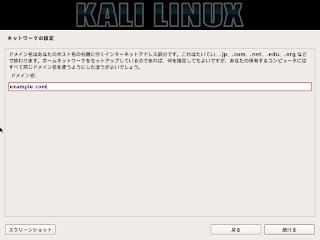
+ RHSA-2016:1978 Important: python-twisted-web security update
https://rhn.redhat.com/errata/RHSA-2016-1978.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1000111
+ Google Chrome 53.0.2785.143 released
https://googlechromereleases.blogspot.jp/2016/09/stable-channel-update-for-desktop_29.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5177
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5178
+ CESA-2016:1940 Important CentOS 6 openssl Security Update
http://lwn.net/Alerts/702199/
+ CESA-2016:1944 Important CentOS 5 bind Security Update
http://lwn.net/Alerts/702195/
+ CESA-2016:1943 Important CentOS 5 kvm Security Update
http://lwn.net/Alerts/702197/
+ CESA-2016:1945 Important CentOS 5 bind97 Security Update
http://lwn.net/Alerts/702196/
+ CESA-2016:1940 Important CentOS 7 openssl Security Update
http://lwn.net/Alerts/702198/
+ CESA-2016:1944 Important CentOS 6 bind Security Update
http://lwn.net/Alerts/702194/
+ CESA-2016:1944 Important CentOS 7 bind Security Update
http://lwn.net/Alerts/702193/
+ UPDATE: Multiple Vulnerabilities in OpenSSL Affecting Cisco Products: September 2016
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160927-openssl
+ PostgreSQL 9.6 Released!
https://www.postgresql.org/about/news/1703/
https://www.postgresql.org/docs/9.6/static/release-9-6.html
JVNDB-2016-000183 baserCMS 用プラグイン「アップローダー」におけるクロスサイトリクエストフォージェリの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000183.html
JVNDB-2016-000182 baserCMS 用プラグイン「メールフォーム」におけるクロスサイトリクエストフォージェリの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000182.html
JVNDB-2016-000181 baserCMS 用プラグイン「フィードリーダー」におけるクロスサイトリクエストフォージェリの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000181.html
JVNDB-2016-000180 baserCMS 用プラグイン「ブログ」におけるクロスサイトリクエストフォージェリの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000180.html
JVNDB-2016-000179 baserCMS におけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000179.html
JVNDB-2016-000178 baserCMS におけるクロスサイトリクエストフォージェリの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000178.html
JVNDB-2016-000177 baserCMS におけるクロスサイトリクエストフォージェリの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000177.html
JVNDB-2016-000176 baserCMS 用プラグイン「ブログ」におけるクロスサイトリクエストフォージェリの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000176.html
データは語る
標的型攻撃対策製品市場は前年比で77.9%増加
http://itpro.nikkeibp.co.jp/atcl/column/16/072600158/092800010/?ST=security?itp_list_theme
「アジア太平洋地域の企業は攻撃に気付くのが遅い」、ファイア・アイがセキュリティ動向を解説
http://itpro.nikkeibp.co.jp/atcl/news/16/092902849/?ST=security?itp_list_theme
JVNVU#90976810 Aternity に複数の脆弱性
http://jvn.jp/vu/JVNVU90976810/index.html
JVN#92765814 baserCMS における複数の脆弱性
http://jvn.jp/jp/JVN92765814/index.html
JVN#72559412 ManageEngine ServiceDesk Plus における Cookie の生成処理に関する脆弱性
http://jvn.jp/jp/JVN72559412/index.html
JVN#89726415 ManageEngine ServiceDesk Plus におけるアクセス制限不備の脆弱性
http://jvn.jp/jp/JVN89726415/index.html
JVN#50347324 ManageEngine ServiceDesk Plus におけるクロスサイトスクリプティングの脆弱性
http://jvn.jp/jp/JVN50347324/index.html
2016年9月30日金曜日
2016年9月29日木曜日
29日 木曜日、赤口
+ RHSA-2016:1944 Important: bind security update
https://rhn.redhat.com/errata/RHSA-2016-1944.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2776
+ RHSA-2016:1945 Important: bind97 security update
https://rhn.redhat.com/errata/RHSA-2016-1945.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2776
+ RHSA-2016:1944 Important: bind security update
https://rhn.redhat.com/errata/RHSA-2016-1944.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2776
+ UPDATE: Cisco Email Security Appliance Internal Testing Interface Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160922-esa
+ UPDATE: Multiple Vulnerabilities in OpenSSL Affecting Cisco Products: September 2016
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160927-openssl
+ Cisco Videoscape Distribution Suite Service Manager Reflective Cross-Site Scripting Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-vds
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6418
+ Cisco IOS and IOS XE Software Smart Install Memory Leak Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-smi
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6385
+ Cisco IOS XR Software Open Shortest Path First Link State Advertisement Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-ospf
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6421
+ Cisco IOS and IOS XE Software Multicast Routing Denial of Service Vulnerabilities
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-msdp
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6382
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6392
+ Cisco IOS and IOS XE Software IP Detail Record Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-ipdr
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6379
+ Cisco IOS and IOS XE Software Internet Key Exchange Version 1 Fragmentation Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-ios-ikev1
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6381
+ Cisco IOS and IOS XE Software H.323 Message Validation Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-h323
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6384
+ Cisco IOS XE Software IP Fragment Reassembly Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-frag
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6386
+ Cisco Firepower Management Center SQL Injection Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-fpmc
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6419
+ Cisco Firepower Management Center Privilege Escalation Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-fmc1
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6420
+ Cisco Firepower Management Center and FireSIGHT System Software Cross-Site Request Forgery Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-fmc
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6417
+ Cisco IOS XE Software NAT Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-esp-nat
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6378
+ Cisco IOS and IOS XE Software DNS Forwarder Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-dns
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6380
+ Cisco IOS Software Common Industrial Protocol Request Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-cip
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6391
+ Cisco AsyncOS File Transfer Protocol Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-aos
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6416
+ Cisco IOS and IOS XE Software AAA Login Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160928-aaados
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6393
+ JVNVU#90255292 ISC BIND 9 にサービス運用妨害 (DoS) の脆弱性
http://jvn.jp/vu/JVNVU90255292/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2776
+ UPDATE: JVNVU#98667810 OpenSSL に複数の脆弱性
http://jvn.jp/vu/JVNVU98667810/index.html
VU#706359 Aternity version 9 vulnerable to cross-site scripting and remote code execution
https://www.kb.cert.org/vuls/id/706359
NECネクサ、Syslogログを分析してサイバー攻撃の定期レポートを作成するサービス
http://itpro.nikkeibp.co.jp/atcl/news/16/092802820/?ST=security?itp_list_theme
2016年9月28日水曜日
28日 水曜日、大安
+ BIND 9.10.4-P3, 9.9.9-P3 released
http://ftp.isc.org/isc/bind9/9.10.4-P3/RELEASE-NOTES-bind-9.10.4-P3.html
http://ftp.isc.org/isc/bind9/9.9.9-P3/RELEASE-NOTES-bind-9.9.9-P3.html
+ RHSA-2016:1940 Important: openssl security update
https://rhn.redhat.com/errata/RHSA-2016-1940.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2177
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2178
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2179
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2180
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2181
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6302
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6304
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6306
+ RHSA-2016:1940 Important: openssl security update
https://rhn.redhat.com/errata/RHSA-2016-1940.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2177
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2178
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2179
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2180
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2181
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6302
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6304
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6306
+ Multiple Vulnerabilities in OpenSSL Affecting Cisco Products: September 2016
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160927-openssl
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2177
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2178
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2179
+ UPDATE: Cisco IOS and Cisco IOS XE ntp Subsystem Unauthorized Access Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160419-ios
+ OpenSSL 1.1.0b, 1.0.2j released
https://www.openssl.org/news/changelog.html#x1
https://www.openssl.org/news/cl110.txt
https://www.openssl.org/news/cl102.txt
+ OpenSSL Security Advisory [26 Sep 2016]
https://www.openssl.org/news/secadv/20160926.txt
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6309
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7052
+ SA72691 GNU Bash PS4 Expansion Privilege Escalation Vulnerability
https://secunia.com/advisories/72691/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7543
+ JVNVU#99474230 OpenSSL に複数の脆弱性
http://jvn.jp/vu/JVNVU99474230/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6309
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7052
+ BIND Bug in 'buffer.c' Constructing Query Responses Lets Remote Users Cause the Target Service to Crash
http://www.securitytracker.com/id/1036903
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2776
+ Linux Kernel 4.6.3 Netfilter Privilege Escalation
https://cxsecurity.com/issue/WLB-2016090197
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4997
+ GNU Bash CVE-2016-7543 Local Command Execution Vulnerability
http://www.securityfocus.com/bid/93183
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7543
+ GNU Wget CVE-2016-7098 Security Bypass Vulnerability
http://www.securityfocus.com/bid/93157
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7098
Barman 2.0 Released
https://www.postgresql.org/about/news/1702/
dbMigration .NET 3.7 released
https://www.postgresql.org/about/news/1701/
JVNDB-2016-000168 FlashAir におけるアクセス制限不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000168.html
サンワサプライ、微細マイクロカットを採用した法人向けシュレッダー
http://itpro.nikkeibp.co.jp/atcl/news/16/092702802/?ST=security?itp_list_theme
http://ftp.isc.org/isc/bind9/9.10.4-P3/RELEASE-NOTES-bind-9.10.4-P3.html
http://ftp.isc.org/isc/bind9/9.9.9-P3/RELEASE-NOTES-bind-9.9.9-P3.html
+ RHSA-2016:1940 Important: openssl security update
https://rhn.redhat.com/errata/RHSA-2016-1940.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2177
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2178
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2179
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2180
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2181
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6302
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6304
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6306
+ RHSA-2016:1940 Important: openssl security update
https://rhn.redhat.com/errata/RHSA-2016-1940.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2177
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2178
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2179
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2180
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2181
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6302
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6304
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6306
+ Multiple Vulnerabilities in OpenSSL Affecting Cisco Products: September 2016
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160927-openssl
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2177
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2178
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2179
+ UPDATE: Cisco IOS and Cisco IOS XE ntp Subsystem Unauthorized Access Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160419-ios
+ OpenSSL 1.1.0b, 1.0.2j released
https://www.openssl.org/news/changelog.html#x1
https://www.openssl.org/news/cl110.txt
https://www.openssl.org/news/cl102.txt
+ OpenSSL Security Advisory [26 Sep 2016]
https://www.openssl.org/news/secadv/20160926.txt
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6309
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7052
+ SA72691 GNU Bash PS4 Expansion Privilege Escalation Vulnerability
https://secunia.com/advisories/72691/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7543
+ JVNVU#99474230 OpenSSL に複数の脆弱性
http://jvn.jp/vu/JVNVU99474230/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6309
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7052
+ BIND Bug in 'buffer.c' Constructing Query Responses Lets Remote Users Cause the Target Service to Crash
http://www.securitytracker.com/id/1036903
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2776
+ Linux Kernel 4.6.3 Netfilter Privilege Escalation
https://cxsecurity.com/issue/WLB-2016090197
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4997
+ GNU Bash CVE-2016-7543 Local Command Execution Vulnerability
http://www.securityfocus.com/bid/93183
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7543
+ GNU Wget CVE-2016-7098 Security Bypass Vulnerability
http://www.securityfocus.com/bid/93157
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7098
Barman 2.0 Released
https://www.postgresql.org/about/news/1702/
dbMigration .NET 3.7 released
https://www.postgresql.org/about/news/1701/
JVNDB-2016-000168 FlashAir におけるアクセス制限不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000168.html
サンワサプライ、微細マイクロカットを採用した法人向けシュレッダー
http://itpro.nikkeibp.co.jp/atcl/news/16/092702802/?ST=security?itp_list_theme
2016年9月27日火曜日
27日 火曜日、仏滅
+ Mozilla Firefox 49.0.1 released
https://www.mozilla.org/en-US/firefox/49.0.1/releasenotes/
+ SA72410 OpenSSL Large Message Handling Use-After-Free Vulnerability
https://secunia.com/advisories/72410/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6309
+ SA72514 OpenSSL CRL Sanity Check Denial of Service Vulnerability
https://secunia.com/advisories/72514/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7052
+ OpenSSL CVE-2016-7052 Denial of Service Vulnerability
http://www.securityfocus.com/bid/93171
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7052
2016年9月26日月曜日
26日 月曜日、先負
+ RHSA-2016:1912 Critical: firefox security update
https://rhn.redhat.com/errata/RHSA-2016-1912.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5250
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5257
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5261
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5270
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5272
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5274
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5276
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5277
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5278
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5280
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5281
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5284
+ About the security content of iOS 10.0.2
https://support.apple.com/ja-jp/HT207199
+ About the security content of iCloud for Windows 6.0
https://support.apple.com/ja-jp/HT207147
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4762
+ About the security content of macOS Server 5.2
https://support.apple.com/ja-jp/HT207171
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4694
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4754
+ About the security content of Safari 10
https://support.apple.com/ja-jp/HT207157
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4618
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4751
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4728
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4758
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4611
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4729
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4730
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4731
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4734
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4735
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4737
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4759
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4762
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4766
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4767
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4768
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4769
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4760
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4733
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4765
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4763
+ CESA-2016:1912 Critical CentOS 5 firefox Security Update
http://lwn.net/Alerts/701617/
+ CESA-2016:1912 Critical CentOS 6 firefox Security Update
http://lwn.net/Alerts/701613/
+ CESA-2016:1912 Critical CentOS 7 firefox Security Update
http://lwn.net/Alerts/701614/
+ Cisco Email Security Appliance Internal Testing Interface Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160922-esa
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6406
+ UPDATE: Multiple Vulnerabilities in OpenSSL (December 2015) Affecting Cisco Products
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20151204-openssl
+ Cisco IOS and IOS XE iox Command Injection Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-iox
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6414
+ Cisco Firepower Management Center and FireSIGHT System Software SSLIinspection Bypass Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-fmc
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6411
+ Cisco IOS and IOS XE Software Data in Motion Component Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-dmo
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6414
+ Cisco Cloud Services Platform 2100 Remote Command Execution Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-csp2100-2
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6374
+ Cisco Cloud Services Platform 2100 Command Injection Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-csp2100-1
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6373
+ Cisco Prime Home Web-Based User Interface XML External Entity Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-cph
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6408
+ Cisco Application-Hosting Framework HTTP Header Injection Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-caf1
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6412
+ Cisco IOS and IOS XE Software Application-Hosting Framework Unauthorized File Access Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-caf
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6410
+ Cisco Application Policy Infrastructure Controller Binary Privilege Escalation Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-apic
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6413
+ Linux kernel 4.7.5, 4.4.22 released
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.7.5
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.4.22
+ OpenSSL 1.1.0a, 1.0.2i, 1.0.1u released
https://www.openssl.org/news/changelog.html#x1
https://www.openssl.org/news/cl102.txt
https://www.openssl.org/news/cl101.txt
+ OpenSSL Security Advisory [22 Sep 2016]
https://www.openssl.org/news/secadv/20160922.txt
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6304
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6305
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2183
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6303
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6302
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2180
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2177
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2178
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2179
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2181
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6306
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6307
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6308
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6307
+ Samba 4.4.6 Available for Download
https://www.samba.org/samba/history/samba-4.4.6.html
+ SA72712 OpenSSL Multiple Vulnerabilities
https://secunia.com/advisories/72712/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2178
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2179
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2180
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2181
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6302
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6304
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6305
+ Apache POI 3.15 released
http://poi.apache.org/changes.html
+ Sysstat 11.4.1, 11.2.7 released
http://sebastien.godard.pagesperso-orange.fr/
+ JVNVU#98667810 OpenSSL に複数の脆弱性
http://jvn.jp/vu/JVNVU98667810/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6304
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6305
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2183
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6303
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6302
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2180
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2177
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2178
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2179
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2181
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6306
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6307
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6308
+ JVNVU#90950877 複数の Apple 製品の脆弱性に対するアップデート
http://jvn.jp/vu/JVNVU90950877/
+ OpenSSL 1.1.0 OCSP DoS resource exhaustion
https://cxsecurity.com/issue/WLB-201609017
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6304
+ Microsoft Internet Explorer 11 CORS Disrespect
https://cxsecurity.com/issue/WLB-2016090165
+ Microsoft Office PowerPoint 2010 - Invalid Pointer Reference
https://cxsecurity.com/issue/WLB-2016090158
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3357
+ RSA Identity Management and Governance Flaw Lets Remote Authenticated Users Obtain Information About Other User Accounts
http://www.securitytracker.com/id/1036896
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0918
Announcement: Amazon RDS for PostgreSQL Enhancements: Support for new minor versions, Logical Replication, and Amazon RDS PostgreSQL as a source for AWS DMS
https://www.postgresql.org/about/news/1700/
JVNDB-2016-000167 Geeklog IVYWE版の複数のプラグインにおけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000167.html
UPATE: JVNVU#92998929 ImageMagick に入力値検証不備の脆弱性
http://jvn.jp/vu/JVNVU92998929/
JVN#46087986 Geeklog IVYWE版の複数のプラグインにおけるクロスサイトスクリプティングの脆弱性
http://jvn.jp/jp/JVN46087986/
速報
NEC、ソニー損保にサイバー攻撃対策の多層防御システムを構築
http://itpro.nikkeibp.co.jp/atcl/news/16/092302770/?ST=security?itp_list_theme
速報
5億人以上の個人情報流出、Yahoo!に国家が関与するサイバー攻撃か
http://itpro.nikkeibp.co.jp/atcl/news/16/092302766/?ST=security?itp_list_theme
https://rhn.redhat.com/errata/RHSA-2016-1912.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5250
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5257
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5261
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5270
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5272
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5274
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5276
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5277
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5278
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5280
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5281
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5284
+ About the security content of iOS 10.0.2
https://support.apple.com/ja-jp/HT207199
+ About the security content of iCloud for Windows 6.0
https://support.apple.com/ja-jp/HT207147
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4762
+ About the security content of macOS Server 5.2
https://support.apple.com/ja-jp/HT207171
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4694
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4754
+ About the security content of Safari 10
https://support.apple.com/ja-jp/HT207157
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4618
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4751
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4728
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4758
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4611
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4729
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4730
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4731
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4734
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4735
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4737
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4759
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4762
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4766
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4767
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4768
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4769
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4760
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4733
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4765
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4763
+ CESA-2016:1912 Critical CentOS 5 firefox Security Update
http://lwn.net/Alerts/701617/
+ CESA-2016:1912 Critical CentOS 6 firefox Security Update
http://lwn.net/Alerts/701613/
+ CESA-2016:1912 Critical CentOS 7 firefox Security Update
http://lwn.net/Alerts/701614/
+ Cisco Email Security Appliance Internal Testing Interface Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160922-esa
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6406
+ UPDATE: Multiple Vulnerabilities in OpenSSL (December 2015) Affecting Cisco Products
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20151204-openssl
+ Cisco IOS and IOS XE iox Command Injection Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-iox
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6414
+ Cisco Firepower Management Center and FireSIGHT System Software SSLIinspection Bypass Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-fmc
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6411
+ Cisco IOS and IOS XE Software Data in Motion Component Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-dmo
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6414
+ Cisco Cloud Services Platform 2100 Remote Command Execution Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-csp2100-2
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6374
+ Cisco Cloud Services Platform 2100 Command Injection Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-csp2100-1
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6373
+ Cisco Prime Home Web-Based User Interface XML External Entity Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-cph
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6408
+ Cisco Application-Hosting Framework HTTP Header Injection Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-caf1
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6412
+ Cisco IOS and IOS XE Software Application-Hosting Framework Unauthorized File Access Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-caf
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6410
+ Cisco Application Policy Infrastructure Controller Binary Privilege Escalation Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160921-apic
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6413
+ Linux kernel 4.7.5, 4.4.22 released
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.7.5
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.4.22
+ OpenSSL 1.1.0a, 1.0.2i, 1.0.1u released
https://www.openssl.org/news/changelog.html#x1
https://www.openssl.org/news/cl102.txt
https://www.openssl.org/news/cl101.txt
+ OpenSSL Security Advisory [22 Sep 2016]
https://www.openssl.org/news/secadv/20160922.txt
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6304
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6305
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2183
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6303
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6302
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2180
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2177
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2178
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2179
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2181
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6306
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6307
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6308
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6307
+ Samba 4.4.6 Available for Download
https://www.samba.org/samba/history/samba-4.4.6.html
+ SA72712 OpenSSL Multiple Vulnerabilities
https://secunia.com/advisories/72712/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2178
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2179
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2180
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2181
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6302
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6304
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6305
+ Apache POI 3.15 released
http://poi.apache.org/changes.html
+ Sysstat 11.4.1, 11.2.7 released
http://sebastien.godard.pagesperso-orange.fr/
+ JVNVU#98667810 OpenSSL に複数の脆弱性
http://jvn.jp/vu/JVNVU98667810/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6304
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6305
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2183
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6303
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6302
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2180
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2177
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2178
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2179
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2181
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6306
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6307
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6308
+ JVNVU#90950877 複数の Apple 製品の脆弱性に対するアップデート
http://jvn.jp/vu/JVNVU90950877/
+ OpenSSL 1.1.0 OCSP DoS resource exhaustion
https://cxsecurity.com/issue/WLB-201609017
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6304
+ Microsoft Internet Explorer 11 CORS Disrespect
https://cxsecurity.com/issue/WLB-2016090165
+ Microsoft Office PowerPoint 2010 - Invalid Pointer Reference
https://cxsecurity.com/issue/WLB-2016090158
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3357
+ RSA Identity Management and Governance Flaw Lets Remote Authenticated Users Obtain Information About Other User Accounts
http://www.securitytracker.com/id/1036896
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0918
Announcement: Amazon RDS for PostgreSQL Enhancements: Support for new minor versions, Logical Replication, and Amazon RDS PostgreSQL as a source for AWS DMS
https://www.postgresql.org/about/news/1700/
JVNDB-2016-000167 Geeklog IVYWE版の複数のプラグインにおけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000167.html
UPATE: JVNVU#92998929 ImageMagick に入力値検証不備の脆弱性
http://jvn.jp/vu/JVNVU92998929/
JVN#46087986 Geeklog IVYWE版の複数のプラグインにおけるクロスサイトスクリプティングの脆弱性
http://jvn.jp/jp/JVN46087986/
速報
NEC、ソニー損保にサイバー攻撃対策の多層防御システムを構築
http://itpro.nikkeibp.co.jp/atcl/news/16/092302770/?ST=security?itp_list_theme
速報
5億人以上の個人情報流出、Yahoo!に国家が関与するサイバー攻撃か
http://itpro.nikkeibp.co.jp/atcl/news/16/092302766/?ST=security?itp_list_theme
2016年9月21日水曜日
21日 水曜日、仏滅
+ Mozilla Firefox 49.0 released
https://www.mozilla.org/en-US/firefox/49.0/releasenotes/
+ MFSA2016-85 Security vulnerabilities fixed in Firefox 49
https://www.mozilla.org/en-US/security/advisories/mfsa2016-85/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2827
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5270
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5271
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5272
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5273
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5276
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5274
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5277
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5275
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5278
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5279
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5280
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5281
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5282
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5283
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5284
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5256
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5257
+ CESA-2016:1847 Important CentOS 7 kernel Security Update
http://lwn.net/Alerts/701240/
+ UPDATE: Multiple Cisco Products Confidential Information Decryption Man-in-the-Middle Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20151125-ci
+ Cisco Unified Communications Manager Information Disclosure Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-201600208-ucm
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1317
+ UPDATE: IKEv1 Information Disclosure Vulnerability in Multiple Cisco Products
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160916-ikev1
+ Sudo 1.8.18 released
https://www.sudo.ws/stable.html#1.8.18
+ SA72624 Symantec Multiple Products Decomposer Engine RAR Multiple Vulnerabilities
https://secunia.com/advisories/72624/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5309
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5310
+ Apache Tomcat 7.0.72 Released
http://tomcat.apache.org/tomcat-7.0-doc/changelog.html
+ Mozilla Firefox MFSA 2016-85 Multiple Security Vulnerabilities
http://www.securityfocus.com/bid/93052
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5256
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2827
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5271
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5273
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5275
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5279
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5282
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5283
+ Mozilla Firefox Multiple Security Vulnerabilities
http://www.securityfocus.com/bid/93049
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5270
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5272
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5276
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5274
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5277
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5278
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5280
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5281
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5284
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5257
JVNDB-2016-000161 Android アプリ「マネーフォワード」における任意の操作が実行可能な脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000161.html
JVNDB-2016-000160 Android アプリ「マネーフォワード」における WebView クラスに関する脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000160.html
記者の眼
「原理主義になるな」、DeNAのセキュリティ部長が大事にしている10のこと
http://itpro.nikkeibp.co.jp/atcl/watcher/14/334361/090100653/?ST=security?itp_list_theme
https://www.mozilla.org/en-US/firefox/49.0/releasenotes/
+ MFSA2016-85 Security vulnerabilities fixed in Firefox 49
https://www.mozilla.org/en-US/security/advisories/mfsa2016-85/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2827
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5270
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5271
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5272
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5273
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5276
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5274
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5277
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5275
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5278
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5279
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5280
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5281
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5282
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5283
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5284
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5256
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5257
+ CESA-2016:1847 Important CentOS 7 kernel Security Update
http://lwn.net/Alerts/701240/
+ UPDATE: Multiple Cisco Products Confidential Information Decryption Man-in-the-Middle Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20151125-ci
+ Cisco Unified Communications Manager Information Disclosure Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-201600208-ucm
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1317
+ UPDATE: IKEv1 Information Disclosure Vulnerability in Multiple Cisco Products
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160916-ikev1
+ Sudo 1.8.18 released
https://www.sudo.ws/stable.html#1.8.18
+ SA72624 Symantec Multiple Products Decomposer Engine RAR Multiple Vulnerabilities
https://secunia.com/advisories/72624/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5309
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5310
+ Apache Tomcat 7.0.72 Released
http://tomcat.apache.org/tomcat-7.0-doc/changelog.html
+ Mozilla Firefox MFSA 2016-85 Multiple Security Vulnerabilities
http://www.securityfocus.com/bid/93052
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5256
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2827
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5271
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5273
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5275
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5279
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5282
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5283
+ Mozilla Firefox Multiple Security Vulnerabilities
http://www.securityfocus.com/bid/93049
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5270
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5272
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5276
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5274
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5277
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5278
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5280
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5281
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5284
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5257
JVNDB-2016-000161 Android アプリ「マネーフォワード」における任意の操作が実行可能な脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000161.html
JVNDB-2016-000160 Android アプリ「マネーフォワード」における WebView クラスに関する脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000160.html
記者の眼
「原理主義になるな」、DeNAのセキュリティ部長が大事にしている10のこと
http://itpro.nikkeibp.co.jp/atcl/watcher/14/334361/090100653/?ST=security?itp_list_theme
2016年9月20日火曜日
20日 火曜日、先負
+ CESA-2016:1844 Important CentOS 7 libarchive Security Update
http://lwn.net/Alerts/700944/
+ CESA-2016:1850 Important CentOS 6 libarchive Security Update
http://lwn.net/Alerts/700943/
+ UPDATE: IKEv1 Information Disclosure Vulnerability in Multiple Cisco Product
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160916-ikev1
+ UPDATE: Cisco Adaptive Security Appliance SNMP Remote Code Execution Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160817-asa-snmp
+ Linux kernel 4.1.33, 3.18.42 released
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.1.33
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.18.42
+ JDBC 1211 released
https://www.postgresql.org/about/news/1698/
+ PHP 5.6.26 released
http://www.php.net/ChangeLog-5.php#5.6.26
+ PHP Multiple Memory Corruption Errors Let Remote and Local Users Execute Arbitrary Code on the Target System
http://www.securitytracker.com/id/1036836
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7411
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7412
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7413
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7414
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7416
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7417
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7418
+ PHP CVE-2016-7418 Out-of-Bounds Read Denial of Service Vulnerability
http://www.securityfocus.com/bid/93011
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7418
+ PHP CVE-2016-7416 Stack Buffer Overflow Vulnerability
http://www.securityfocus.com/bid/93008
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7416
PostgreSQL PHP Generator 16.9 released
https://www.postgresql.org/about/news/1699/
PGLiveBackup Beta 1 Released
https://www.postgresql.org/about/news/1697/
Aiven brings easy, powerful hosted PostgreSQL to Microsoft Azure
https://www.postgresql.org/about/news/1695/
JVNDB-2016-000166 ウイルスバスター クラウドにおける検索対象に関する脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000166.html
JVNDB-2016-000165 Splunk Enterprise および Splunk Light におけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000165.html
JVNDB-2016-000164 Splunk Enterprise および Splunk Light におけるオープンリダイレクトの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000164.html
JVNDB-2016-000163 Splunk Enterprise および Splunk Light におけるオープンリダイレクトの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000163.html
JVNDB-2016-000162 Splunk Enterprise および Splunk Light におけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000162.html
松田次博 間違いだらけのネットワーク作り
どこまでやればセキュリティ対策は「合格点」?
http://itpro.nikkeibp.co.jp/atcl/watcher/14/230970/091500028/?ST=security?itp_list_theme
UPDATE: JVNVU#90754453 プロキシサーバを使った通信を行うアプリケーションに中間者攻撃 (MITM) が可能な脆弱性
http://jvn.jp/vu/JVNVU90754453/index.html
http://lwn.net/Alerts/700944/
+ CESA-2016:1850 Important CentOS 6 libarchive Security Update
http://lwn.net/Alerts/700943/
+ UPDATE: IKEv1 Information Disclosure Vulnerability in Multiple Cisco Product
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160916-ikev1
+ UPDATE: Cisco Adaptive Security Appliance SNMP Remote Code Execution Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160817-asa-snmp
+ Linux kernel 4.1.33, 3.18.42 released
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.1.33
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.18.42
+ JDBC 1211 released
https://www.postgresql.org/about/news/1698/
+ PHP 5.6.26 released
http://www.php.net/ChangeLog-5.php#5.6.26
+ PHP Multiple Memory Corruption Errors Let Remote and Local Users Execute Arbitrary Code on the Target System
http://www.securitytracker.com/id/1036836
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7411
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7412
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7413
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7414
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7416
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7417
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7418
+ PHP CVE-2016-7418 Out-of-Bounds Read Denial of Service Vulnerability
http://www.securityfocus.com/bid/93011
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7418
+ PHP CVE-2016-7416 Stack Buffer Overflow Vulnerability
http://www.securityfocus.com/bid/93008
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7416
PostgreSQL PHP Generator 16.9 released
https://www.postgresql.org/about/news/1699/
PGLiveBackup Beta 1 Released
https://www.postgresql.org/about/news/1697/
Aiven brings easy, powerful hosted PostgreSQL to Microsoft Azure
https://www.postgresql.org/about/news/1695/
JVNDB-2016-000166 ウイルスバスター クラウドにおける検索対象に関する脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000166.html
JVNDB-2016-000165 Splunk Enterprise および Splunk Light におけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000165.html
JVNDB-2016-000164 Splunk Enterprise および Splunk Light におけるオープンリダイレクトの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000164.html
JVNDB-2016-000163 Splunk Enterprise および Splunk Light におけるオープンリダイレクトの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000163.html
JVNDB-2016-000162 Splunk Enterprise および Splunk Light におけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000162.html
松田次博 間違いだらけのネットワーク作り
どこまでやればセキュリティ対策は「合格点」?
http://itpro.nikkeibp.co.jp/atcl/watcher/14/230970/091500028/?ST=security?itp_list_theme
UPDATE: JVNVU#90754453 プロキシサーバを使った通信を行うアプリケーションに中間者攻撃 (MITM) が可能な脆弱性
http://jvn.jp/vu/JVNVU90754453/index.html
2016年9月16日金曜日
16日 金曜日、大安
+ マイクロソフト セキュリティ アドバイザリ 3174644 Diffie-Hellman キー交換のサポートの更新
https://technet.microsoft.com/ja-jp/library/security/3174644
+ マイクロソフト セキュリティ アドバイザリ 3181759 ASP.NET Core のビュー コンポーネントの脆弱性により、特権が昇格される
https://technet.microsoft.com/ja-jp/library/security/3181759
+ Vim 8.0 released
https://groups.google.com/forum/#!topic/vim_announce/EKTuhjF3ET0
+ UPDATE: Cisco IOS XR Software for NCS 6000 Series Devices OSPF Packet Processing Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160914-iosxr
+ UPDATE: Cisco ACE30 Application Control Engine Module and Cisco ACE 4710 Application Control Engine Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160908-ace
+ Linux kernel 4.7.4, 4.4.21 released
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.7.4
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.4.21
+ PHP 7.0.11 Released
http://www.php.net/ChangeLog-7.php#7.0.11
+ UPDATE: JVNVU#97236594 glibc にバッファオーバーフローの脆弱性
http://jvn.jp/vu/JVNVU97236594/index.html
+ UPDATE: JVNVU#91445763 OpenSSL に複数の脆弱性
http://jvn.jp/vu/JVNVU91445763/index.html
+ UPDATE: JVNVU#95877131 OpenSSL に複数の脆弱性
http://jvn.jp/vu/JVNVU95877131/index.html
+ UPDATE: JVNVU#99125992 SSL/TLS の実装が輸出グレードの RSA 鍵を受け入れる問題 (FREAK 攻撃)
http://jvn.jp/vu/JVNVU99125992/index.html
+ UPDATE: JVNVU#93841436 複数の Apple 製品の脆弱性に対するアップデート
http://jvn.jp/vu/JVNVU93841436/index.html
+ PHP 7.0.10 Out-Of-Bounds Read in php_wddx_push_element of wddx.c
https://cxsecurity.com/issue/WLB-2016090114
+ PHP 7.0.10 Missing type check when unserializing SplArray
https://cxsecurity.com/issue/WLB-2016090113
+ PHP 7.0.10 SEH buffer overflow msgfmt_format_message
https://cxsecurity.com/issue/WLB-2016090112
+ PHP 7.0.10 Out of bound when verify signature of zip phar in phar_parse_zipfile
https://cxsecurity.com/issue/WLB-2016090111
+ PHP 7.0.10 Heap overflow in mysqlnd related to BIT fields
https://cxsecurity.com/issue/WLB-2016090110
+ libcurl Integer Overflow in Escape Functions May Let Users Execute Arbitrary Code on the Target System
http://www.securitytracker.com/id/1036813
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7167
ITpro EXPO 2016見どころ解説
激増するサイバー攻撃、我々はどう立ち向かうべきなのか
http://itpro.nikkeibp.co.jp/atcl/column/16/091500203/091500001/?ST=security?itp_list_theme
UPDATE: JVN#89379547 Apache Commons FileUpload におけるサービス運用妨害 (DoS) の脆弱性
http://jvn.jp/jp/JVN89379547/index.html
JVN#94779084 H2O における書式指定文字列に関する脆弱性
http://jvn.jp/jp/JVN94779084/index.html
JVN#18926672 Zend Framework における SQL インジェクションの脆弱性
http://jvn.jp/jp/JVN18926672/index.html
https://technet.microsoft.com/ja-jp/library/security/3174644
+ マイクロソフト セキュリティ アドバイザリ 3181759 ASP.NET Core のビュー コンポーネントの脆弱性により、特権が昇格される
https://technet.microsoft.com/ja-jp/library/security/3181759
+ Vim 8.0 released
https://groups.google.com/forum/#!topic/vim_announce/EKTuhjF3ET0
+ UPDATE: Cisco IOS XR Software for NCS 6000 Series Devices OSPF Packet Processing Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160914-iosxr
+ UPDATE: Cisco ACE30 Application Control Engine Module and Cisco ACE 4710 Application Control Engine Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160908-ace
+ Linux kernel 4.7.4, 4.4.21 released
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.7.4
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.4.21
+ PHP 7.0.11 Released
http://www.php.net/ChangeLog-7.php#7.0.11
+ UPDATE: JVNVU#97236594 glibc にバッファオーバーフローの脆弱性
http://jvn.jp/vu/JVNVU97236594/index.html
+ UPDATE: JVNVU#91445763 OpenSSL に複数の脆弱性
http://jvn.jp/vu/JVNVU91445763/index.html
+ UPDATE: JVNVU#95877131 OpenSSL に複数の脆弱性
http://jvn.jp/vu/JVNVU95877131/index.html
+ UPDATE: JVNVU#99125992 SSL/TLS の実装が輸出グレードの RSA 鍵を受け入れる問題 (FREAK 攻撃)
http://jvn.jp/vu/JVNVU99125992/index.html
+ UPDATE: JVNVU#93841436 複数の Apple 製品の脆弱性に対するアップデート
http://jvn.jp/vu/JVNVU93841436/index.html
+ PHP 7.0.10 Out-Of-Bounds Read in php_wddx_push_element of wddx.c
https://cxsecurity.com/issue/WLB-2016090114
+ PHP 7.0.10 Missing type check when unserializing SplArray
https://cxsecurity.com/issue/WLB-2016090113
+ PHP 7.0.10 SEH buffer overflow msgfmt_format_message
https://cxsecurity.com/issue/WLB-2016090112
+ PHP 7.0.10 Out of bound when verify signature of zip phar in phar_parse_zipfile
https://cxsecurity.com/issue/WLB-2016090111
+ PHP 7.0.10 Heap overflow in mysqlnd related to BIT fields
https://cxsecurity.com/issue/WLB-2016090110
+ libcurl Integer Overflow in Escape Functions May Let Users Execute Arbitrary Code on the Target System
http://www.securitytracker.com/id/1036813
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7167
ITpro EXPO 2016見どころ解説
激増するサイバー攻撃、我々はどう立ち向かうべきなのか
http://itpro.nikkeibp.co.jp/atcl/column/16/091500203/091500001/?ST=security?itp_list_theme
UPDATE: JVN#89379547 Apache Commons FileUpload におけるサービス運用妨害 (DoS) の脆弱性
http://jvn.jp/jp/JVN89379547/index.html
JVN#94779084 H2O における書式指定文字列に関する脆弱性
http://jvn.jp/jp/JVN94779084/index.html
JVN#18926672 Zend Framework における SQL インジェクションの脆弱性
http://jvn.jp/jp/JVN18926672/index.html
2016年9月15日木曜日
15日 木曜日、仏滅
+ 2016 年 9 月のマイクロソフト セキュリティ情報の概要
https://technet.microsoft.com/ja-jp/library/security/ms16-sep
+ MS16-104 - 緊急 Internet Explorer 用の累積的なセキュリティ更新プログラム (3183038)
https://technet.microsoft.com/library/security/MS16-104
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3247
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3291
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3292
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3295
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3297
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3324
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3325
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3351
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3353
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3375
+ MS16-105 - 緊急 Microsoft Edge 用の累積的なセキュリティ更新プログラム (3183043)
https://technet.microsoft.com/library/security/MS16-105
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3247
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3291
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3294
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3295
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3297
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3325
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3330
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3350
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3351
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3374
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3377
+ MS16-106 - 緊急 Microsoft Graphics コンポーネント用のセキュリティ更新プログラム (3185848)
https://technet.microsoft.com/library/security/MS16-106
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3348
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3349
+ MS16-107 - 緊急 Microsoft Office 用のセキュリティ更新プログラム (3185852)
https://technet.microsoft.com/library/security/MS16-107
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0137
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0141
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3357
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3358
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3359
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3360
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3361
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3362
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3363
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3364
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3365
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3381
+ MS16-108 - 緊急 Microsoft Exchange Server 用のセキュリティ更新プログラム (3185883)
https://technet.microsoft.com/library/security/MS16-108
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0138
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3378
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3379
+ MS16-109 - 重要 Silverlight 用のセキュリティ更新プログラム (3182373)
https://technet.microsoft.com/library/security/MS16-109
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3367
+ MS16-110 - 重要 Microsoft Windows 用のセキュリティ更新プログラム (3178467)
https://technet.microsoft.com/library/security/MS16-110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3346
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3352
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3368
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3369
+ MS16-111 - 重要 Windows カーネル用のセキュリティ更新プログラム (3186973)
https://technet.microsoft.com/library/security/MS16-111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3305
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3306
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3371
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3372
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3373
+ MS16-112 - 重要 Windows のロック画面用のセキュリティ更新プログラム (3178469)
https://technet.microsoft.com/library/security/MS16-112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3302
+ MS16-113 - 重要 Windows 保護カーネル モード用のセキュリティ更新プログラム (3185876)
https://technet.microsoft.com/library/security/MS16-113
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3344
+ MS16-114 - 重要 Windows SMBv1 サーバー用のセキュリティ更新プログラム (3185879)
https://technet.microsoft.com/library/security/MS16-114
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3345
+ MS16-115 - 重要 Microsoft Windows PDF ライブラリ用のセキュリティ更新プログラム (3188733)
https://technet.microsoft.com/library/security/MS16-115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3374
+ MS16-116 - 緊急 VBScript スクリプト エンジン用の OLE オートメーションのセキュリティ更新プログラム (3188724)
https://technet.microsoft.com/library/security/MS16-116
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3375
+ MS16-117 - 緊急 Adobe Flash Player のセキュリティ更新プログラム (3188128)
https://technet.microsoft.com/library/security/MS16-117
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4271
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4272
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4274
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4275
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4276
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4277
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4278
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4279
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4280
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4281
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4282
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4283
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4284
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4285
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4287
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6921
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6922
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6923
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6924
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6925
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6926
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6927
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6929
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6930
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6931
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6932
+ curl escape and unescape integer overflows
https://curl.haxx.se/docs/adv_20160914.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7167
+ RHSA-2016:1847 Important: kernel security, bug fix, and enhancement update
https://rhn.redhat.com/errata/RHSA-2016-1847.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3134
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4997
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4998
+ About the security content of watchOS 3
https://support.apple.com/ja-jp/HT207141
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4719
+ About the security content of Xcode 8
https://support.apple.com/ja-jp/HT207140
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4704
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4705
+ About the security content of iOS 10.0.1
https://support.apple.com/ja-jp/HT207145
+ About the security content of iOS 10
https://support.apple.com/ja-jp/HT207143
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4741
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4719
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4746
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4747
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4740
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4749
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4620
+ Google Chrome 53.0.2785.116 released
https://googlechromereleases.blogspot.jp/2016/09/stable-channel-update-for-desktop_14.html
+ Google Chrome 53.0.2785.113 released
https://googlechromereleases.blogspot.jp/2016/09/stable-channel-update-for-desktop_13.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5170
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5171
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5172
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5173
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5174
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5175
+ Zabbix 3.2.0 released
http://www.zabbix.com/rn3.2.0.php
+ APSB16-31 Security update available for Adobe AIR SDK & Compiler
https://helpx.adobe.com/security/products/air/apsb16-31.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6936
+ APSB16-29 Security updates available for Adobe Flash Player
https://helpx.adobe.com/security/products/flash-player/apsb16-29.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4271
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4272
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4274
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4275
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4276
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4277
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4278
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4279
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4280
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4281
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4282
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4283
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4284
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4285
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4287
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6921
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6922
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6923
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6924
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6925
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6926
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6927
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6929
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6930
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6931
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6932
+ APSB16-28 Security update available for Adobe Digital Editions
https://helpx.adobe.com/security/products/Digital-Editions/apsb16-28.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4256
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4257
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4258
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4259
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4260
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4261
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4262
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4263
+ VMware Workstation Player 12.5 released
http://pubs.vmware.com/Release_Notes/en/workstation/12player/player-125-release-notes.html?__utma=207178772.702043549.1440547077.1473897507.1473908525.223&__utmb=207178772.1.10.1473908525&__utmc=207178772&__utmx=-&__utmz=207178772.1440547077.1.1.utmcsr=my.vmware.com|utmccn=(referral)|utmcmd=referral|utmcct=/web/vmware/free&__utmv=-&__utmk=112311047
+ Cisco Web Security Appliance HTTP Load Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160914-wsa
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6407
+ Cisco WebEx Meetings Server Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160914-wms
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1483
+ Cisco WebEx Meetings Server Remote Command Execution Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160914-wem
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1482
+ Cisco Unified Computing System Command Line Interface Privilege Escalation Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160914-ucs
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6402
+ Cisco Fog Director for IOx Arbitrary File Write Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160914-ioxfd
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6405
+ Cisco IOS XR for NCS6000 Series Devices OSPF Packet Processing Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160914-iosxr
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1433
+ Cisco IOS and IOS XE Software Data in Motion Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160914-ios-xe
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6403
+ Cisco IOS and IOS XE Software IOx Local Manager Cross-Site Scripting Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160914-ios
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6404
+ Cisco Carrier Routing System IPv6 Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160914-crs
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6401
+ UPDATE: Cisco Products IPv6 Neighbor Discovery Crafted Packet Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160525-ipv6
+ curl 7.50.3 released
https://curl.haxx.se/changes.html#7_50_3
+ SA72515 libcURL Multiple Integer Overflow Denial of Service Vulnerabilities
https://secunia.com/advisories/72515/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7167
+ SA72509 VMware Workstation Multiple Vulnerabilities
https://secunia.com/advisories/72509/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7081
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7082
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7083
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7084
+ SA72567 VMware Tools Multiple NULL Pointer Dereference Vulnerabilities
https://secunia.com/advisories/72567/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7079
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7080
+ MySQL General Query Logging Function Lets Remote Authenticated Users Modify the 'my.cnf' File to Gain Elevated Privileges
http://www.securitytracker.com/id/1036769
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6662
VU#667480 AVer Information EH6108H+ hybrid DVR contains multiple vulnerabilities
https://www.kb.cert.org/vuls/id/667480
JVNDB-2016-000159 H2O における書式指定文字列に関する脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000159.html
JVNDB-2016-000158 Zend Framework における SQL インジェクションの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000158.html
JVNDB-2016-000157 CS-Cart 用アドオン「Twigmo」における PHP オブジェクトインジェクションの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000157.html
マカフィー、個人向けセキュリティ対策ソフトの2017年版を発表--クラウドを活用しゼロデイ攻撃を防御
http://itpro.nikkeibp.co.jp/atcl/news/16/091402690/?ST=security?itp_list_theme
NRIセキュア、成りすましによる不正アクセスを振る舞い検知するソフトを販売
http://itpro.nikkeibp.co.jp/atcl/news/16/091302668/?ST=security?itp_list_theme
2016年9月13日火曜日
13日 火曜日、友引
+ RHSA-2016:1850 Important: libarchive security update
https://rhn.redhat.com/errata/RHSA-2016-1850.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8920
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8921
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8932
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4809
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5418
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5844
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7166
+ RHSA-2016:1844 Important: libarchive security update
https://rhn.redhat.com/errata/RHSA-2016-1844.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8916
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8917
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8919
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8920
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8921
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8922
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8923
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8924
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8925
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8926
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8928
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8930
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8931
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8932
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8934
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1541
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4300
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4302
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4809
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5418
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5844
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6250
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7166
+ MySQL <= 5.7/5.6/5.5 Remote Root Code Execution / Privilege Escalation (0day)
https://cxsecurity.com/issue/WLB-2016090079
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6662
+ Oracle MySQL CVE-2016-6662 Remote Code Execution Vulnerability
http://www.securityfocus.com/bid/92912
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6662
+ Oracle MySQL CVE-2016-6663 Unspecified Security Vulnerability
http://www.securityfocus.com/bid/92911
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6663
https://rhn.redhat.com/errata/RHSA-2016-1850.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8920
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8921
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8932
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4809
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5418
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5844
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7166
+ RHSA-2016:1844 Important: libarchive security update
https://rhn.redhat.com/errata/RHSA-2016-1844.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8916
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8917
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8919
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8920
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8921
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8922
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8923
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8924
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8925
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8926
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8928
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8930
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8931
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8932
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8934
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1541
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4300
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4302
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4809
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5418
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5844
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6250
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7166
+ MySQL <= 5.7/5.6/5.5 Remote Root Code Execution / Privilege Escalation (0day)
https://cxsecurity.com/issue/WLB-2016090079
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6662
+ Oracle MySQL CVE-2016-6662 Remote Code Execution Vulnerability
http://www.securityfocus.com/bid/92912
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6662
+ Oracle MySQL CVE-2016-6663 Unspecified Security Vulnerability
http://www.securityfocus.com/bid/92911
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6663
2016年9月12日月曜日
12日 月曜日、先勝
+ Cisco ACE30 Application Control Engine Module and Cisco ACE 4710 Application Control Engine Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160908-ace
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6399
+ Linux kernel 3.14.79 released
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.14.79
+ SA72441 Hitachi Multiple Cosminexus / uCosminexus Products Java Information Disclosure Vulnerability
https://secunia.com/advisories/72441/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0887
+ SA72444 Hitachi Multiple Products Multiple Vulnerabilities
https://secunia.com/advisories/72444/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2105
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2106
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2108
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2109
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2177
+ HS16-024 Vulnerability in Cosminexus
http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS16-024/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0887
+ HS16-023 Multiple Vulnerabilities in Hitachi Web Server
http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS16-023/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0702
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2105
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2106
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2108
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2109
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2177
+ HS16-024 Cosminexusにおける問題
http://www.hitachi.co.jp/Prod/comp/soft1/security/info/vuls/HS16-024/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0887
+ HS16-023 Hitachi Web Serverにおける複数の脆弱性
http://www.hitachi.co.jp/Prod/comp/soft1/security/info/vuls/HS16-023/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0702
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2105
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2106
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2108
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2109
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2177
+ Wireshark QNX6 QNET, H.225, Catapult DCT2000, UMTS FP, and IPMI Trace Dissector Bugs Lets Remote Users Cause the Target Service to Crash
http://www.securitytracker.com/id/1036760
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7175
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7176
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7177
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7178
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7179
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7180
+ Vodafone Mobile Wifi Reset Admin Password
https://cxsecurity.com/issue/WLB-2016090070
+ Google Docs XSPA / SSRF
https://cxsecurity.com/issue/WLB-2016090068
+ Apple iCloud Desktop Client 5.2.1.0 Credential Disclosure
https://cxsecurity.com/issue/WLB-2016090066
+ Dropbox Desktop Client 9.4.49 Credential Disclosure
https://cxsecurity.com/issue/WLB-2016090064
+ Wireshark Multiple Denial of Service Vulnerabilities
http://www.securityfocus.com/bid/92889
UPDATE: JVNVU#94993132 Open Dental がインストール時にデフォルトの認証情報を設定する問題
http://jvn.jp/vu/JVNVU94993132/
2016年9月9日金曜日
9日 金曜日、仏滅
+ Incorrect reuse of client certificates
https://curl.haxx.se/docs/adv_20160907.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7141
+ Wireshark 2.0.6 released
https://www.wireshark.org/docs/relnotes/wireshark-2.0.6.html
+ UPDATE: Row Hammer Privilege Escalation Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20150309-rowhammer
+ Cisco ACE30 Application Control Engine Module and Cisco ACE 4710 Application Control Engine Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160908-ace
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6399
+ curl 7.50.2 released
https://curl.haxx.se/changes.html#7_50_2
+ PostgreSQL JDBC Driver 9.4.1210 released!
https://www.postgresql.org/about/news/1694/
https://jdbc.postgresql.org/documentation/changelog.html#version_9.4.1210
+ SA72440 Wireshark Multiple Denial of Service Vulnerabilities
https://secunia.com/advisories/72440/
+ SA72437 Zimbra Collaboration Server Multiple Vulnerabilities
https://secunia.com/advisories/72437/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4852
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3401
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3402
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3403
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3404
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3405
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3406
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3407
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3408
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3409
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3410
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3411
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3412
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3413
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3414
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3415
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3999
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4019
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5721
+ WinSCP DLL Hijacking Exploit (shcore.dll)
https://cxsecurity.com/issue/WLB-2016090050
ブロックチェーンは本当に世界を変えるのか
国際的な存在感が希薄すぎる日本のブロックチェーン業界
http://itpro.nikkeibp.co.jp/atcl/column/16/062400138/090100006/?ST=security?itp_list_theme
UPDATE: JVNVU#94423160 Dentsply Sirona CDR DICOM に認証情報がハードコードされている問題
http://jvn.jp/vu/JVNVU94423160/index.html
UPDATE: JVNVU#94993132 Open Dental がインストール時にデフォルトの認証情報を設定する問題
http://jvn.jp/vu/JVNVU94993132/index.html
JVNVU#97260486 Fortinet FortiWAN ロードバランサアプライアンスに複数の脆弱性
http://jvn.jp/vu/JVNVU97260486/index.html
JVNVU#91018225 DEXIS Imaging Suite 10 に認証情報がハードコードされている問題
http://jvn.jp/vu/JVNVU91018225/index.html
https://curl.haxx.se/docs/adv_20160907.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7141
+ Wireshark 2.0.6 released
https://www.wireshark.org/docs/relnotes/wireshark-2.0.6.html
+ UPDATE: Row Hammer Privilege Escalation Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20150309-rowhammer
+ Cisco ACE30 Application Control Engine Module and Cisco ACE 4710 Application Control Engine Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160908-ace
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6399
+ curl 7.50.2 released
https://curl.haxx.se/changes.html#7_50_2
+ PostgreSQL JDBC Driver 9.4.1210 released!
https://www.postgresql.org/about/news/1694/
https://jdbc.postgresql.org/documentation/changelog.html#version_9.4.1210
+ SA72440 Wireshark Multiple Denial of Service Vulnerabilities
https://secunia.com/advisories/72440/
+ SA72437 Zimbra Collaboration Server Multiple Vulnerabilities
https://secunia.com/advisories/72437/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4852
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3401
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3402
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3403
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3404
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3405
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3406
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3407
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3408
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3409
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3410
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3411
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3412
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3413
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3414
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3415
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3999
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4019
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5721
+ WinSCP DLL Hijacking Exploit (shcore.dll)
https://cxsecurity.com/issue/WLB-2016090050
ブロックチェーンは本当に世界を変えるのか
国際的な存在感が希薄すぎる日本のブロックチェーン業界
http://itpro.nikkeibp.co.jp/atcl/column/16/062400138/090100006/?ST=security?itp_list_theme
UPDATE: JVNVU#94423160 Dentsply Sirona CDR DICOM に認証情報がハードコードされている問題
http://jvn.jp/vu/JVNVU94423160/index.html
UPDATE: JVNVU#94993132 Open Dental がインストール時にデフォルトの認証情報を設定する問題
http://jvn.jp/vu/JVNVU94993132/index.html
JVNVU#97260486 Fortinet FortiWAN ロードバランサアプライアンスに複数の脆弱性
http://jvn.jp/vu/JVNVU97260486/index.html
JVNVU#91018225 DEXIS Imaging Suite 10 に認証情報がハードコードされている問題
http://jvn.jp/vu/JVNVU91018225/index.html
2016年9月8日木曜日
8日 木曜日、先負
+ Google Chrome 53.0.2785.101 released
https://googlechromereleases.blogspot.jp/2016/09/stable-channel-update-for-desktop.html
+ CESA-2016:1809 Important CentOS 7 thunderbird Security Update
http://lwn.net/Alerts/699655/
+ CESA-2016:1809 Important CentOS 5 thunderbird Security Update
http://lwn.net/Alerts/699653/
+ CESA-2016:1809 Important CentOS 6 thunderbird Security Update
http://lwn.net/Alerts/699654/
+ CESA-2016:1797 Moderate CentOS 7 ipa Security Update
http://lwn.net/Alerts/699652/
+ CESA-2016:1797 Moderate CentOS 6 ipa Security Update
http://lwn.net/Alerts/699651/
+ CESA-2016:1776 Important CentOS 7 java-1.6.0-openjdk Security Update
http://lwn.net/Alerts/698324/
+ CESA-2016:1776 Important CentOS 6 java-1.6.0-openjdk Security Update
http://lwn.net/Alerts/698323/
+ CESA-2016:1776 Important CentOS 5 java-1.6.0-openjdk Security Update
http://lwn.net/Alerts/698322/
+ Wireshark 2.2.0, 2.0.5 released
https://www.wireshark.org/docs/relnotes/wireshark-2.2.0.html
https://www.wireshark.org/docs/relnotes/wireshark-2.0.5.html
+ Cisco Firepower Management Center and FireSIGHT System Software Malware Bypass Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160907-fsss1
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6396
+ Cisco Firepower Management Center and FireSIGHT System Software Cross-Site Scripting Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160907-fsss
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6395
+ Cisco Firepower Management Center and FireSIGHT System Software Session Fixation Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160907-fsmc
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6394
+ UPDATE: Cisco Wireless LAN Controller TSM SNMP Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-wlc-1
+ UPDATE: Cisco Wireless LAN Controller wIPS Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-wlc-2
+ Linux kernel 4.7.3, 4.4.20, 3.14.78, 3.12.63 released
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.7.3
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.4.20
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.14.78
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.12.63
+ Samba 4.5.0 Available for Download
https://www.samba.org/samba/history/samba-4.5.0.html
+ SA72413 Google Nexus Multiple Vulnerabilities
https://secunia.com/advisories/72413/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3861
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3862
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3863
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3878
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3879
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3880
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3881
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3886
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3899
+ SA72372 cURL / libcURL TLS Client Certificate Reuse Security Bypass Vulnerability
https://secunia.com/advisories/72372/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7141
+ Apache Tomcat 8.5.5, 8.0.37 released
http://tomcat.apache.org/tomcat-8.5-doc/changelog.html#Tomcat_8.5.5_(markt)
http://tomcat.apache.org/tomcat-8.0-doc/changelog.html#Tomcat_8.0.36_(markt)
+ UPDATE: JVNVU#92267426 複数の Apple 製品の脆弱性に対するアップデート
http://jvn.jp/vu/JVNVU92267426/
+ glibc getaddrinfo Stack Buffer Overflow
https://cxsecurity.com/issue/WLB-2016090038
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7547
+ Android 6.0.0 MDA89E / 6.0.1 MMB29V OEM Panic
https://cxsecurity.com/issue/WLB-2016090037
+ MySQL 5.5.45 (64bit) - Local Credentials Disclosure
https://cxsecurity.com/issue/WLB-2016090026
+ cURL/libcurl Certificate Reuse Bug Lets Remote Users Bypass Security Restrictions on the Target System
http://www.securitytracker.com/id/1036739
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5420
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7141
+ cURL/libcURL CVE-2016-7141 Certificate Validation Security Bypass Vulnerability
http://www.securityfocus.com/bid/92754
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7141
VU#282991 DEXIS Imaging Suite 10 contains hard-coded credentials
https://www.kb.cert.org/vuls/id/282991
VU#548399 Dentsply Sirona CDR DICOM contains multiple hard-coded credentials
https://www.kb.cert.org/vuls/id/548399
VU#619767 Open Dental installs with default database credentials
https://www.kb.cert.org/vuls/id/619767
VU#724487 Fortinet FortiWAN load balancer appliance contains multiple vulnerabilities
https://www.kb.cert.org/vuls/id/724487
JVNDB-2016-000156 ADOdb におけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000156.html
JVNVU#94423160 Dentsply Sirona CDR DICOM に認証情報がハードコードされている問題
http://jvn.jp/vu/JVNVU94423160/index.html
JVNVU#94993132 Open Dental に認証情報がハードコードされている問題
http://jvn.jp/vu/JVNVU94993132/index.html
JVNVU#97260486 Fortinet FortiWAN ロードバランサアプライアンスに複数の脆弱性
http://jvn.jp/vu/JVNVU97260486/index.html
辻伸弘の裏読みセキュリティ事件簿
なぜ情報が少ない!? 大学を狙った攻撃を調査
http://itpro.nikkeibp.co.jp/atcl/column/16/012900025/090200015/?ST=security?itp_list_theme
携帯キャリア各社、10月からスパム送信者の情報を相互提供
http://itpro.nikkeibp.co.jp/atcl/news/16/090702609/?ST=security?itp_list_theme
「セキュリティ意識が低いCEOはあり得ない」、AWSのベンチャー向けイベントで議論
http://itpro.nikkeibp.co.jp/atcl/column/14/346926/090500624/?ST=security?itp_list_theme
辻伸弘の裏読みセキュリティ事件簿
被害タレントに専門家が指南 安全なパスワード管理法はこれだ!
http://itpro.nikkeibp.co.jp/atcl/column/16/012900025/042000013/?ST=security?itp_list_theme
仏ジェムアルト、自動車メーカーや製造業向けIoTセキュリティ製品戦略を発表
http://itpro.nikkeibp.co.jp/atcl/news/16/090602596/?ST=security?itp_list_theme
https://googlechromereleases.blogspot.jp/2016/09/stable-channel-update-for-desktop.html
+ CESA-2016:1809 Important CentOS 7 thunderbird Security Update
http://lwn.net/Alerts/699655/
+ CESA-2016:1809 Important CentOS 5 thunderbird Security Update
http://lwn.net/Alerts/699653/
+ CESA-2016:1809 Important CentOS 6 thunderbird Security Update
http://lwn.net/Alerts/699654/
+ CESA-2016:1797 Moderate CentOS 7 ipa Security Update
http://lwn.net/Alerts/699652/
+ CESA-2016:1797 Moderate CentOS 6 ipa Security Update
http://lwn.net/Alerts/699651/
+ CESA-2016:1776 Important CentOS 7 java-1.6.0-openjdk Security Update
http://lwn.net/Alerts/698324/
+ CESA-2016:1776 Important CentOS 6 java-1.6.0-openjdk Security Update
http://lwn.net/Alerts/698323/
+ CESA-2016:1776 Important CentOS 5 java-1.6.0-openjdk Security Update
http://lwn.net/Alerts/698322/
+ Wireshark 2.2.0, 2.0.5 released
https://www.wireshark.org/docs/relnotes/wireshark-2.2.0.html
https://www.wireshark.org/docs/relnotes/wireshark-2.0.5.html
+ Cisco Firepower Management Center and FireSIGHT System Software Malware Bypass Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160907-fsss1
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6396
+ Cisco Firepower Management Center and FireSIGHT System Software Cross-Site Scripting Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160907-fsss
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6395
+ Cisco Firepower Management Center and FireSIGHT System Software Session Fixation Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160907-fsmc
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6394
+ UPDATE: Cisco Wireless LAN Controller TSM SNMP Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-wlc-1
+ UPDATE: Cisco Wireless LAN Controller wIPS Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-wlc-2
+ Linux kernel 4.7.3, 4.4.20, 3.14.78, 3.12.63 released
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.7.3
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.4.20
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.14.78
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.12.63
+ Samba 4.5.0 Available for Download
https://www.samba.org/samba/history/samba-4.5.0.html
+ SA72413 Google Nexus Multiple Vulnerabilities
https://secunia.com/advisories/72413/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3861
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3862
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3863
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3878
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3879
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3880
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3881
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3886
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3899
+ SA72372 cURL / libcURL TLS Client Certificate Reuse Security Bypass Vulnerability
https://secunia.com/advisories/72372/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7141
+ Apache Tomcat 8.5.5, 8.0.37 released
http://tomcat.apache.org/tomcat-8.5-doc/changelog.html#Tomcat_8.5.5_(markt)
http://tomcat.apache.org/tomcat-8.0-doc/changelog.html#Tomcat_8.0.36_(markt)
+ UPDATE: JVNVU#92267426 複数の Apple 製品の脆弱性に対するアップデート
http://jvn.jp/vu/JVNVU92267426/
+ glibc getaddrinfo Stack Buffer Overflow
https://cxsecurity.com/issue/WLB-2016090038
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7547
+ Android 6.0.0 MDA89E / 6.0.1 MMB29V OEM Panic
https://cxsecurity.com/issue/WLB-2016090037
+ MySQL 5.5.45 (64bit) - Local Credentials Disclosure
https://cxsecurity.com/issue/WLB-2016090026
+ cURL/libcurl Certificate Reuse Bug Lets Remote Users Bypass Security Restrictions on the Target System
http://www.securitytracker.com/id/1036739
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5420
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7141
+ cURL/libcURL CVE-2016-7141 Certificate Validation Security Bypass Vulnerability
http://www.securityfocus.com/bid/92754
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7141
VU#282991 DEXIS Imaging Suite 10 contains hard-coded credentials
https://www.kb.cert.org/vuls/id/282991
VU#548399 Dentsply Sirona CDR DICOM contains multiple hard-coded credentials
https://www.kb.cert.org/vuls/id/548399
VU#619767 Open Dental installs with default database credentials
https://www.kb.cert.org/vuls/id/619767
VU#724487 Fortinet FortiWAN load balancer appliance contains multiple vulnerabilities
https://www.kb.cert.org/vuls/id/724487
JVNDB-2016-000156 ADOdb におけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000156.html
JVNVU#94423160 Dentsply Sirona CDR DICOM に認証情報がハードコードされている問題
http://jvn.jp/vu/JVNVU94423160/index.html
JVNVU#94993132 Open Dental に認証情報がハードコードされている問題
http://jvn.jp/vu/JVNVU94993132/index.html
JVNVU#97260486 Fortinet FortiWAN ロードバランサアプライアンスに複数の脆弱性
http://jvn.jp/vu/JVNVU97260486/index.html
辻伸弘の裏読みセキュリティ事件簿
なぜ情報が少ない!? 大学を狙った攻撃を調査
http://itpro.nikkeibp.co.jp/atcl/column/16/012900025/090200015/?ST=security?itp_list_theme
携帯キャリア各社、10月からスパム送信者の情報を相互提供
http://itpro.nikkeibp.co.jp/atcl/news/16/090702609/?ST=security?itp_list_theme
「セキュリティ意識が低いCEOはあり得ない」、AWSのベンチャー向けイベントで議論
http://itpro.nikkeibp.co.jp/atcl/column/14/346926/090500624/?ST=security?itp_list_theme
辻伸弘の裏読みセキュリティ事件簿
被害タレントに専門家が指南 安全なパスワード管理法はこれだ!
http://itpro.nikkeibp.co.jp/atcl/column/16/012900025/042000013/?ST=security?itp_list_theme
仏ジェムアルト、自動車メーカーや製造業向けIoTセキュリティ製品戦略を発表
http://itpro.nikkeibp.co.jp/atcl/news/16/090602596/?ST=security?itp_list_theme
2016年9月6日火曜日
Kali Linux 2016.2 INSTALL MEMO
Kali Linux 2016.2 がリリースされたので、インストールしてみた。
https://www.kali.org/
1) ISOイメージからブートすると、「Boot menu」が表示されるので、"Graphical Install" を選択する。
2) 「Select a language」 画面が表示されるので、「Japanese - 日本語」を選択して、[Continue] ボタンを押す。
3) 警告画面が表示されるので、「はい」を選択して、[続ける] ボタンを押す。
4) 「場所の選択」画面が表示されるので、「日本」を選択して、[続ける] ボタンを押す。
5) 「キーボートの選択」画面が表示されるので、「日本語」を選択して、[続ける] ボタンを押す。
6) コンポーネントのインストールが始まる。
7) ネットワークの設定が始まる。
8) 「ネットワークの設定」画面が表示されるので、ホスト名を入力して、[続ける] ボタンを押す。
9) 引き続き、ドメイン名を入力して、[続ける] ボタンを押す。
10) 「ユーザとパスワードのセットアップ」画面が表示されるので、root のパスワードを入力して、[続ける] ボタンを押す。
11) ネットワーク時刻サーバと同期を始める。接続できないなら、[キャンセル] ボタンを押す。
12) 「ディスクのパーティショニング」画面が表示されるので、「ガイド-ディスク全体を使う」を選択して、[続けるボタンを押す。
13) ディスクを選択して、[続ける] ボタンを押す。
14) 「すべてのファイルを1つのパーティションに…」を選択した、[続けるボタンを押す。
15) 設定内容を確認して、「パーティショニングの終了とディスクへの変更の書き込み」を選択して、[続けるボタンを押す。
16) 「はい」を選択して、[続けるボタンを押す。
17) システムのインストールが始まる。
18) 「パッケージマネージャの設定」画面が表示さえるので、「はい」を選択して、[続けるボタンを押す。
19) パッケージの取得とインストールが始まる。
20) 「ハードディスクへの GRUB ブートローダのインストール」画面が表示されるので、「はい」を選択して、[続けるボタンを押す。
21) インストールするデバイスを選択して、[続けるボタンを押す。
22) GRUB ブートローダのインストールが始まる。
23) インストールの終了へと進む。
24) 「インストールの完了」画面が表示されるので、[続けるボタンを押す。
25) 最後の処理が始まる。
26) 再起動してしばらくすると、ログイン画面が表示されるので、ログインする。
27) デスクトップが表示される。
Enjoy !!
https://www.kali.org/
1) ISOイメージからブートすると、「Boot menu」が表示されるので、"Graphical Install" を選択する。
2) 「Select a language」 画面が表示されるので、「Japanese - 日本語」を選択して、[Continue] ボタンを押す。
3) 警告画面が表示されるので、「はい」を選択して、[続ける] ボタンを押す。
4) 「場所の選択」画面が表示されるので、「日本」を選択して、[続ける] ボタンを押す。
5) 「キーボートの選択」画面が表示されるので、「日本語」を選択して、[続ける] ボタンを押す。
6) コンポーネントのインストールが始まる。
7) ネットワークの設定が始まる。
8) 「ネットワークの設定」画面が表示されるので、ホスト名を入力して、[続ける] ボタンを押す。
9) 引き続き、ドメイン名を入力して、[続ける] ボタンを押す。
10) 「ユーザとパスワードのセットアップ」画面が表示されるので、root のパスワードを入力して、[続ける] ボタンを押す。
11) ネットワーク時刻サーバと同期を始める。接続できないなら、[キャンセル] ボタンを押す。
12) 「ディスクのパーティショニング」画面が表示されるので、「ガイド-ディスク全体を使う」を選択して、[続けるボタンを押す。
13) ディスクを選択して、[続ける] ボタンを押す。
14) 「すべてのファイルを1つのパーティションに…」を選択した、[続けるボタンを押す。
15) 設定内容を確認して、「パーティショニングの終了とディスクへの変更の書き込み」を選択して、[続けるボタンを押す。
16) 「はい」を選択して、[続けるボタンを押す。
17) システムのインストールが始まる。
18) 「パッケージマネージャの設定」画面が表示さえるので、「はい」を選択して、[続けるボタンを押す。
19) パッケージの取得とインストールが始まる。
20) 「ハードディスクへの GRUB ブートローダのインストール」画面が表示されるので、「はい」を選択して、[続けるボタンを押す。
21) インストールするデバイスを選択して、[続けるボタンを押す。
22) GRUB ブートローダのインストールが始まる。
23) インストールの終了へと進む。
24) 「インストールの完了」画面が表示されるので、[続けるボタンを押す。
25) 最後の処理が始まる。
26) 再起動してしばらくすると、ログイン画面が表示されるので、ログインする。
27) デスクトップが表示される。
Enjoy !!
6日 火曜日、先勝
+ MantisBT 1.3.1, 1.2.20 Released
https://www.mantisbt.org/issues/changelog_page.php?version=1.3.1
https://www.mantisbt.org/issues/changelog_page.php?version=1.2.20
+ RHSA-2016:1809 Important: thunderbird security update
https://rhn.redhat.com/errata/RHSA-2016-1809.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2836
+ Linux kernel 4.1.32, 3.18.41 released
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.1.32
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.18.41
+ UPDATE: Oracle Solaris Third Party Bulletin - July 2016
http://www.oracle.com/technetwork/topics/security/bulletinjul2016-3090568.html
+ SA72414 Linux Kernel "tcp_check_send_head()" Use-After-Free Vulnerability
https://secunia.com/advisories/72414/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6828
+ SA72411 Linux Kernel "ioctl_send_fib()" Double Fetch Vulnerability
https://secunia.com/advisories/72411/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6480
+ libpng 1.6.25 released
http://www.libpng.org/pub/png/src/libpng-1.6.25-README.txt
+ MySQL 5.7.15, 5.6.33, 5.5.52 released
http://dev.mysql.com/doc/relnotes/mysql/5.7/en/news-5-7-15.html
http://dev.mysql.com/doc/relnotes/mysql/5.6/en/news-5-6-33.html
http://dev.mysql.com/doc/relnotes/mysql/5.5/en/news-5-5-52.html
+ PHP 7.0.9 __wakeup() in Deserialization
https://cxsecurity.com/issue/WLB-2016090023
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7124
+ PHP 7.0.9 Session Data Injection Vulnerability
https://cxsecurity.com/issue/WLB-2016090022
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7125
記者の眼
世界はランサムウエアに屈するのか
http://itpro.nikkeibp.co.jp/atcl/watcher/14/334361/090200654/?ST=security
辻伸弘の裏読みセキュリティ事件簿
米軍基地と間違えられた?岩国の病院被害を調査
http://itpro.nikkeibp.co.jp/atcl/column/16/012900025/042000012/?ST=security
https://www.mantisbt.org/issues/changelog_page.php?version=1.3.1
https://www.mantisbt.org/issues/changelog_page.php?version=1.2.20
+ RHSA-2016:1809 Important: thunderbird security update
https://rhn.redhat.com/errata/RHSA-2016-1809.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2836
+ Linux kernel 4.1.32, 3.18.41 released
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.1.32
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.18.41
+ UPDATE: Oracle Solaris Third Party Bulletin - July 2016
http://www.oracle.com/technetwork/topics/security/bulletinjul2016-3090568.html
+ SA72414 Linux Kernel "tcp_check_send_head()" Use-After-Free Vulnerability
https://secunia.com/advisories/72414/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6828
+ SA72411 Linux Kernel "ioctl_send_fib()" Double Fetch Vulnerability
https://secunia.com/advisories/72411/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6480
+ libpng 1.6.25 released
http://www.libpng.org/pub/png/src/libpng-1.6.25-README.txt
+ MySQL 5.7.15, 5.6.33, 5.5.52 released
http://dev.mysql.com/doc/relnotes/mysql/5.7/en/news-5-7-15.html
http://dev.mysql.com/doc/relnotes/mysql/5.6/en/news-5-6-33.html
http://dev.mysql.com/doc/relnotes/mysql/5.5/en/news-5-5-52.html
+ PHP 7.0.9 __wakeup() in Deserialization
https://cxsecurity.com/issue/WLB-2016090023
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7124
+ PHP 7.0.9 Session Data Injection Vulnerability
https://cxsecurity.com/issue/WLB-2016090022
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7125
記者の眼
世界はランサムウエアに屈するのか
http://itpro.nikkeibp.co.jp/atcl/watcher/14/334361/090200654/?ST=security
辻伸弘の裏読みセキュリティ事件簿
米軍基地と間違えられた?岩国の病院被害を調査
http://itpro.nikkeibp.co.jp/atcl/column/16/012900025/042000012/?ST=security
2016年9月5日月曜日
5日 月曜日、赤口
+ About the security content of Security Update 2016-001 El Capitan and Security Update 2016-005 Yosemite
https://support.apple.com/ja-jp/HT207130
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4655
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4656
+ About the security content of Safari 9.1.3
https://support.apple.com/ja-jp/HT207131
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4657
+ UPDATE: Cisco IOS Software Point-to-Point Tunneling Protocol Server Information Disclosure Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160902-ios
+ UPDATE: Cisco Wireless LAN Controller TSM SNMP Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-wlc-1
+ SA72371 Mozilla Thunderbird Multiple Vulnerabilities
https://secunia.com/advisories/72371/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2835
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2836
+ JVNVU#92267426 複数の Apple 製品の脆弱性に対するアップデート
http://jvn.jp/vu/JVNVU92267426/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4654
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4655
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4656
+ UPDATE: JVNVU#90289707 プロキシ自動設定ファイル (proxy.pac) から HTTPS URL に含まれる情報を取得できる問題
http://jvn.jp/vu/JVNVU90289707/
セキュリティ被害を減らす秘策
http://itpro.nikkeibp.co.jp/atcl/watcher/14/334361/083100652/?ST=security
辻伸弘の裏読みセキュリティ事件簿
注目のランサムウエアに感染 身代金を払ってはいけないのか?
http://itpro.nikkeibp.co.jp/atcl/column/16/012900025/031700010/?ST=security
大日本印刷、個人番号カードで本人確認ができるマルチカードスキャナーを発売
http://itpro.nikkeibp.co.jp/atcl/news/16/090202564/?ST=security
チェックポイント、サンドボックスと連携するWebプラグイン型マルウエア対策を発表
http://itpro.nikkeibp.co.jp/atcl/news/16/090202563/?ST=security
https://support.apple.com/ja-jp/HT207130
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4655
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4656
+ About the security content of Safari 9.1.3
https://support.apple.com/ja-jp/HT207131
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4657
+ UPDATE: Cisco IOS Software Point-to-Point Tunneling Protocol Server Information Disclosure Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160902-ios
+ UPDATE: Cisco Wireless LAN Controller TSM SNMP Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-wlc-1
+ SA72371 Mozilla Thunderbird Multiple Vulnerabilities
https://secunia.com/advisories/72371/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2835
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2836
+ JVNVU#92267426 複数の Apple 製品の脆弱性に対するアップデート
http://jvn.jp/vu/JVNVU92267426/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4654
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4655
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4656
+ UPDATE: JVNVU#90289707 プロキシ自動設定ファイル (proxy.pac) から HTTPS URL に含まれる情報を取得できる問題
http://jvn.jp/vu/JVNVU90289707/
セキュリティ被害を減らす秘策
http://itpro.nikkeibp.co.jp/atcl/watcher/14/334361/083100652/?ST=security
辻伸弘の裏読みセキュリティ事件簿
注目のランサムウエアに感染 身代金を払ってはいけないのか?
http://itpro.nikkeibp.co.jp/atcl/column/16/012900025/031700010/?ST=security
大日本印刷、個人番号カードで本人確認ができるマルチカードスキャナーを発売
http://itpro.nikkeibp.co.jp/atcl/news/16/090202564/?ST=security
チェックポイント、サンドボックスと連携するWebプラグイン型マルウエア対策を発表
http://itpro.nikkeibp.co.jp/atcl/news/16/090202563/?ST=security
2016年9月2日金曜日
2日 金曜日、先負
+ RHSA-2016:1797 Moderate: ipa security update
https://rhn.redhat.com/errata/RHSA-2016-1797.html
CVE-2016-5404
+ Red Hat Enterprise Linux 7.3 Beta released
https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/7-Beta/html/7.3_Release_Notes/index.html
+ UPDATE: APSB16-30 Security Update: Hotfixes available for ColdFusion
https://helpx.adobe.com/security/products/coldfusion/apsb16-30.html
PostgreSQL 9.6 RC 1 Released
https://www.postgresql.org/about/news/1693/
PHP 7.1.0 Release Candidate 1 Released
http://php.net/archive/2016.php#id2016-09-01-1
https://rhn.redhat.com/errata/RHSA-2016-1797.html
CVE-2016-5404
+ Red Hat Enterprise Linux 7.3 Beta released
https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/7-Beta/html/7.3_Release_Notes/index.html
+ UPDATE: APSB16-30 Security Update: Hotfixes available for ColdFusion
https://helpx.adobe.com/security/products/coldfusion/apsb16-30.html
PostgreSQL 9.6 RC 1 Released
https://www.postgresql.org/about/news/1693/
PHP 7.1.0 Release Candidate 1 Released
http://php.net/archive/2016.php#id2016-09-01-1
2016年9月1日木曜日
1日 木曜日、友引
+ Google Chrome 53.0.2785.89 released
http://googlechromereleases.blogspot.jp/2016/08/stable-channel-update-for-desktop_31.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5147
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5148
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5149
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5150
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5151
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5152
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5153
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5154
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5155
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5156
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5157
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5158
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5159
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5161
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5162
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5163
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5164
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5165
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5166
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5160
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5167
+ Mozilla Thunderbird 45.3.0 released
https://www.mozilla.org/en-US/thunderbird/45.3.0/releasenotes/
+ Wireshark 2.0.5, 1.12.13 released
https://www.wireshark.org/docs/relnotes/wireshark-2.0.5.html
https://www.wireshark.org/docs/relnotes/wireshark-1.12.13.html
+ Cisco Wireless LAN Controller wIPS Denial of Service Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-wlc-2
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6376
+ Cisco Wireless LAN Controller TSM SNMP Denial of Service Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-wlc-1
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6375
+ Cisco WebEx Meetings Player Denial of Service Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-webex
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1415
+ Cisco Virtual Media Packager PAM API Unauthorized Access Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-vmp
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6377
+ Cisco Small Business 220 Series Smart Plus Switches SNMP Unauthorized Access Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-sps3
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1473
+ Cisco Small Business 220 Series Smart Plus Switches Web Interface Denial of Service Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-sps2
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1472
+ Cisco Small Business 220 Series Smart Plus Switches Web Interface Cross-Site Scripting Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-sps1
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1471
+ Cisco Small Business 220 Series Smart Plus Switches Web Interface Cross-Site Request Forgery Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-sps
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1470
+ Cisco Small Business SPA3x/5x Series Denial of Service Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-spa
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1469
+ Cisco WebEx Meetings Player Arbitrary Code Execution Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-meetings-player
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1464
+ Cisco Hosted Collaboration Mediation Fulfillment Directory Traversal File System Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-hcmf
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6371
+ Cisco Hosted Collaboration Mediation Fulfillment Authenticated Directory Traversal Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-hcm
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6370
+ SA72310 Hitachi Multiple Cosminexus / uCosminexus Products File Upload Request Handling Denial of Service Vulnerability
https://secunia.com/advisories/72310/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3092
+ SA72338 McAfee ePolicy Orchestrator Oracle Java Multiple Vulnerabilities
https://secunia.com/advisories/72338/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3485
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3500
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3508
+ HS16-022 DoS Vulnerability in Cosminexus
http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS16-022/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3092
+ HS16-021 Information Disclosure Vulnerability in Hitachi Automation Director and JP1/Automatic Operation
http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS16-021/index.html
+ HS16-022 CosminexusにおけるDoS脆弱性
http://www.hitachi.co.jp/Prod/comp/soft1/security/info/vuls/HS16-022/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3092
+ HS16-021 Hitachi Automation Director, JP1/Automatic Operationにおける情報露出の脆弱性
http://www.hitachi.co.jp/Prod/comp/soft1/security/info/vuls/HS16-021/index.html
+ UPDATE: JVNVU#91485132 CGI ウェブサーバがヘッダ Proxy の値を環境変数 HTTP_PROXY に設定する脆弱性
http://jvn.jp/vu/JVNVU91485132/index.html
+ Linux Kernel 'fs/fcntl.c' Local Denial of Service Vulnerability
http://www.securityfocus.com/bid/92697
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7118
JVNDB-2016-000154 有限会社AKABEi SOFT2 製の複数のゲーム製品における OS コマンドインジェクションの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000154.html
サイバーインテリジェンスの探し方
サイバーインテリジェンスのためにネットニュースを整理
http://itpro.nikkeibp.co.jp/atcl/column/16/081200173/082500008/?ST=security
ランサムウエアへの対策を強化、トレンドマイクロがウイルスバスター新製品を発表
http://itpro.nikkeibp.co.jp/atcl/news/16/083102539/?ST=security
http://googlechromereleases.blogspot.jp/2016/08/stable-channel-update-for-desktop_31.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5147
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5148
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5149
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5150
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5151
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5152
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5153
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5154
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5155
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5156
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5157
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5158
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5159
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5161
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5162
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5163
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5164
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5165
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5166
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5160
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5167
+ Mozilla Thunderbird 45.3.0 released
https://www.mozilla.org/en-US/thunderbird/45.3.0/releasenotes/
+ Wireshark 2.0.5, 1.12.13 released
https://www.wireshark.org/docs/relnotes/wireshark-2.0.5.html
https://www.wireshark.org/docs/relnotes/wireshark-1.12.13.html
+ Cisco Wireless LAN Controller wIPS Denial of Service Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-wlc-2
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6376
+ Cisco Wireless LAN Controller TSM SNMP Denial of Service Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-wlc-1
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6375
+ Cisco WebEx Meetings Player Denial of Service Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-webex
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1415
+ Cisco Virtual Media Packager PAM API Unauthorized Access Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-vmp
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6377
+ Cisco Small Business 220 Series Smart Plus Switches SNMP Unauthorized Access Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-sps3
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1473
+ Cisco Small Business 220 Series Smart Plus Switches Web Interface Denial of Service Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-sps2
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1472
+ Cisco Small Business 220 Series Smart Plus Switches Web Interface Cross-Site Scripting Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-sps1
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1471
+ Cisco Small Business 220 Series Smart Plus Switches Web Interface Cross-Site Request Forgery Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-sps
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1470
+ Cisco Small Business SPA3x/5x Series Denial of Service Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-spa
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1469
+ Cisco WebEx Meetings Player Arbitrary Code Execution Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-meetings-player
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1464
+ Cisco Hosted Collaboration Mediation Fulfillment Directory Traversal File System Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-hcmf
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6371
+ Cisco Hosted Collaboration Mediation Fulfillment Authenticated Directory Traversal Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160831-hcm
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-6370
+ SA72310 Hitachi Multiple Cosminexus / uCosminexus Products File Upload Request Handling Denial of Service Vulnerability
https://secunia.com/advisories/72310/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3092
+ SA72338 McAfee ePolicy Orchestrator Oracle Java Multiple Vulnerabilities
https://secunia.com/advisories/72338/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3485
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3500
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3508
+ HS16-022 DoS Vulnerability in Cosminexus
http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS16-022/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3092
+ HS16-021 Information Disclosure Vulnerability in Hitachi Automation Director and JP1/Automatic Operation
http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS16-021/index.html
+ HS16-022 CosminexusにおけるDoS脆弱性
http://www.hitachi.co.jp/Prod/comp/soft1/security/info/vuls/HS16-022/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3092
+ HS16-021 Hitachi Automation Director, JP1/Automatic Operationにおける情報露出の脆弱性
http://www.hitachi.co.jp/Prod/comp/soft1/security/info/vuls/HS16-021/index.html
+ UPDATE: JVNVU#91485132 CGI ウェブサーバがヘッダ Proxy の値を環境変数 HTTP_PROXY に設定する脆弱性
http://jvn.jp/vu/JVNVU91485132/index.html
+ Linux Kernel 'fs/fcntl.c' Local Denial of Service Vulnerability
http://www.securityfocus.com/bid/92697
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7118
JVNDB-2016-000154 有限会社AKABEi SOFT2 製の複数のゲーム製品における OS コマンドインジェクションの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000154.html
サイバーインテリジェンスの探し方
サイバーインテリジェンスのためにネットニュースを整理
http://itpro.nikkeibp.co.jp/atcl/column/16/081200173/082500008/?ST=security
ランサムウエアへの対策を強化、トレンドマイクロがウイルスバスター新製品を発表
http://itpro.nikkeibp.co.jp/atcl/news/16/083102539/?ST=security
登録:
投稿 (Atom)