+ CESA-2013:1182 Important CentOS 6 389-ds-base Update
http://lwn.net/Alerts/565263/
+ CESA-2013:1173 Important CentOS 6 kernel Update
http://lwn.net/Alerts/565264/
+ HPSBNS02920 rev.1 - HP NonStop Servers running Java 6.0, Multiple Remote Vulnerabilities affecting Confidentiality, Integrity and Availability
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03909126-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0786
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0788
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0802
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0814
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0815
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0817
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0862
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0863
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0864
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0865
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0866
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0867
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0868
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0869
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0872
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0873
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3389
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3516
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3521
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3544
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3545
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3546
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3547
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3548
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3549
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3550
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3551
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3552
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3553
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3554
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3556
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3557
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3558
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3560
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3561
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3563
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-5035
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0497
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0498
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0499
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0500
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0501
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0502
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0503
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0504
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0505
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0506
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0507
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0547
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0551
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1531
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1532
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1533
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1541
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1711
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1713
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1716
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1717
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1718
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1719
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1720
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1721
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1722
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1723
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1724
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1725
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-3143
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-3159
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-3213
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-3216
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-3342
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-4416
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5068
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5069
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5071
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5072
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5073
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5075
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5077
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5079
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5081
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5083
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5084
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5085
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5086
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5087
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5089
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0351
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0409
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0419
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0423
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0424
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0425
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0426
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0427
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0428
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0429
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0432
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0433
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0434
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0435
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0438
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0440
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0441
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0442
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0443
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0445
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0446
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0450
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0809
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1473
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1475
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1476
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1478
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1480
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1481
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1493
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1537
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1571
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2424
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2457
+ SQL Select 1.3.0.32 released
http://www.postgresql.org/about/news/1479/
+ REMOTE: HP LoadRunner lrFileIOService ActiveX Remote Code Execution
http://www.exploit-db.com/exploits/27939
http://cxsecurity.com/issue/WLB-2013080229
+ REMOTE: Firefox XMLSerializer Use After Free
http://www.exploit-db.com/exploits/27940
http://cxsecurity.com/issue/WLB-2013080230
+ REMOTE: SPIP connect Parameter PHP Injection
http://www.exploit-db.com/exploits/27941
+ REMOTE: Oracle Java ByteComponentRaster.verify() Memory Corruption
http://www.exploit-db.com/exploits/27943
+ LOCAL: VMWare Setuid vmware-mount Unsafe popen(3)
http://www.exploit-db.com/exploits/27938
http://cxsecurity.com/issue/WLB-2013080228
+ LOCAL: Mac OS X Sudo Password Bypass
http://www.exploit-db.com/exploits/27944
+ Google Docs Information Disclosure
http://cxsecurity.com/issue/WLB-2013080224
+ Linux Kernel CVE-2013-2899 NULL Pointer Dereference Denial of Service Vulnerability
http://www.securityfocus.com/bid/62046
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2899
+ Linux Kernel CVE-2013-2897 Heap Buffer Overflow Vulnerability
http://www.securityfocus.com/bid/62044
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2897
トレンドマイクロアカウントで発生している事象について
http://www.trendmicro.co.jp/support/news.asp?id=2003
世界のセキュリティ・ラボから
世界で広がる様々なAndroid向け脅威
http://itpro.nikkeibp.co.jp/article/COLUMN/20130828/500789/?ST=security
ロリポップ!レンタルサーバーに大規模攻撃、WordPress利用中のサイト8438件が改ざん
http://itpro.nikkeibp.co.jp/article/NEWS/20130829/501062/?ST=security
IPAが“出口対策ガイドライン”の続編を公表、標的型攻撃に絞って詳細に
http://itpro.nikkeibp.co.jp/article/NEWS/20130829/501005/?ST=security
日本セーフネットと日本RAが提携、PKIベースUSB認証トークンの月額サービス提供へ
http://itpro.nikkeibp.co.jp/article/NEWS/20130829/500865/?ST=security
New York Timesサイトがほぼ復旧、Twitterも攻撃されていた---米メディアが報道
http://itpro.nikkeibp.co.jp/article/NEWS/20130829/500822/?ST=security
DoS/PoC: AVTECH DVR Firmware 1017-1003-1009-1003 - Multiple Vulnerabilities
http://www.exploit-db.com/exploits/27942
2013年8月30日金曜日
2013年8月29日木曜日
29日 木曜日、大安
+ RHSA-2013:1182 Important: 389-ds-base security update
http://rhn.redhat.com/errata/RHSA-2013-1182.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4283
+ Cisco Secure Access Control Server Remote Command Execution Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130828-acs
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3466
+ UPDATE: Multiple Vulnerabilities in Cisco Unified Customer Voice Portal Software
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130508-cvp
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1220
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1221
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1222
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1223
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1224
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1225
+ UPDATE: HPSBMU02746 SSRT100781 rev.2 - HP Data Protector Express, Remote Denial of Service (DoS), Execution of Arbitrary Code
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03229235-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ Red Hat Enterprise Virtualization Hypervisor XML Character Filtering Bug Lets Local Users Deny Service
http://www.securitytracker.com/id/1028955
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0167
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4236
+ Opera Browser Speed Dial Extensions XSS and XSRF
http://cxsecurity.com/issue/WLB-2013080216
+ IBM iNotes Cross Site Scripting
http://cxsecurity.com/issue/WLB-2013080215
+ Oracle Java ByteComponentRaster.verify() Memory Corruption
http://cxsecurity.com/issue/WLB-2013080214
+ SA54514 Opera Unspecified Vulnerabilities
http://secunia.com/advisories/54514/
Trend Micro InterScan Messaging Security Suite 7.1 Windows版 Patch 3 build 15240 公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=2002
Facebook、各国政府の情報請求レポートを公開、米国は1万件以上
http://itpro.nikkeibp.co.jp/article/NEWS/20130828/500584/?ST=security
New York Timesサイトが今月2度目のダウン、ハッキング攻撃か---米メディアの報道
http://itpro.nikkeibp.co.jp/article/NEWS/20130828/500542/?ST=security
MS13-056 (false positive)? alerts
https://isc.sans.edu/forums/diary/MS13-056+false+positive+alerts/16460
http://rhn.redhat.com/errata/RHSA-2013-1182.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4283
+ Cisco Secure Access Control Server Remote Command Execution Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130828-acs
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3466
+ UPDATE: Multiple Vulnerabilities in Cisco Unified Customer Voice Portal Software
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130508-cvp
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1220
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1221
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1222
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1223
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1224
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1225
+ UPDATE: HPSBMU02746 SSRT100781 rev.2 - HP Data Protector Express, Remote Denial of Service (DoS), Execution of Arbitrary Code
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03229235-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ Red Hat Enterprise Virtualization Hypervisor XML Character Filtering Bug Lets Local Users Deny Service
http://www.securitytracker.com/id/1028955
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0167
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4236
+ Opera Browser Speed Dial Extensions XSS and XSRF
http://cxsecurity.com/issue/WLB-2013080216
+ IBM iNotes Cross Site Scripting
http://cxsecurity.com/issue/WLB-2013080215
+ Oracle Java ByteComponentRaster.verify() Memory Corruption
http://cxsecurity.com/issue/WLB-2013080214
+ SA54514 Opera Unspecified Vulnerabilities
http://secunia.com/advisories/54514/
Trend Micro InterScan Messaging Security Suite 7.1 Windows版 Patch 3 build 15240 公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=2002
Facebook、各国政府の情報請求レポートを公開、米国は1万件以上
http://itpro.nikkeibp.co.jp/article/NEWS/20130828/500584/?ST=security
New York Timesサイトが今月2度目のダウン、ハッキング攻撃か---米メディアの報道
http://itpro.nikkeibp.co.jp/article/NEWS/20130828/500542/?ST=security
MS13-056 (false positive)? alerts
https://isc.sans.edu/forums/diary/MS13-056+false+positive+alerts/16460
2013年8月28日水曜日
28日 水曜日、仏滅
+ RHSA-2013:1173 Important: kernel security and bug fix update
http://rhn.redhat.com/errata/RHSA-2013-1173.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-6544
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2146
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2206
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2224
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2232
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2237
+ Opera 16.00 released
http://www.opera.com/docs/changelogs/unified/1600/
+ UPDATE: Microsoft Security Advisory (2862973) Update for Deprecation of MD5 Hashing Algorithm for Microsoft Root Certificate Program
http://technet.microsoft.com/en-us/security/advisory/2862973
+ UPDATE: Microsoft Security Advisory (2854544) Updates to Improve Cryptography and Digital Certificate Handling in Windows
http://technet.microsoft.com/en-us/security/advisory/2854544
+ Mac OS X 10.8.4 Sudo Password Bypass Vulnerability
http://cxsecurity.com/issue/WLB-2013080212
+ Linux Kernel ARM KVM NULL pointer dereferences
http://cxsecurity.com/issue/WLB-2013080210
+ Linux Kernel NULL Pointer Dereference Local Denial of Service Vulnerability
http://www.securityfocus.com/bid/61995
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5634
「2ちゃんねる」の有料サービスで情報流出、カード情報などが3万件以上
http://itpro.nikkeibp.co.jp/article/NEWS/20130828/500522/?ST=security
旧式ツール「Phish Locker」使ったオンライン詐欺が急増、RSAが報告
http://itpro.nikkeibp.co.jp/article/NEWS/20130827/500462/?ST=security
ITproまとめ
標的型攻撃
http://itpro.nikkeibp.co.jp/article/COLUMN/20130827/500344/?ST=security
IIJ、企業向けオンラインストレージに遠隔地DRオプションを追加
http://itpro.nikkeibp.co.jp/article/NEWS/20130827/500362/?ST=security
「増え続けるデータと攻撃者が大きな脅威に」サイバー犯罪やセキュリティで警察庁幹部らが指摘
http://itpro.nikkeibp.co.jp/article/NEWS/20130826/500262/?ST=security
JVNVU#94326802 Corporater EPM Suite に複数の脆弱性
http://jvn.jp/cert/JVNVU94326802/
JVNVU#92153282 RealPlayer のファイル名の処理にスタックバッファオーバーフローの脆弱性
http://jvn.jp/cert/JVNVU92153282/
LOCAL: WinAmp 5.63 (winamp.ini) - Local Exploit
http://www.exploit-db.com/exploits/27874
http://rhn.redhat.com/errata/RHSA-2013-1173.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-6544
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2146
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2206
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2224
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2232
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2237
+ Opera 16.00 released
http://www.opera.com/docs/changelogs/unified/1600/
+ UPDATE: Microsoft Security Advisory (2862973) Update for Deprecation of MD5 Hashing Algorithm for Microsoft Root Certificate Program
http://technet.microsoft.com/en-us/security/advisory/2862973
+ UPDATE: Microsoft Security Advisory (2854544) Updates to Improve Cryptography and Digital Certificate Handling in Windows
http://technet.microsoft.com/en-us/security/advisory/2854544
+ Mac OS X 10.8.4 Sudo Password Bypass Vulnerability
http://cxsecurity.com/issue/WLB-2013080212
+ Linux Kernel ARM KVM NULL pointer dereferences
http://cxsecurity.com/issue/WLB-2013080210
+ Linux Kernel NULL Pointer Dereference Local Denial of Service Vulnerability
http://www.securityfocus.com/bid/61995
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5634
「2ちゃんねる」の有料サービスで情報流出、カード情報などが3万件以上
http://itpro.nikkeibp.co.jp/article/NEWS/20130828/500522/?ST=security
旧式ツール「Phish Locker」使ったオンライン詐欺が急増、RSAが報告
http://itpro.nikkeibp.co.jp/article/NEWS/20130827/500462/?ST=security
ITproまとめ
標的型攻撃
http://itpro.nikkeibp.co.jp/article/COLUMN/20130827/500344/?ST=security
IIJ、企業向けオンラインストレージに遠隔地DRオプションを追加
http://itpro.nikkeibp.co.jp/article/NEWS/20130827/500362/?ST=security
「増え続けるデータと攻撃者が大きな脅威に」サイバー犯罪やセキュリティで警察庁幹部らが指摘
http://itpro.nikkeibp.co.jp/article/NEWS/20130826/500262/?ST=security
JVNVU#94326802 Corporater EPM Suite に複数の脆弱性
http://jvn.jp/cert/JVNVU94326802/
JVNVU#92153282 RealPlayer のファイル名の処理にスタックバッファオーバーフローの脆弱性
http://jvn.jp/cert/JVNVU92153282/
LOCAL: WinAmp 5.63 (winamp.ini) - Local Exploit
http://www.exploit-db.com/exploits/27874
2013年8月27日火曜日
27日 火曜日、先負
+ UPDATE: HPSBHF02888 rev.3 - HP Network Products including H3C and 3COM Routers and Switches, Remote Information Disclosure and Code Execution
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03808969-3%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ Perl 5.18.1 released
http://www.perl.org/get.html
+ IBM Lotus iNotes Input Validation Flaws Permit Cross-Site Scripting Attacks
http://www.securitytracker.com/id/1028954
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0590
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0591
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0595
+ RealPlayer Buffer Overflow and Memory Corruption Error Let Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1028953
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4973
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4974
+ Linux Kernel ARM Null Pointer Dereference Lets Local Users Deny Service
http://www.securitytracker.com/id/1028951
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5634
+ REMOTE: Oracle Endeca Server Remote Command Execution
http://www.exploit-db.com/exploits/27877
+ DoS/PoC: libtiff <= 3.9.5 - Integer Overflow
http://www.exploit-db.com/exploits/27875
+ SA54645 IBM Lotus iNotes Multiple Cross-Site Scripting Vulnerabilities
http://secunia.com/advisories/54645/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0590
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0591
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0595
+ SA54651 IBM WebSphere Extended Deployment Compute Grid Information Disclosure Weakness
http://secunia.com/advisories/54651/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4039
+ SA54655 IBM Tivoli Workload Scheduler OpenSSL Multiple Vulnerabilities
http://secunia.com/advisories/54655/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-3864
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0014
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3210
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-4108
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-4576
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-4577
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-4619
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0050
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0884
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-2131
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-2686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0166
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0169
+ SA54643 IBM WebSphere Commerce Tools Pages Cross-Site Scripting Vulnerabilities
http://secunia.com/advisories/54643/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0566
+ SA54621 RealPlayer Two Vulnerabilities
http://secunia.com/advisories/54621/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4973
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4974
+ Linux Kernel NULL Pointer Dereference Local Denial of Service Vulnerability
http://www.securityfocus.com/bid/61995
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5634
Trend Micro Deep Discovery Inspector 3.5 公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=2000
【スマホ少女の憂鬱、スマホ少年の暴走~今、10代が危ない】
第12回 話し合いと微調整を繰り返す、親は子供のスマホ利用にどう向き合う?(後編)
http://itpro.nikkeibp.co.jp/article/COLUMN/20130821/499306/?ST=security
JVNVU#92040696 SearchBlox に複数の脆弱性
http://jvn.jp/cert/JVNVU92040696/
VU#595142 Corporater EPM Suite is vulnerable to cross-site request forgery and cross-site scripting
http://www.kb.cert.org/vuls/id/595142
VU#246524 Real Media Player filename handler stack buffer overflow vulnerability
http://www.kb.cert.org/vuls/id/246524
REMOTE: Belkin G Wireless Router Firmware 5.00.12 - RCE PoC
http://www.exploit-db.com/exploits/27873
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03808969-3%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ Perl 5.18.1 released
http://www.perl.org/get.html
+ IBM Lotus iNotes Input Validation Flaws Permit Cross-Site Scripting Attacks
http://www.securitytracker.com/id/1028954
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0590
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0591
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0595
+ RealPlayer Buffer Overflow and Memory Corruption Error Let Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1028953
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4973
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4974
+ Linux Kernel ARM Null Pointer Dereference Lets Local Users Deny Service
http://www.securitytracker.com/id/1028951
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5634
+ REMOTE: Oracle Endeca Server Remote Command Execution
http://www.exploit-db.com/exploits/27877
+ DoS/PoC: libtiff <= 3.9.5 - Integer Overflow
http://www.exploit-db.com/exploits/27875
+ SA54645 IBM Lotus iNotes Multiple Cross-Site Scripting Vulnerabilities
http://secunia.com/advisories/54645/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0590
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0591
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0595
+ SA54651 IBM WebSphere Extended Deployment Compute Grid Information Disclosure Weakness
http://secunia.com/advisories/54651/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4039
+ SA54655 IBM Tivoli Workload Scheduler OpenSSL Multiple Vulnerabilities
http://secunia.com/advisories/54655/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-3864
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0014
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3210
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-4108
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-4576
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-4577
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-4619
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0050
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0884
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-2131
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-2686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0166
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0169
+ SA54643 IBM WebSphere Commerce Tools Pages Cross-Site Scripting Vulnerabilities
http://secunia.com/advisories/54643/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0566
+ SA54621 RealPlayer Two Vulnerabilities
http://secunia.com/advisories/54621/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4973
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4974
+ Linux Kernel NULL Pointer Dereference Local Denial of Service Vulnerability
http://www.securityfocus.com/bid/61995
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5634
Trend Micro Deep Discovery Inspector 3.5 公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=2000
【スマホ少女の憂鬱、スマホ少年の暴走~今、10代が危ない】
第12回 話し合いと微調整を繰り返す、親は子供のスマホ利用にどう向き合う?(後編)
http://itpro.nikkeibp.co.jp/article/COLUMN/20130821/499306/?ST=security
JVNVU#92040696 SearchBlox に複数の脆弱性
http://jvn.jp/cert/JVNVU92040696/
VU#595142 Corporater EPM Suite is vulnerable to cross-site request forgery and cross-site scripting
http://www.kb.cert.org/vuls/id/595142
VU#246524 Real Media Player filename handler stack buffer overflow vulnerability
http://www.kb.cert.org/vuls/id/246524
REMOTE: Belkin G Wireless Router Firmware 5.00.12 - RCE PoC
http://www.exploit-db.com/exploits/27873
2013年8月26日月曜日
26日 月曜日、友引
+ CESA-2013:X007 Moderate Xen4CentOS kernel Security Update
http://lwn.net/Alerts/564597/
+ VMSA-2013-0010 VMware Workstation host privilege escalation vulnerability
http://www.vmware.com/security/advisories/VMSA-2013-0010.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1662
+ RealNetworks, Inc. Releases Update to Address Security Vulnerabilities.
http://service.real.com/realplayer/security/08232013_player/en/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4973
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4974
+ VMware Workstation and Player vmware-mount Command Flaw Lets Local Users Gain Root Privileges
http://www.securitytracker.com/id/1028948
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1662
+ HP StoreOnce D2D Backup System Unspecified Flaw Lets Remote Users Deny Service
http://www.securitytracker.com/id/1028947
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2353
+ Google Chrome Multiple Bugs Let Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1028942
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2887
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2900
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2901
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2902
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2903
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2904
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2905
+ VMware Workstation / Player "vmware-mount" Privilege Escalation Vulnerability
http://secunia.com/advisories/54580/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1662
Advisory: Following an update to Sophos Anti-Virus, the Sophos Anti-Virus service fails to start for PureMessage for Microsoft Exchange and Sophos for Microsoft SharePoint
http://www.sophos.com/en-us/support/knowledgebase/119717.aspx
Office 2003も来年4月にサポート終了、クラウドへの切り替えを急げ
日本マイクロソフトOffice ビジネス本部 Officeマーケティング グループ シニア プロダクト マネージャー、輪島文氏
http://itpro.nikkeibp.co.jp/article/Interview/20130823/499785/?ST=security
VU#592942 SearchBlox contains multiple vulnerabilities
http://www.kb.cert.org/vuls/id/592942
REMOTE: dreamMail e-mail client v4.6.9.2 Stored XSS
http://www.exploit-db.com/exploits/27805
Oracle Endeca Server Remote Command Execution
http://cxsecurity.com/issue/WLB-2013080194
http://lwn.net/Alerts/564597/
+ VMSA-2013-0010 VMware Workstation host privilege escalation vulnerability
http://www.vmware.com/security/advisories/VMSA-2013-0010.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1662
+ RealNetworks, Inc. Releases Update to Address Security Vulnerabilities.
http://service.real.com/realplayer/security/08232013_player/en/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4973
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4974
+ VMware Workstation and Player vmware-mount Command Flaw Lets Local Users Gain Root Privileges
http://www.securitytracker.com/id/1028948
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1662
+ HP StoreOnce D2D Backup System Unspecified Flaw Lets Remote Users Deny Service
http://www.securitytracker.com/id/1028947
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2353
+ Google Chrome Multiple Bugs Let Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1028942
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2887
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2900
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2901
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2902
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2903
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2904
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2905
+ VMware Workstation / Player "vmware-mount" Privilege Escalation Vulnerability
http://secunia.com/advisories/54580/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1662
Advisory: Following an update to Sophos Anti-Virus, the Sophos Anti-Virus service fails to start for PureMessage for Microsoft Exchange and Sophos for Microsoft SharePoint
http://www.sophos.com/en-us/support/knowledgebase/119717.aspx
Office 2003も来年4月にサポート終了、クラウドへの切り替えを急げ
日本マイクロソフトOffice ビジネス本部 Officeマーケティング グループ シニア プロダクト マネージャー、輪島文氏
http://itpro.nikkeibp.co.jp/article/Interview/20130823/499785/?ST=security
VU#592942 SearchBlox contains multiple vulnerabilities
http://www.kb.cert.org/vuls/id/592942
REMOTE: dreamMail e-mail client v4.6.9.2 Stored XSS
http://www.exploit-db.com/exploits/27805
Oracle Endeca Server Remote Command Execution
http://cxsecurity.com/issue/WLB-2013080194
2013年8月23日金曜日
23日 金曜日、大安
+ HPSBST02897 rev.1 - HP StoreOnce D2D Backup System, Remote Denial of Service (DoS)
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03828580-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2353
+ PHP 5.4.19 and PHP 5.5.3 Released!
http://www.php.net/ChangeLog-5.php#5.4.19
+ McAfee Email Gateway SMTP Processing Flaw Lets Remote Users Deny Service
http://www.securitytracker.com/id/1028941
+ FreeBSD SCTP Discloses Portions of Kernel Memory Contents to Remote Users
http://www.securitytracker.com/id/1028940
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5209
+ FreeBSD Integer Overflow in IP_MSFILTER Lets Local Users Gain Elevated Privileges
http://www.securitytracker.com/id/1028939
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3077
+ DoS/PoC: Samba nttrans Reply - Integer Overflow Vulnerability
http://www.exploit-db.com/exploits/27778
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4124
+ SA54603 FreeBSD SCTP Information Disclosure and IP_MSFILTER Privileges Escalation Vulnerabilities
http://secunia.com/advisories/54603/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3077
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5209
+ Samba nttrans Reply Integer Overflow Vulnerability
http://cxsecurity.com/issue/WLB-2013080182
+ FreeBSD IP_MSFILTER Local Privilege Escalation Vulnerability
http://www.securityfocus.com/bid/61946
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3077
+ FreeBSD CVE-2013-5209 Information Disclosure Vulnerability
http://www.securityfocus.com/bid/61939
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5209
How to effectively set user permissions in Gaia OS
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk94491&src=securityAlerts
脆弱性対策オプション 1.5 Service Pack 1 Patch 1 公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=1970
PostgreSQL 9.3 RC1 Available for Testing
http://www.postgresql.org/about/news/1478/
CTC、標的型攻撃の耐性診断SIサービスをメニュー化
http://itpro.nikkeibp.co.jp/article/NEWS/20130822/499628/?ST=security
政府機関や企業を狙うサイバー攻撃、独自プロトコルを使うマルウエアが急増
http://itpro.nikkeibp.co.jp/article/NEWS/20130822/499443/?ST=security
NSAは米国ネット通信の75%を監視可能---米メディアが報道
http://itpro.nikkeibp.co.jp/article/NEWS/20130822/499442/?ST=security
「GM作物の遺伝子」で有害雑草の成長力が向上(WIRED.jp)
http://itpro.nikkeibp.co.jp/article/NEWS/20130822/499422/?ST=security
JVNVU#94025783 Web Viewer for Samsung DVR に複数の脆弱性
http://jvn.jp/cert/JVNVU94025783/
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03828580-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2353
+ PHP 5.4.19 and PHP 5.5.3 Released!
http://www.php.net/ChangeLog-5.php#5.4.19
+ McAfee Email Gateway SMTP Processing Flaw Lets Remote Users Deny Service
http://www.securitytracker.com/id/1028941
+ FreeBSD SCTP Discloses Portions of Kernel Memory Contents to Remote Users
http://www.securitytracker.com/id/1028940
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5209
+ FreeBSD Integer Overflow in IP_MSFILTER Lets Local Users Gain Elevated Privileges
http://www.securitytracker.com/id/1028939
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3077
+ DoS/PoC: Samba nttrans Reply - Integer Overflow Vulnerability
http://www.exploit-db.com/exploits/27778
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4124
+ SA54603 FreeBSD SCTP Information Disclosure and IP_MSFILTER Privileges Escalation Vulnerabilities
http://secunia.com/advisories/54603/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3077
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5209
+ Samba nttrans Reply Integer Overflow Vulnerability
http://cxsecurity.com/issue/WLB-2013080182
+ FreeBSD IP_MSFILTER Local Privilege Escalation Vulnerability
http://www.securityfocus.com/bid/61946
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3077
+ FreeBSD CVE-2013-5209 Information Disclosure Vulnerability
http://www.securityfocus.com/bid/61939
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5209
How to effectively set user permissions in Gaia OS
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk94491&src=securityAlerts
脆弱性対策オプション 1.5 Service Pack 1 Patch 1 公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=1970
PostgreSQL 9.3 RC1 Available for Testing
http://www.postgresql.org/about/news/1478/
CTC、標的型攻撃の耐性診断SIサービスをメニュー化
http://itpro.nikkeibp.co.jp/article/NEWS/20130822/499628/?ST=security
政府機関や企業を狙うサイバー攻撃、独自プロトコルを使うマルウエアが急増
http://itpro.nikkeibp.co.jp/article/NEWS/20130822/499443/?ST=security
NSAは米国ネット通信の75%を監視可能---米メディアが報道
http://itpro.nikkeibp.co.jp/article/NEWS/20130822/499442/?ST=security
「GM作物の遺伝子」で有害雑草の成長力が向上(WIRED.jp)
http://itpro.nikkeibp.co.jp/article/NEWS/20130822/499422/?ST=security
JVNVU#94025783 Web Viewer for Samsung DVR に複数の脆弱性
http://jvn.jp/cert/JVNVU94025783/
2013年8月22日木曜日
22日 木曜日、仏滅
+ CESA-2013:1166 Important CentOS 5 kernel Update
http://lwn.net/Alerts/564230/
+ Multiple Vulnerabilities in Cisco Unified Communications Manager
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130821-cucm
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3459
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3460
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3461
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3462
+ Cisco Unified Communications Manager IM and Presence Service Denial of Service Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130821-cup
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3453
+ Cisco Prime Central for Hosted Collaboration Solution Assurance Denial of Service Vulnerabilities
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130821-hcm
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3390
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3389
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3388
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3387
+ IBM WebSphere Portal Unspecified Bug Lets Remote Users Access User Directories
http://www.securitytracker.com/id/1028933
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3016
+ IBM WebSphere Application Server Input Validation Flaw in Administrative Console Permits Cross-Site Scripting Attacks
http://www.securitytracker.com/id/1028932
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4005
+ Xen Intel VT-d Interrupt Processing Flaw Lets Local Users Deny Service on the Host System
http://www.securitytracker.com/id/1028931
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3495
+ MySQL Debian/Ubuntu Installation Script Lets Local Users Obtain Potentially Sensitive Information
http://www.securitytracker.com/id/1028927
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2162
+ REMOTE: Oracle Java BytePackedRaster.verify() Signed Integer Overflow
http://www.exploit-db.com/exploits/27754
+ Linux kernel vfs_read()/vfs_write() potential missing checks
http://cxsecurity.com/issue/WLB-2013080168
+ SA54486 McAfee Email Gateway Email Processing "ws_inv-smtp" Denial of Service Vulnerability
http://secunia.com/advisories/54486/
Check Point response to OSPF LSA spoofing vulnerability (VU#229804)
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk94490&src=securityAlerts
JVNDB-2013-000080 PHP OpenID Library における XML 外部実体参照に関する脆弱性
http://jvndb.jvn.jp/ja/contents/2013/JVNDB-2013-000080.html
世界のセキュリティ・ラボから
不正URLに使用される短縮URLサービス
http://itpro.nikkeibp.co.jp/article/COLUMN/20130819/498687/?ST=security
米政府の監視活動問題をめぐり英当局が英紙に資料破壊を要請---Guardian報道
http://itpro.nikkeibp.co.jp/article/NEWS/20130821/499142/?ST=security
JVNVU#95005184 Dell の BIOS 更新処理にバッファオーバーフローの脆弱性
http://jvn.jp/cert/JVNVU95005184/
JVN#24713981 PHP OpenID Library における XML 外部実体参照に関する脆弱性
http://jvn.jp/jp/JVN24713981/
VU#882286 Samsung Web Viewer for Samsung DVR allows authentication bypass and password disclosure
http://www.kb.cert.org/vuls/id/882286
REMOTE: freeFTPd 1.0.10 (PASS Command) - SEH Buffer Overflow
http://www.exploit-db.com/exploits/27747
REMOTE: Graphite Web Unsafe Pickle Handling
http://www.exploit-db.com/exploits/27752
2013年8月21日水曜日
21日 水曜日、先負
+ UPDATE: HPSBGN02905 rev.2 - HP LoadRunner, HP Business Process Monitor, Remote Code Execution and Denial of Service (DoS)
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03862772-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ Google Chrome 29.0.1547.57 released
http://googlechromereleases.blogspot.jp/2013/08/stable-channel-update.html
+ RHSA-2013:1166 Important: kernel security and bug fix update
http://rhn.redhat.com/errata/RHSA-2013-1166.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2147
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2164
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2206
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2224
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2232
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2234
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2237
+ Samba 4.0.9 Available for Download
http://samba.org/samba/history/samba-4.0.9.html
+ Oracle Java BytePackedRaster.verify() Signed Integer Overflow
http://cxsecurity.com/issue/WLB-2013080158
+ Linux Kernel CVE-2013-4247 Memory Corruption Vulnerability
http://www.securityfocus.com/bid/61800
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4247
+ Google Chrome Prior to 29.0.1547.57 Multiple Security Vulnerabilities
http://www.securityfocus.com/bid/61865
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2887
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2900
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2901
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2902
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2903
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2904
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2905
キヤノンITS、法人向けセキュリティ製品のXPサポートを2017年2月まで継続
「ESET Endpoint Protection シリーズ」が対象
http://itpro.nikkeibp.co.jp/article/NEWS/20130821/499123/?ST=security
韓国サイバー攻撃を他山の石に、実は無防備な社内サーバー
トレンドマイクロ 代表取締役社長兼CEO(最高経営責任者)
エバ・チェン氏
http://itpro.nikkeibp.co.jp/article/Interview/20130717/492076/?ST=security
チェックしておきたい脆弱性情報<2013.08.21>
http://itpro.nikkeibp.co.jp/article/COLUMN/20130819/498702/?ST=security
OCNへの不正アクセスは無線LANルーターの脆弱性が原因の可能性、ファームウェア更新呼びかけ
http://itpro.nikkeibp.co.jp/article/NEWS/20130820/499111/?ST=security
あらゆるものをタッチスクリーンにするソフトウェア「Ubi」(WIRED.jp)
http://itpro.nikkeibp.co.jp/article/NEWS/20130820/498883/?ST=security
世界のセキュリティ・ラボ
Windowsマルウエアを内包したAndroidアプリケーション
http://itpro.nikkeibp.co.jp/article/COLUMN/20130819/498645/?ST=security
チェックしておきたい脆弱性情報<2013.08.20>
http://itpro.nikkeibp.co.jp/article/COLUMN/20130819/498643/?ST=security
JVNVU#96465452 Open Shortest Path First (OSPF) プロトコルの Link State Advertisement (LSA) に関する問題
http://jvn.jp/cert/JVNVU96465452/index.html
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03862772-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ Google Chrome 29.0.1547.57 released
http://googlechromereleases.blogspot.jp/2013/08/stable-channel-update.html
+ RHSA-2013:1166 Important: kernel security and bug fix update
http://rhn.redhat.com/errata/RHSA-2013-1166.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2147
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2164
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2206
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2224
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2232
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2234
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2237
+ Samba 4.0.9 Available for Download
http://samba.org/samba/history/samba-4.0.9.html
+ Oracle Java BytePackedRaster.verify() Signed Integer Overflow
http://cxsecurity.com/issue/WLB-2013080158
+ Linux Kernel CVE-2013-4247 Memory Corruption Vulnerability
http://www.securityfocus.com/bid/61800
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4247
+ Google Chrome Prior to 29.0.1547.57 Multiple Security Vulnerabilities
http://www.securityfocus.com/bid/61865
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2887
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2900
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2901
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2902
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2903
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2904
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2905
キヤノンITS、法人向けセキュリティ製品のXPサポートを2017年2月まで継続
「ESET Endpoint Protection シリーズ」が対象
http://itpro.nikkeibp.co.jp/article/NEWS/20130821/499123/?ST=security
韓国サイバー攻撃を他山の石に、実は無防備な社内サーバー
トレンドマイクロ 代表取締役社長兼CEO(最高経営責任者)
エバ・チェン氏
http://itpro.nikkeibp.co.jp/article/Interview/20130717/492076/?ST=security
チェックしておきたい脆弱性情報<2013.08.21>
http://itpro.nikkeibp.co.jp/article/COLUMN/20130819/498702/?ST=security
OCNへの不正アクセスは無線LANルーターの脆弱性が原因の可能性、ファームウェア更新呼びかけ
http://itpro.nikkeibp.co.jp/article/NEWS/20130820/499111/?ST=security
あらゆるものをタッチスクリーンにするソフトウェア「Ubi」(WIRED.jp)
http://itpro.nikkeibp.co.jp/article/NEWS/20130820/498883/?ST=security
世界のセキュリティ・ラボ
Windowsマルウエアを内包したAndroidアプリケーション
http://itpro.nikkeibp.co.jp/article/COLUMN/20130819/498645/?ST=security
チェックしておきたい脆弱性情報<2013.08.20>
http://itpro.nikkeibp.co.jp/article/COLUMN/20130819/498643/?ST=security
JVNVU#96465452 Open Shortest Path First (OSPF) プロトコルの Link State Advertisement (LSA) に関する問題
http://jvn.jp/cert/JVNVU96465452/index.html
2013年8月20日火曜日
20日 火曜日、友引
+ UPDATE: HPSBMU02902 rev.2 - HP Integrated Lights-Out iLO3, iLO4, and iLO CM IPMI, Cipher Suite 0 Authentication Bypass Vulnerabilit
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03844348-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ OpenLDAP 2.4.36 released
http://www.openldap.org/software/release/
+ Linux Kernel ARM perf_event_open() Bug Lets Local Users Gain Elevated Privileges
http://www.securitytracker.com/id/1028926
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4254
+ PHP May Let Remote Users Hijack User Sessions
http://www.securitytracker.com/id/1028925
+ PHP OpenSSL subjectAltName Null Byte Processing Flaw Lets Remote Users Spoof SSL Servers
http://www.securitytracker.com/id/1028924
+ REMOTE: Mozilla Firefox 3.6 - Integer Overflow Exploit
http://www.exploit-db.com/exploits/27698
+ REMOTE: Mozilla Firefox 3.5.4 - Local Color Map Exploit
http://www.exploit-db.com/exploits/27699
+ REMOTE: PCMAN FTP 2.07 STOR Command - Buffer Overflow Exploit
http://www.exploit-db.com/exploits/27703
+ REMOTE: Cogent DataHub HTTP Server Buffer Overflow
http://www.exploit-db.com/exploits/27704
+ REMOTE: Java storeImageArray() Invalid Array Indexing Vulnerability
http://www.exploit-db.com/exploits/27705
+ REMOTE: IBM 1754 GCM 1.18.0.22011 - Remote Command Execution
http://www.exploit-db.com/exploits/27706
+ DoS/PoC: VLC Player 2.0.8 (.m3u) - Local Crash PoC
http://www.exploit-db.com/exploits/27700
+ Mozilla Firefox 3.6 Integer Overflow Exploit
http://cxsecurity.com/issue/WLB-2013080154
+ glibc ld-2.5.so security
http://cxsecurity.com/issue/WLB-2013080153
+ SA54494 Linux Kernel ARM Perf Event Privilege Escalation Vulnerability
http://secunia.com/advisories/54494/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4254
+ SA54099 Linux Kernel ARM Perf Event Denial of Service Vulnerability
http://secunia.com/advisories/54099/
+ SA54562 PHP SSL Client Certificate Verification and Session Fixation Vulnerabilities
http://secunia.com/advisories/54562/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-4718
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4248
JVNDB-2013-000079 Android 版 Yahoo!ショッピングにおける SSL サーバ証明書の検証不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2013/JVNDB-2013-000079.html
JVNDB-2013-000078 ヤフオク! における SSL サーバ証明書の検証不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2013/JVNDB-2013-000078.html
【スマホ少女の憂鬱、スマホ少年の暴走~今、10代が危ない】
第11回 鍵になる「ルール作り」、親は子供のスマホ利用にどう向き合う?(前編)
http://itpro.nikkeibp.co.jp/article/COLUMN/20130819/498685/?ST=security
「Web改ざんと不正アクセス急増」と注意喚起、トレンドマイクロが13年上期の脅威動向を発表
http://itpro.nikkeibp.co.jp/article/NEWS/20130819/498862/?ST=security
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03844348-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ OpenLDAP 2.4.36 released
http://www.openldap.org/software/release/
+ Linux Kernel ARM perf_event_open() Bug Lets Local Users Gain Elevated Privileges
http://www.securitytracker.com/id/1028926
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4254
+ PHP May Let Remote Users Hijack User Sessions
http://www.securitytracker.com/id/1028925
+ PHP OpenSSL subjectAltName Null Byte Processing Flaw Lets Remote Users Spoof SSL Servers
http://www.securitytracker.com/id/1028924
+ REMOTE: Mozilla Firefox 3.6 - Integer Overflow Exploit
http://www.exploit-db.com/exploits/27698
+ REMOTE: Mozilla Firefox 3.5.4 - Local Color Map Exploit
http://www.exploit-db.com/exploits/27699
+ REMOTE: PCMAN FTP 2.07 STOR Command - Buffer Overflow Exploit
http://www.exploit-db.com/exploits/27703
+ REMOTE: Cogent DataHub HTTP Server Buffer Overflow
http://www.exploit-db.com/exploits/27704
+ REMOTE: Java storeImageArray() Invalid Array Indexing Vulnerability
http://www.exploit-db.com/exploits/27705
+ REMOTE: IBM 1754 GCM 1.18.0.22011 - Remote Command Execution
http://www.exploit-db.com/exploits/27706
+ DoS/PoC: VLC Player 2.0.8 (.m3u) - Local Crash PoC
http://www.exploit-db.com/exploits/27700
+ Mozilla Firefox 3.6 Integer Overflow Exploit
http://cxsecurity.com/issue/WLB-2013080154
+ glibc ld-2.5.so security
http://cxsecurity.com/issue/WLB-2013080153
+ SA54494 Linux Kernel ARM Perf Event Privilege Escalation Vulnerability
http://secunia.com/advisories/54494/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4254
+ SA54099 Linux Kernel ARM Perf Event Denial of Service Vulnerability
http://secunia.com/advisories/54099/
+ SA54562 PHP SSL Client Certificate Verification and Session Fixation Vulnerabilities
http://secunia.com/advisories/54562/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-4718
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4248
JVNDB-2013-000079 Android 版 Yahoo!ショッピングにおける SSL サーバ証明書の検証不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2013/JVNDB-2013-000079.html
JVNDB-2013-000078 ヤフオク! における SSL サーバ証明書の検証不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2013/JVNDB-2013-000078.html
【スマホ少女の憂鬱、スマホ少年の暴走~今、10代が危ない】
第11回 鍵になる「ルール作り」、親は子供のスマホ利用にどう向き合う?(前編)
http://itpro.nikkeibp.co.jp/article/COLUMN/20130819/498685/?ST=security
「Web改ざんと不正アクセス急増」と注意喚起、トレンドマイクロが13年上期の脅威動向を発表
http://itpro.nikkeibp.co.jp/article/NEWS/20130819/498862/?ST=security
2013年8月19日月曜日
19日 月曜日、先勝
+ Vim 7.4 released
http://www.vim.org/
+ Mozilla Firefox 23.0.1 released
http://www.mozilla.jp/firefox/download/all/
+ UPDATE: OSPF LSA Manipulation Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130801-lsaospf
+ UPDATE: Cisco TelePresence System Default Credentials Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130807-tp
+ PHP 5.5.2, 5.4.18 Released!
http://php.net/archive/2013.php#id2013-08-16-1
http://php.net/archive/2013.php#id2013-08-15-1
+ Juniper Junos Space Bugs Let Remote Users Conduct Cross-Site Scripting Attacks and Remote Authenticated Users Modify the Configuration and Obtain Authentication Information
http://www.securitytracker.com/id/1028923
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5095
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5096
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5097
+ Juniper Network and Security Manager SSL Session Renegotiation Flaw Lets Remote Users Deny Service
http://www.securitytracker.com/id/1028922
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-1473
+ Juniper Security Threat Response Manager Lets Remote Authenticated Users Execute Arbitrary Commands
http://www.securitytracker.com/id/1028921
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2970
+ SA54565 McAfee Data Loss Prevention Multiple Vulnerabilities
http://secunia.com/advisories/54565/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2004-0230
+ SA54554 PHP SSL Client Certificate Verification and XML Parsing Buffer Overflow Vulnerabilities
http://secunia.com/advisories/54554/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4073
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4113
+ Cisco WebEx One-Click Client Password Encryption Information Vulnerability
http://cxsecurity.com/issue/WLB-2013080147
+ Linux Kernel 3.11-rc ARM/perf priviledge escalation
http://cxsecurity.com/issue/WLB-2013080128
+ Linux Kernel 'perf_event.c' Local Privilege Escalation Vulnerability
http://www.securityfocus.com/bid/61793
InterScan WebManager 8.0リパック版公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=1998
Trend Micro Network VirusWall Enforcer 1500i/3500i/3600i バージョン 3.5 公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=1997
Error 0x80131604 shown when the console fails to open
http://www.sophos.com/en-us/support/knowledgebase/118219.aspx
Facebookの脆弱性、発見者がZuckerberg CEOのウオールを使って証明
http://itpro.nikkeibp.co.jp/article/NEWS/20130819/498642/?ST=security
「ウイルス配布サイトは使い捨て」――標的型攻撃の実態
ファイア・アイが報告
http://itpro.nikkeibp.co.jp/article/NEWS/20130819/498583/?ST=security
JVNVU#95005184 Dell の BIOS 更新処理にバッファオーバーフローの脆弱性
http://jvn.jp/cert/JVNVU95005184/index.html
http://www.vim.org/
+ Mozilla Firefox 23.0.1 released
http://www.mozilla.jp/firefox/download/all/
+ UPDATE: OSPF LSA Manipulation Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130801-lsaospf
+ UPDATE: Cisco TelePresence System Default Credentials Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130807-tp
+ PHP 5.5.2, 5.4.18 Released!
http://php.net/archive/2013.php#id2013-08-16-1
http://php.net/archive/2013.php#id2013-08-15-1
+ Juniper Junos Space Bugs Let Remote Users Conduct Cross-Site Scripting Attacks and Remote Authenticated Users Modify the Configuration and Obtain Authentication Information
http://www.securitytracker.com/id/1028923
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5095
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5096
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5097
+ Juniper Network and Security Manager SSL Session Renegotiation Flaw Lets Remote Users Deny Service
http://www.securitytracker.com/id/1028922
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-1473
+ Juniper Security Threat Response Manager Lets Remote Authenticated Users Execute Arbitrary Commands
http://www.securitytracker.com/id/1028921
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2970
+ SA54565 McAfee Data Loss Prevention Multiple Vulnerabilities
http://secunia.com/advisories/54565/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2004-0230
+ SA54554 PHP SSL Client Certificate Verification and XML Parsing Buffer Overflow Vulnerabilities
http://secunia.com/advisories/54554/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4073
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4113
+ Cisco WebEx One-Click Client Password Encryption Information Vulnerability
http://cxsecurity.com/issue/WLB-2013080147
+ Linux Kernel 3.11-rc ARM/perf priviledge escalation
http://cxsecurity.com/issue/WLB-2013080128
+ Linux Kernel 'perf_event.c' Local Privilege Escalation Vulnerability
http://www.securityfocus.com/bid/61793
InterScan WebManager 8.0リパック版公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=1998
Trend Micro Network VirusWall Enforcer 1500i/3500i/3600i バージョン 3.5 公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=1997
Error 0x80131604 shown when the console fails to open
http://www.sophos.com/en-us/support/knowledgebase/118219.aspx
Facebookの脆弱性、発見者がZuckerberg CEOのウオールを使って証明
http://itpro.nikkeibp.co.jp/article/NEWS/20130819/498642/?ST=security
「ウイルス配布サイトは使い捨て」――標的型攻撃の実態
ファイア・アイが報告
http://itpro.nikkeibp.co.jp/article/NEWS/20130819/498583/?ST=security
JVNVU#95005184 Dell の BIOS 更新処理にバッファオーバーフローの脆弱性
http://jvn.jp/cert/JVNVU95005184/index.html
2013年8月16日金曜日
Android-x86 4.3 INSTALL MEMO
http://www.android-x86.org/download から Android-x86 4.3-20130725 を入手してインストールしてみた。
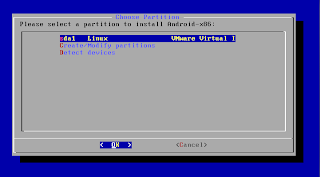
1. ISO イメージからブートしてハードディスクへのインストールを選択。
6. フォーマットを開始。
7. boot loader GRUB のインストールを選択。
8. システムディレクトリへの読み書きを許可。
9. インストールが始まる。
10. インストールが成功して "Reboot" を選択。
11. Android が起動を始める。
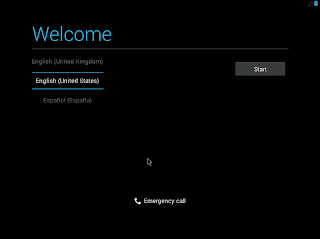
12. 設定が始まる。言語選択。(残念ながら日本語がない)
13. 何か設定している。
14. Wi-Fi の設定だが、環境がないのでスキップを選択。
15. 確認画面でもスキップを選択。
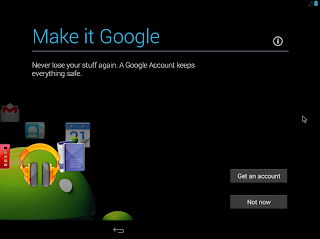
16. Google アカウントは持っているが、ネット接続できないので "No" を選択。
17. ここも "Not Now" を選択。
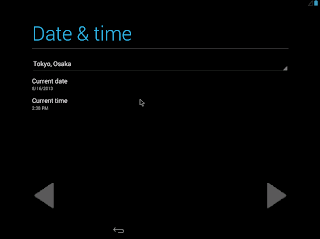
18. ローケーションの設定が始まる。
19. ロケールに "Tokyo, Osaka" を選択、日付と時刻を調整。
20. 一応名前を入力。
21. Google サービスを確認。
22. セットアップ完了。
23. トップ画面と共に操作説明が表示される。[OK] を押す。
24. アプリ選択でも操作説明が表示される。[OK] を押す。
25. 有線LAN を有効にするために eth0 を設定。http-proxy も設定。
(ALT-F1 で画面切り替え、ALT-F7 で戻る)
ネット接続は成功したが、Proxy 経由でブラウジングができない… なぜ?
1. ISO イメージからブートしてハードディスクへのインストールを選択。
2. 新規のパーティション作成を選択。
3. "Primary" ですべての領域を指定、"Boot" フラッグを付けて作成。
4. 作成してパーティションを選択。
5. "ext3" でのフォーマットを選択。
6. フォーマットを開始。
7. boot loader GRUB のインストールを選択。
8. システムディレクトリへの読み書きを許可。
9. インストールが始まる。
10. インストールが成功して "Reboot" を選択。
11. Android が起動を始める。
12. 設定が始まる。言語選択。(残念ながら日本語がない)
13. 何か設定している。
14. Wi-Fi の設定だが、環境がないのでスキップを選択。
15. 確認画面でもスキップを選択。
16. Google アカウントは持っているが、ネット接続できないので "No" を選択。
18. ローケーションの設定が始まる。
19. ロケールに "Tokyo, Osaka" を選択、日付と時刻を調整。
20. 一応名前を入力。
21. Google サービスを確認。
22. セットアップ完了。
23. トップ画面と共に操作説明が表示される。[OK] を押す。
24. アプリ選択でも操作説明が表示される。[OK] を押す。
25. 有線LAN を有効にするために eth0 を設定。http-proxy も設定。
(ALT-F1 で画面切り替え、ALT-F7 で戻る)
ネット接続は成功したが、Proxy 経由でブラウジングができない… なぜ?
16日 金曜日、仏滅
+ HPSBMU02915 rev.1 - HP Service Manager, Remote Unauthenticated Access and Elevation of Privilege
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03888320-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ UPDATE: Oracle Critical Patch Update Advisory - July 2013
http://www.oracle.com/technetwork/topics/security/cpujuly2013-1899826.html
+ Kingsoft Writer Buffer Overflow Let Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1028920
+ Google Android PRNG Initialization Flaw Causes Some Cryptographic Applications to Be Less Secure
http://www.securitytracker.com/id/1028916
+ Cisco IOS XR ICMP Memory Corruption Flaw Lets Local Users Deny Service
http://www.securitytracker.com/id/1028914
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3464
+ VU#912156 Dell BIOS in some Latitude laptops and Precision Mobile Workstations vulnerable to buffer overflow
http://www.kb.cert.org/vuls/id/912156
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3582
+ REMOTE: Oracle Java IntegerInterleavedRaster.verify() Signed Integer Overflow
http://www.exploit-db.com/exploits/27611
+ Linux Kernel 3.11-rc ARM/perf priviledge escalation
http://cxsecurity.com/issue/WLB-2013080128
+ SA53266 Kingsoft Writer 2012 WPS Font Names Buffer Overflow Vulnerability
http://secunia.com/advisories/53266/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3934
+ PHP SSL Certificate Validation CVE-2013-4248 Security Bypass Vulnerability
http://www.securityfocus.com/bid/61776
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4248
REMOTE: Intrasrv 1.0 Buffer Overflow
http://www.exploit-db.com/exploits/27606
REMOTE: MiniWeb (Build 300) Arbitrary File Upload
http://www.exploit-db.com/exploits/27607
REMOTE: Ultra Mini HTTPD Stack Buffer Overflow
http://www.exploit-db.com/exploits/27608
REMOTE: Joomla Media Manager File Upload Vulnerability
http://www.exploit-db.com/exploits/27610
LOCAL: Chasys Draw IES Buffer Overflow
http://www.exploit-db.com/exploits/27609
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03888320-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ UPDATE: Oracle Critical Patch Update Advisory - July 2013
http://www.oracle.com/technetwork/topics/security/cpujuly2013-1899826.html
+ Kingsoft Writer Buffer Overflow Let Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1028920
+ Google Android PRNG Initialization Flaw Causes Some Cryptographic Applications to Be Less Secure
http://www.securitytracker.com/id/1028916
+ Cisco IOS XR ICMP Memory Corruption Flaw Lets Local Users Deny Service
http://www.securitytracker.com/id/1028914
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3464
+ VU#912156 Dell BIOS in some Latitude laptops and Precision Mobile Workstations vulnerable to buffer overflow
http://www.kb.cert.org/vuls/id/912156
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3582
+ REMOTE: Oracle Java IntegerInterleavedRaster.verify() Signed Integer Overflow
http://www.exploit-db.com/exploits/27611
+ Linux Kernel 3.11-rc ARM/perf priviledge escalation
http://cxsecurity.com/issue/WLB-2013080128
+ SA53266 Kingsoft Writer 2012 WPS Font Names Buffer Overflow Vulnerability
http://secunia.com/advisories/53266/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3934
+ PHP SSL Certificate Validation CVE-2013-4248 Security Bypass Vulnerability
http://www.securityfocus.com/bid/61776
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4248
REMOTE: Intrasrv 1.0 Buffer Overflow
http://www.exploit-db.com/exploits/27606
REMOTE: MiniWeb (Build 300) Arbitrary File Upload
http://www.exploit-db.com/exploits/27607
REMOTE: Ultra Mini HTTPD Stack Buffer Overflow
http://www.exploit-db.com/exploits/27608
REMOTE: Joomla Media Manager File Upload Vulnerability
http://www.exploit-db.com/exploits/27610
LOCAL: Chasys Draw IES Buffer Overflow
http://www.exploit-db.com/exploits/27609
2013年8月15日木曜日
15日 木曜日、先負
+ Selenium Server 2.35.0 released
http://docs.seleniumhq.org/download/
+ Selenium The Internet Explorer Driver Server 2.35.0 released
http://docs.seleniumhq.org/download/
+ Selenium WebDriver 2.35.0 released
http://docs.seleniumhq.org/download/
http://selenium.googlecode.com/git/java/CHANGELOG
+ CESA-2013:1156 Moderate CentOS 6 httpd Update
http://lwn.net/Alerts/563368/
+ CESA-2013:1156 Moderate CentOS 5 httpd Update
http://lwn.net/Alerts/563369/
+ Samba 3.6.18 Available for Download
http://samba.org/samba/history/samba-3.6.18.html
+ Oracle Java IntegerInterleavedRaster.verify() Signed Integer Overflow
http://cxsecurity.com/issue/WLB-2013080116
+ Apache Struts2 2.3.15 OGNL Injection
http://cxsecurity.com/issue/WLB-2013080115
+ Apache Struts2 2.3.15 Open Redirect
http://cxsecurity.com/issue/WLB-2013080111
+ SA54480 PHP SSL Module "subjectAltNames" NULL Byte Handling Security Issue
http://secunia.com/advisories/54480/
+ PHP SSL Certificate Validation Security Bypass Vulnerability
http://www.securityfocus.com/bid/61776
Advisory: Following an update to Sophos Anti-Virus the Sophos Anti-Virus service fails to start
http://www.sophos.com/en-us/support/knowledgebase/119717.aspx
JVNTA13-225A Microsoft 製品の複数の脆弱性に対するアップデート
http://jvn.jp/cert/JVNTA13-225A/
http://docs.seleniumhq.org/download/
+ Selenium The Internet Explorer Driver Server 2.35.0 released
http://docs.seleniumhq.org/download/
+ Selenium WebDriver 2.35.0 released
http://docs.seleniumhq.org/download/
http://selenium.googlecode.com/git/java/CHANGELOG
+ CESA-2013:1156 Moderate CentOS 6 httpd Update
http://lwn.net/Alerts/563368/
+ CESA-2013:1156 Moderate CentOS 5 httpd Update
http://lwn.net/Alerts/563369/
+ Samba 3.6.18 Available for Download
http://samba.org/samba/history/samba-3.6.18.html
+ Oracle Java IntegerInterleavedRaster.verify() Signed Integer Overflow
http://cxsecurity.com/issue/WLB-2013080116
+ Apache Struts2 2.3.15 OGNL Injection
http://cxsecurity.com/issue/WLB-2013080115
+ Apache Struts2 2.3.15 Open Redirect
http://cxsecurity.com/issue/WLB-2013080111
+ SA54480 PHP SSL Module "subjectAltNames" NULL Byte Handling Security Issue
http://secunia.com/advisories/54480/
+ PHP SSL Certificate Validation Security Bypass Vulnerability
http://www.securityfocus.com/bid/61776
Advisory: Following an update to Sophos Anti-Virus the Sophos Anti-Virus service fails to start
http://www.sophos.com/en-us/support/knowledgebase/119717.aspx
JVNTA13-225A Microsoft 製品の複数の脆弱性に対するアップデート
http://jvn.jp/cert/JVNTA13-225A/
2013年8月14日水曜日
14日 水曜日、友引
+ 2013 年 8 月のセキュリティ情報
http://technet.microsoft.com/ja-jp/security/bulletin/ms13-aug
+ MS13-059 - 緊急 Internet Explorer 用の累積的なセキュリティ更新プログラム (2862772)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-059
http://www.securitytracker.com/id/1028902
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3184
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3186
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3187
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3188
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3189
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3190
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3191
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3192
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3193
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3194
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3199
+ MS13-060 - 緊急 Unicode スクリプト プロセッサの脆弱性により、リモートでコードが実行される (2850869)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-060
http://www.securitytracker.com/id/1028903
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3181
+ MS13-061 - 緊急 Microsoft Exchange Server の脆弱性により、リモートでコードが実行される (2876063)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-061
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2393
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3776
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3781
+ MS13-062 - 重要 リモート プロシージャ コールの脆弱性により、特権が昇格される (2849470)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-062
http://www.securitytracker.com/id/1028906
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3175
+ MS13-063 - 重要 Windows カーネルの脆弱性により、特権が昇格される (2859537)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-063
http://www.securitytracker.com/id/1028907
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2556
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3196
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3197
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3198
+ MS13-064 - 重要 Windows NAT ドライバーの脆弱性により、サービス拒否が起こる (2849568)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-064
http://www.securitytracker.com/id/1028909
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3182
+ MS13-065 - 重要 ICMPv6 の脆弱性により、サービス拒否が起こる (2868623)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-065
http://www.securitytracker.com/id/1028910
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3183
+ MS13-066 - 重要 Active Directory フェデレーション サービスの脆弱性により、情報漏えいが起こる (2873872)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-066
http://www.securitytracker.com/id/1028908
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3185
+ RHSA-2013:1156 Moderate: httpd security update
http://rhn.redhat.com/errata/RHSA-2013-1156.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1896
+ Microsoft Security Advisory (2862973) Update for Deprecation of MD5 Hashing Algorithm for Microsoft Root Certificate Program
http://technet.microsoft.com/en-us/security/advisory/2862973
+ Microsoft Security Advisory (2861855) Updates to Improve Remote Desktop Protocol Network-level Authentication
http://technet.microsoft.com/en-us/security/advisory/2861855
+ Microsoft Security Advisory (2854544) Updates to Improve Cryptography and Digital Certificate Handling in Windows
http://technet.microsoft.com/en-us/security/advisory/2854544
+ マイクロソフト セキュリティ アドバイザリ (2862973) マイクロソフト ルート証明書プログラムでの MD5 ハッシュ アルゴリズム廃止用の更新プログラム
http://technet.microsoft.com/ja-jp/security/advisory/2862973
+ マイクロソフト セキュリティ アドバイザリ (2861855) リモート デスクトップ プロトコルのネットワーク レベル認証を改善する更新プログラム
http://technet.microsoft.com/ja-jp/security/advisory/2861855
+ マイクロソフト セキュリティ アドバイザリ (2854544) Windows の暗号化とデジタル証明書の処理を改善するための更新プログラム
http://technet.microsoft.com/ja-jp/security/advisory/2854544
+ glibc 2.18 released
http://www.gnu.org/software/libc/index.html
sk94228 Check Point response to IPMI vulnerabilities
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk94228&src=securityAlerts
InterScan Web Security Suite 3.1 Solaris版 Patch 4 (build 1293) 公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=1996
JVNDB-2013-000077 サイボウズ メールワイズにおける情報漏えいの脆弱性
http://jvndb.jvn.jp/ja/contents/2013/JVNDB-2013-000077.html
JVN#21103639 サイボウズ メールワイズにおける情報漏えいの脆弱性
http://jvn.jp/jp/JVN21103639/
glibc Buffer overwrite when using readdir_r
http://cxsecurity.com/issue/WLB-2013080108
REMOTE: MinaliC Webserver 2.0.0 - Buffer Overflow (Egghunter)
http://www.exploit-db.com/exploits/27554
REMOTE: HP StorageWorks P4000 Virtual SAN Appliance Login Buffer Overflow
http://www.exploit-db.com/exploits/27555
REMOTE: Open-FTPD 1.2 Arbitrary File Upload
http://www.exploit-db.com/exploits/27556
DoS/PoC: onehttpd 0.7 - Denial of Service
http://www.exploit-db.com/exploits/27553
http://technet.microsoft.com/ja-jp/security/bulletin/ms13-aug
+ MS13-059 - 緊急 Internet Explorer 用の累積的なセキュリティ更新プログラム (2862772)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-059
http://www.securitytracker.com/id/1028902
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3184
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3186
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3187
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3188
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3189
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3190
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3191
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3192
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3193
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3194
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3199
+ MS13-060 - 緊急 Unicode スクリプト プロセッサの脆弱性により、リモートでコードが実行される (2850869)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-060
http://www.securitytracker.com/id/1028903
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3181
+ MS13-061 - 緊急 Microsoft Exchange Server の脆弱性により、リモートでコードが実行される (2876063)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-061
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2393
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3776
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3781
+ MS13-062 - 重要 リモート プロシージャ コールの脆弱性により、特権が昇格される (2849470)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-062
http://www.securitytracker.com/id/1028906
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3175
+ MS13-063 - 重要 Windows カーネルの脆弱性により、特権が昇格される (2859537)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-063
http://www.securitytracker.com/id/1028907
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2556
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3196
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3197
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3198
+ MS13-064 - 重要 Windows NAT ドライバーの脆弱性により、サービス拒否が起こる (2849568)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-064
http://www.securitytracker.com/id/1028909
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3182
+ MS13-065 - 重要 ICMPv6 の脆弱性により、サービス拒否が起こる (2868623)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-065
http://www.securitytracker.com/id/1028910
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3183
+ MS13-066 - 重要 Active Directory フェデレーション サービスの脆弱性により、情報漏えいが起こる (2873872)
https://technet.microsoft.com/ja-jp/security/bulletin/ms13-066
http://www.securitytracker.com/id/1028908
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3185
+ RHSA-2013:1156 Moderate: httpd security update
http://rhn.redhat.com/errata/RHSA-2013-1156.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1896
+ Microsoft Security Advisory (2862973) Update for Deprecation of MD5 Hashing Algorithm for Microsoft Root Certificate Program
http://technet.microsoft.com/en-us/security/advisory/2862973
+ Microsoft Security Advisory (2861855) Updates to Improve Remote Desktop Protocol Network-level Authentication
http://technet.microsoft.com/en-us/security/advisory/2861855
+ Microsoft Security Advisory (2854544) Updates to Improve Cryptography and Digital Certificate Handling in Windows
http://technet.microsoft.com/en-us/security/advisory/2854544
+ マイクロソフト セキュリティ アドバイザリ (2862973) マイクロソフト ルート証明書プログラムでの MD5 ハッシュ アルゴリズム廃止用の更新プログラム
http://technet.microsoft.com/ja-jp/security/advisory/2862973
+ マイクロソフト セキュリティ アドバイザリ (2861855) リモート デスクトップ プロトコルのネットワーク レベル認証を改善する更新プログラム
http://technet.microsoft.com/ja-jp/security/advisory/2861855
+ マイクロソフト セキュリティ アドバイザリ (2854544) Windows の暗号化とデジタル証明書の処理を改善するための更新プログラム
http://technet.microsoft.com/ja-jp/security/advisory/2854544
+ glibc 2.18 released
http://www.gnu.org/software/libc/index.html
sk94228 Check Point response to IPMI vulnerabilities
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk94228&src=securityAlerts
InterScan Web Security Suite 3.1 Solaris版 Patch 4 (build 1293) 公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=1996
JVNDB-2013-000077 サイボウズ メールワイズにおける情報漏えいの脆弱性
http://jvndb.jvn.jp/ja/contents/2013/JVNDB-2013-000077.html
JVN#21103639 サイボウズ メールワイズにおける情報漏えいの脆弱性
http://jvn.jp/jp/JVN21103639/
glibc Buffer overwrite when using readdir_r
http://cxsecurity.com/issue/WLB-2013080108
REMOTE: MinaliC Webserver 2.0.0 - Buffer Overflow (Egghunter)
http://www.exploit-db.com/exploits/27554
REMOTE: HP StorageWorks P4000 Virtual SAN Appliance Login Buffer Overflow
http://www.exploit-db.com/exploits/27555
REMOTE: Open-FTPD 1.2 Arbitrary File Upload
http://www.exploit-db.com/exploits/27556
DoS/PoC: onehttpd 0.7 - Denial of Service
http://www.exploit-db.com/exploits/27553
2013年8月13日火曜日
13日 火曜日、先勝
+ GCC 4.8.1 released
http://gcc.gnu.org/gcc-4.8/
+ curl and libcurl 7.32.0 released
http://curl.haxx.se/changes.html#7_32_0
+ SA54490: McAfee Multiple Products BIND RDATA Handling Assertion Failure Denial of Service Vulnerability
http://secunia.com/advisories/54490/
+ Oracle Java storeImageArray() Invalid Array Indexing
http://cxsecurity.com/issue/WLB-2013080102
+ GNU glibc CVE-2013-4237 Remote Buffer Overflow Vulnerability
http://www.securityfocus.com/bid/61729
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4237
Amebaに24万3266件の不正ログイン、ユーザー情報が閲覧された可能性
http://itpro.nikkeibp.co.jp/article/NEWS/20130813/498062/?ST=security
REMOTE: D-Link Devices Unauthenticated Remote Command Execution
http://www.exploit-db.com/exploits/27528
REMOTE: Sami FTP Server 2.0.1 - MKD Buffer Overflow ASLR Bypass (SEH)
http://www.exploit-db.com/exploits/27523
REMOTE: Oracle Java storeImageArray() Invalid Array Indexing
http://www.exploit-db.com/exploits/27526
REMOTE: Ruby on Rails Known Secret Session Cookie Remote Code Execution
http://www.exploit-db.com/exploits/27527
REMOTE: OpenX Backdoor PHP Code Execution
http://www.exploit-db.com/exploits/27529
REMOTE: Squash YAML Code Execution
http://www.exploit-db.com/exploits/27530
http://gcc.gnu.org/gcc-4.8/
+ curl and libcurl 7.32.0 released
http://curl.haxx.se/changes.html#7_32_0
+ SA54490: McAfee Multiple Products BIND RDATA Handling Assertion Failure Denial of Service Vulnerability
http://secunia.com/advisories/54490/
+ Oracle Java storeImageArray() Invalid Array Indexing
http://cxsecurity.com/issue/WLB-2013080102
+ GNU glibc CVE-2013-4237 Remote Buffer Overflow Vulnerability
http://www.securityfocus.com/bid/61729
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4237
Amebaに24万3266件の不正ログイン、ユーザー情報が閲覧された可能性
http://itpro.nikkeibp.co.jp/article/NEWS/20130813/498062/?ST=security
REMOTE: D-Link Devices Unauthenticated Remote Command Execution
http://www.exploit-db.com/exploits/27528
REMOTE: Sami FTP Server 2.0.1 - MKD Buffer Overflow ASLR Bypass (SEH)
http://www.exploit-db.com/exploits/27523
REMOTE: Oracle Java storeImageArray() Invalid Array Indexing
http://www.exploit-db.com/exploits/27526
REMOTE: Ruby on Rails Known Secret Session Cookie Remote Code Execution
http://www.exploit-db.com/exploits/27527
REMOTE: OpenX Backdoor PHP Code Execution
http://www.exploit-db.com/exploits/27529
REMOTE: Squash YAML Code Execution
http://www.exploit-db.com/exploits/27530
2013年8月12日月曜日
12日 月曜日、赤口
+ Selenium IDE 2.3.0 released
https://code.google.com/p/selenium/wiki/SeIDEReleaseNotes
+ CESA-2013:1142 Important CentOS 6 thunderbird Update
http://lwn.net/Alerts/562868/
+ UPDATE: Cisco TelePresence System Default Credentials Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130807-tp
+ UPDATE: OSPF LSA Manipulation Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130801-lsaospf
+ UPDATE: HPSBUX02450 SSRT090141 rev.2 - HP-UX ttrace(2), Local Denial of Service (DoS)
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c01832652-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ php 5.3.26 heap corruption in the XML parser
http://cxsecurity.com/issue/WLB-2013070090
+ Linux Kernel ARM64 "el0_sync_compat" Handler Denial of Service Vulnerability
http://secunia.com/advisories/54187/
+ Linux Kernel "unshare_userns()" Denial of Service Vulnerability
http://secunia.com/advisories/54395/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4205
+ Linux Kernel CVE-2013-4220 Multiple Local Denial of Service Vulnerabilities
http://www.securityfocus.com/bid/61698
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4220
インタビュー&トークITpro
“守り”に入ったセキュリティ部門は捨てられる
http://itpro.nikkeibp.co.jp/article/Interview/20130809/497716/?ST=security
「じゃらんnet」で2万7620件の不正アクセス、予約履歴など漏洩の恐れ
http://itpro.nikkeibp.co.jp/article/NEWS/20130809/497702/?ST=security
BlackBerry、BB10端末が米国防総省のセキュリティ認定を取得
http://itpro.nikkeibp.co.jp/article/NEWS/20130809/497669/?ST=security
【夏休みスペシャル2013】
依存、いじめ、出会い――ネット、スマホの負の側面と親はどう戦う
http://itpro.nikkeibp.co.jp/article/COLUMN/20130802/496322/?ST=security
【夏休みスペシャル2013】
夏休みに見たいICT関連の映画DVD
http://itpro.nikkeibp.co.jp/article/COLUMN/20130806/496865/?ST=security
JVNVU#90202792 HP/H3C 製および Huawei 製ネットワーク機器がパスワードの暗号化に DES を使用している問題
http://jvn.jp/cert/JVNVU90202792/
2013年8月9日金曜日
9日 金曜日、先負
+ マイクロソフト セキュリティ情報の事前通知 - 2013 年 8 月
http://technet.microsoft.com/ja-jp/security/bulletin/ms13-aug
+ CESA-2013:1144 Moderate CentOS 6 nss, nss-util, nss-softokn, and nspr Update
http://lwn.net/Alerts/562649/
+ CESA-2013:1142 Important CentOS 5 thunderbird Update
http://lwn.net/Alerts/562650/
+ HPSBHF02912 rev.1 - HP Networking Products including H3C and 3COM Routers and Switches, OSPF Remote Information Disclosure and Denial of Service
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03880910-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HP Data Protector Arbitrary Remote Command Execution
http://cxsecurity.com/issue/WLB-2013080082
+ Firefox 20.0.1 Use After Free Vulnerability
http://cxsecurity.com/issue/WLB-2013080081
+ Firefox onreadystatechange Event DocumentViewerImpl Use After Free
http://cxsecurity.com/issue/WLB-2013080080
+ REMOTE: D-Link Devices Unauthenticated Remote Command Execution
http://www.exploit-db.com/exploits/27428
+ Firefox onreadystatechange Event DocumentViewerImpl Use After Free
http://www.exploit-db.com/exploits/27429
Trend Micro Security (for Mac) 2.0 公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=1992
【デジタル世界の知られざる真相、米国10代のネット事情】
第5回:安易な「過剰な個人情報」の投稿、青少年に警鐘
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495369/?ST=security
GREEに3万9590件の不正ログイン、対象アカウントを一時停止
http://itpro.nikkeibp.co.jp/article/NEWS/20130808/497543/?ST=security
ワンビが紛失PCの遠隔消去サービスを強化、一定期間後にPCをロック
http://itpro.nikkeibp.co.jp/article/NEWS/20130808/497463/?ST=security
ピーエスシー、Webサイトの脆弱性をリモート診断するスポットサービスを開始
http://itpro.nikkeibp.co.jp/article/NEWS/20130808/497403/?ST=security
http://technet.microsoft.com/ja-jp/security/bulletin/ms13-aug
+ CESA-2013:1144 Moderate CentOS 6 nss, nss-util, nss-softokn, and nspr Update
http://lwn.net/Alerts/562649/
+ CESA-2013:1142 Important CentOS 5 thunderbird Update
http://lwn.net/Alerts/562650/
+ HPSBHF02912 rev.1 - HP Networking Products including H3C and 3COM Routers and Switches, OSPF Remote Information Disclosure and Denial of Service
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03880910-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HP Data Protector Arbitrary Remote Command Execution
http://cxsecurity.com/issue/WLB-2013080082
+ Firefox 20.0.1 Use After Free Vulnerability
http://cxsecurity.com/issue/WLB-2013080081
+ Firefox onreadystatechange Event DocumentViewerImpl Use After Free
http://cxsecurity.com/issue/WLB-2013080080
+ REMOTE: D-Link Devices Unauthenticated Remote Command Execution
http://www.exploit-db.com/exploits/27428
+ Firefox onreadystatechange Event DocumentViewerImpl Use After Free
http://www.exploit-db.com/exploits/27429
Trend Micro Security (for Mac) 2.0 公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=1992
【デジタル世界の知られざる真相、米国10代のネット事情】
第5回:安易な「過剰な個人情報」の投稿、青少年に警鐘
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495369/?ST=security
GREEに3万9590件の不正ログイン、対象アカウントを一時停止
http://itpro.nikkeibp.co.jp/article/NEWS/20130808/497543/?ST=security
ワンビが紛失PCの遠隔消去サービスを強化、一定期間後にPCをロック
http://itpro.nikkeibp.co.jp/article/NEWS/20130808/497463/?ST=security
ピーエスシー、Webサイトの脆弱性をリモート診断するスポットサービスを開始
http://itpro.nikkeibp.co.jp/article/NEWS/20130808/497403/?ST=security
2013年8月8日木曜日
Mantis Bug Tracker インストールメモ
Mantis Bug Tracker を Windows の 64 ビット環境に構築したインストールメモです。
0. 前提条件
動作環境 Windows 7 Professional SP1 (x64)
1. パッケージの入手
1. パッケージの入手
- MySQL 5.6.13 (32,64共通)
http://dev.mysql.com/downloads/installer/5.6.html
ファイル名:mysql-installer-community-5.6.13.0.msi - Visual Studio 2012 更新プログラム 3 の Visual C++ 再頒布可能パッケージ
http://www.microsoft.com/ja-jp/download/details.aspx?id=30679
ファイル名:vcredist_x64.exe
※ VC11版 PHP、Apache HTTPD 実行に必要 - PHP 5.5.1 (VC11,x64版)
http://windows.php.net/download/
ファイル名:php-5.5.1-Win32-VC11-x64.zip - Apache HTTPD 2.4.6 (VC11,x64版)
http://www.apachelounge.com/download/VC11/
ファイル名:httpd-2.4.6-win64-VC11.zip - Mantis Bug Tracker 1.2.15
http://sourceforge.net/projects/mantisbt/files/mantis-stable/
ファイル名:mantisbt-1.2.15.zip
2. インストール
- MySQL
- msi パッケージを実行、画面の要求に沿って進める。
- root のアカウントに注意。
- 追加アカウントはとりあえず「なし」
- Visual C++ パッケージ
- exe を実行
- PHP
- zip ファイルを解凍して C:\PHP に移動。
- C:\PHP にある php.ini-production を php.ini にコピー
- php.ini を編集
doc_root = "c:\Apache24\htdocs"
extension_dir = "C:\PHP\ext"
upload_max_filesize = 5M
extension=php_gd2.dll
extension=php_mbstring.dll
extension=php_mysql.dll
date.timezone = Asia/Tokyo
session.save_path = "C:/tmp"
- Apache HTTPD
- zip ファイルを解凍して C:\Apache24 に移動。
- C:\Apache24\conf\httpd.conf を編集
LoadModule php5_module "C:/PHP/php5apache2_4.dll"
PHPIniDir "C:/PHP"
ServerAdmin foo@example.com
ServerName localhost:80
<IfModule dir_module>
DirectoryIndex index.html index.php
</IfModule>
<IfModule mime_module>
...
AddType application/x-httpd-php .php
</IfModule>
- "C:\Apache24\bin\httpd.exe -k install" でサービス追加。
- "C:\Apache24\bin\httpd.exe -k start" サービス開始。
- C:\Apache24\bin\ApacheMonitor.exe を「スタートアップ」に追加。
- http://localhost/ で "It works !" と表示されることを確認。
- Apache Monitor を status bar に "Apache/2.4.6 (Win64) PHP/5.5.1" と表示されていることを確認。
- Mantis Bug Tracker
- zip ファイルを解凍して C:\Apache24\htdocs\mantisbt にコピー
- http://localhost/mantisbt/admin/install.php を開く。
- "Password (for Database) を入力して [Install/Upgrade Database] ボタンを押す。
すべて "GOOD" となることを確認。"BAD" が出たらその内容を対処。 - http://localhost/mantisbt/admin/check.php を開いてエラーがないことを確認。
- C:\Apache24\htdocs\mantisbt\admin を削除または名前を変更する。
- C:\Apache24\htdocs\mantisbt\config_inc.php を編集
$g_default_language = 'japanese';
- http://localhost/mantisbt/ を開き、日本語化されたログイン画面が表示されることを確認。
画面ショットもない手順で申し訳ないが、これで一応 Mantis Bug Tracker は動作可能となった。あとは、Mantis BT の使い方であるが、それは多くの情報があるだろうからそちらに譲ることとする。
-以上-
8日 木曜日、友引
+ RHSA-2013:1144 Moderate: nss, nss-util, nss-softokn, and nspr security update
http://rhn.redhat.com/errata/RHSA-2013-1144.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0791
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1620
+ RHSA-2013:1142 Important: thunderbird security update
http://rhn.redhat.com/errata/RHSA-2013-1142.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1701
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1709
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1710
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1713
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1714
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1717
+ RHSA-2013:1140 Critical: firefox security update
http://rhn.redhat.com/errata/RHSA-2013-1140.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1701
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1709
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1710
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1713
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1714
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1717
+ CESA-2013:1140 Critical CentOS 5 firefox Update
http://lwn.net/Alerts/562424/
+ CESA-2013:1140 Critical CentOS 6 firefox Update
http://lwn.net/Alerts/562425/
+ Cisco TelePresence System Default Credentials Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130807-tp
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3454
+ iptables 1.4.20 released
http://www.hu.netfilter.org/projects/iptables/downloads.html#iptables-1.4.20
http://www.hu.netfilter.org/projects/iptables/files/changes-iptables-1.4.20.txt
+ REMOTE: Apache suEXEC Privilege Elevation / Information Disclosure
http://www.exploit-db.com/exploits/27397
+ REMOTE: HP Data Protector Arbitrary Remote Command Execution
http://www.exploit-db.com/exploits/27400
+ Apache suEXEC privilege elevation / information disclosure
http://cxsecurity.com/issue/WLB-2013080067
+ Microsoft Yammer Social Network oAuth Bypass (Session Token) Vulnerability
http://cxsecurity.com/issue/WLB-2013080059
+ McAfee Superscan 4.0 Cross Site Scripting
http://cxsecurity.com/issue/WLB-2013080058
+ Facebook Friends Disclosure
http://cxsecurity.com/issue/WLB-2013080056
JVNDB-2013-000075 ドコモ海外利用アプリにおける接続処理に関する脆弱性
http://jvndb.jvn.jp/ja/contents/2013/JVNDB-2013-000075.html
最新サイバー攻撃に備えるITpro
ユーザーIDの役割を分離する
http://itpro.nikkeibp.co.jp/article/COLUMN/20130807/497103/?ST=security
【デジタル世界の知られざる真相、米国10代のネット事情】
第4回:いじめとカンニングの温床に、ネットの負の側面
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495368/?ST=security
FFRI、複数環境で並行解析できるマルウエア解析ツール新版を出荷
http://itpro.nikkeibp.co.jp/article/NEWS/20130807/497242/?ST=security
アシストが特権IDの利用申請パックを強化、申請外ログインを検知可能に
http://itpro.nikkeibp.co.jp/article/NEWS/20130807/497142/?ST=security
JVN#44035194 ドコモ海外利用アプリにおける接続処理に関する脆弱性
http://jvn.jp/jp/JVN44035194/
REMOTE: Open&Compact FTP Server 1.2 - Auth Bypass & Directory Traversal SAM Retrieval Exploit
http://www.exploit-db.com/exploits/27401
http://rhn.redhat.com/errata/RHSA-2013-1144.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0791
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1620
+ RHSA-2013:1142 Important: thunderbird security update
http://rhn.redhat.com/errata/RHSA-2013-1142.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1701
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1709
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1710
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1713
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1714
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1717
+ RHSA-2013:1140 Critical: firefox security update
http://rhn.redhat.com/errata/RHSA-2013-1140.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1701
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1709
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1710
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1713
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1714
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1717
+ CESA-2013:1140 Critical CentOS 5 firefox Update
http://lwn.net/Alerts/562424/
+ CESA-2013:1140 Critical CentOS 6 firefox Update
http://lwn.net/Alerts/562425/
+ Cisco TelePresence System Default Credentials Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130807-tp
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3454
+ iptables 1.4.20 released
http://www.hu.netfilter.org/projects/iptables/downloads.html#iptables-1.4.20
http://www.hu.netfilter.org/projects/iptables/files/changes-iptables-1.4.20.txt
+ REMOTE: Apache suEXEC Privilege Elevation / Information Disclosure
http://www.exploit-db.com/exploits/27397
+ REMOTE: HP Data Protector Arbitrary Remote Command Execution
http://www.exploit-db.com/exploits/27400
+ Apache suEXEC privilege elevation / information disclosure
http://cxsecurity.com/issue/WLB-2013080067
+ Microsoft Yammer Social Network oAuth Bypass (Session Token) Vulnerability
http://cxsecurity.com/issue/WLB-2013080059
+ McAfee Superscan 4.0 Cross Site Scripting
http://cxsecurity.com/issue/WLB-2013080058
+ Facebook Friends Disclosure
http://cxsecurity.com/issue/WLB-2013080056
JVNDB-2013-000075 ドコモ海外利用アプリにおける接続処理に関する脆弱性
http://jvndb.jvn.jp/ja/contents/2013/JVNDB-2013-000075.html
最新サイバー攻撃に備えるITpro
ユーザーIDの役割を分離する
http://itpro.nikkeibp.co.jp/article/COLUMN/20130807/497103/?ST=security
【デジタル世界の知られざる真相、米国10代のネット事情】
第4回:いじめとカンニングの温床に、ネットの負の側面
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495368/?ST=security
FFRI、複数環境で並行解析できるマルウエア解析ツール新版を出荷
http://itpro.nikkeibp.co.jp/article/NEWS/20130807/497242/?ST=security
アシストが特権IDの利用申請パックを強化、申請外ログインを検知可能に
http://itpro.nikkeibp.co.jp/article/NEWS/20130807/497142/?ST=security
JVN#44035194 ドコモ海外利用アプリにおける接続処理に関する脆弱性
http://jvn.jp/jp/JVN44035194/
REMOTE: Open&Compact FTP Server 1.2 - Auth Bypass & Directory Traversal SAM Retrieval Exploit
http://www.exploit-db.com/exploits/27401
2013年8月7日水曜日
7日 水曜日、先勝
+ Selenium Server (formerly the Selenium RC Server) 2.34.0 released
http://docs.seleniumhq.org/download/
+ Seleniumu: The Internet Explorer Driver Server 2.34.0 released
http://docs.seleniumhq.org/download/
+ Selenium Client & WebDriver Language Bindings 2.34.0 released
http://docs.seleniumhq.org/download/
+ Mozilla Firefox 23 released
http://www.mozilla.org/en-US/firefox/23.0/releasenotes/
+ Mozilla Thunderbird 17.0.8 released
http://www.mozilla.org/en-US/thunderbird/17.0.8/releasenotes/
+ MFSA 2013-75 Local Java applets may read contents of local file system
http://www.mozilla.org/security/announce/2013/mfsa2013-75.html
+ MFSA 2013-74 Firefox full and stub installer DLL hijacking
http://www.mozilla.org/security/announce/2013/mfsa2013-74.html
+ MFSA 2013-73 Same-origin bypass with web workers and XMLHttpRequest
http://www.mozilla.org/security/announce/2013/mfsa2013-73.html
+ MFSA 2013-72 Wrong principal used for validating URI for some Javascript components
http://www.mozilla.org/security/announce/2013/mfsa2013-72.html
+ MFSA 2013-71 Further Privilege escalation through Mozilla Updater
http://www.mozilla.org/security/announce/2013/mfsa2013-71.html
+ MFSA 2013-70 Bypass of XrayWrappers using XBL Scopes
http://www.mozilla.org/security/announce/2013/mfsa2013-70.html
+ MFSA 2013-69 CRMF requests allow for code execution and XSS attacks
http://www.mozilla.org/security/announce/2013/mfsa2013-69.html
+ MFSA 2013-68 Document URI misrepresentation and masquerading
http://www.mozilla.org/security/announce/2013/mfsa2013-68.html
+ MFSA 2013-67 Crash during WAV audio file decoding
http://www.mozilla.org/security/announce/2013/mfsa2013-67.html
+ MFSA 2013-66 Buffer overflow in Mozilla Maintenance Service and Mozilla Updater
http://www.mozilla.org/security/announce/2013/mfsa2013-66.html
+ MFSA 2013-65 Buffer underflow when generating CRMF requests
http://www.mozilla.org/security/announce/2013/mfsa2013-65.html
+ MFSA 2013-64 Use after free mutating DOM during SetBody
http://www.mozilla.org/security/announce/2013/mfsa2013-64.html
+ MFSA 2013-63 Miscellaneous memory safety hazards (rv:23.0 / rv:17.0.8)
http://www.mozilla.org/security/announce/2013/mfsa2013-63.html
+ CESA-2013:1135 Moderate CentOS 5 nss Update
http://lwn.net/Alerts/562258/
+ Mozilla Thunderbird Multiple Bugs Let Remote Users Execute Arbitrary Code and Conduct Cross-Site Scripting Attacks and Let Local Users Obtain Files
http://www.securitytracker.com/id/1028887
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1701
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1702
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1706
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1707
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1709
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1710
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1712
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1713
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1714
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1717
+ Mozilla Firefox Multiple Bugs Let Remote Users Execute Arbitrary Code and Conduct Cross-Site Scripting Attacks and Let Local Users Obtain Files
http://www.securitytracker.com/id/1028885
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1701
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1702
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1704
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1705
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1706
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1707
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1708
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1709
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1710
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1711
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1712
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1713
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1714
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1715
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1717
+ PuTTY 0.62 Heap Overflow
http://cxsecurity.com/issue/WLB-2013080054
+ Linux Kernel MSR Driver Privilege Escalation
http://cxsecurity.com/issue/WLB-2013080050
+ Linux Kernel CVE-2013-4205 Local Denial of Service Vulnerability
http://www.securityfocus.com/bid/61636
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4205
ウイルスバスター ビジネスセキュリティ 7.0 Service Pack1 Patch2公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=1995
世界のセキュリティ・ラボから
標的型攻撃の検出支援システム
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495465/?ST=security
ネットワーク・ホットトピックス
カーネルに権限昇格バグが見つかる、Android 4.0~4.2系では要注意
http://itpro.nikkeibp.co.jp/article/COLUMN/20130723/493624/?ST=security
スマホ少女の憂鬱、スマホ少年の暴走~今、10代が危ない
第10回 「ネット依存の中高生が約52万人」の波紋、スマホで増幅される依存の連鎖
http://itpro.nikkeibp.co.jp/article/COLUMN/20130805/496708/?ST=security
【デジタル世界の知られざる真相、米国10代のネット事情】
第3回:「開かれた世界」へとティーンを誘うソーシャル
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495367/?ST=security
JVNVU#94916481 HTTPS レスポンスから暗号化されたデータの一部を推測可能な脆弱性 (BREACH)
http://jvn.jp/cert/JVNVU94916481/
http://docs.seleniumhq.org/download/
+ Seleniumu: The Internet Explorer Driver Server 2.34.0 released
http://docs.seleniumhq.org/download/
+ Selenium Client & WebDriver Language Bindings 2.34.0 released
http://docs.seleniumhq.org/download/
+ Mozilla Firefox 23 released
http://www.mozilla.org/en-US/firefox/23.0/releasenotes/
+ Mozilla Thunderbird 17.0.8 released
http://www.mozilla.org/en-US/thunderbird/17.0.8/releasenotes/
+ MFSA 2013-75 Local Java applets may read contents of local file system
http://www.mozilla.org/security/announce/2013/mfsa2013-75.html
+ MFSA 2013-74 Firefox full and stub installer DLL hijacking
http://www.mozilla.org/security/announce/2013/mfsa2013-74.html
+ MFSA 2013-73 Same-origin bypass with web workers and XMLHttpRequest
http://www.mozilla.org/security/announce/2013/mfsa2013-73.html
+ MFSA 2013-72 Wrong principal used for validating URI for some Javascript components
http://www.mozilla.org/security/announce/2013/mfsa2013-72.html
+ MFSA 2013-71 Further Privilege escalation through Mozilla Updater
http://www.mozilla.org/security/announce/2013/mfsa2013-71.html
+ MFSA 2013-70 Bypass of XrayWrappers using XBL Scopes
http://www.mozilla.org/security/announce/2013/mfsa2013-70.html
+ MFSA 2013-69 CRMF requests allow for code execution and XSS attacks
http://www.mozilla.org/security/announce/2013/mfsa2013-69.html
+ MFSA 2013-68 Document URI misrepresentation and masquerading
http://www.mozilla.org/security/announce/2013/mfsa2013-68.html
+ MFSA 2013-67 Crash during WAV audio file decoding
http://www.mozilla.org/security/announce/2013/mfsa2013-67.html
+ MFSA 2013-66 Buffer overflow in Mozilla Maintenance Service and Mozilla Updater
http://www.mozilla.org/security/announce/2013/mfsa2013-66.html
+ MFSA 2013-65 Buffer underflow when generating CRMF requests
http://www.mozilla.org/security/announce/2013/mfsa2013-65.html
+ MFSA 2013-64 Use after free mutating DOM during SetBody
http://www.mozilla.org/security/announce/2013/mfsa2013-64.html
+ MFSA 2013-63 Miscellaneous memory safety hazards (rv:23.0 / rv:17.0.8)
http://www.mozilla.org/security/announce/2013/mfsa2013-63.html
+ CESA-2013:1135 Moderate CentOS 5 nss Update
http://lwn.net/Alerts/562258/
+ Mozilla Thunderbird Multiple Bugs Let Remote Users Execute Arbitrary Code and Conduct Cross-Site Scripting Attacks and Let Local Users Obtain Files
http://www.securitytracker.com/id/1028887
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1701
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1702
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1706
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1707
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1709
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1710
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1712
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1713
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1714
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1717
+ Mozilla Firefox Multiple Bugs Let Remote Users Execute Arbitrary Code and Conduct Cross-Site Scripting Attacks and Let Local Users Obtain Files
http://www.securitytracker.com/id/1028885
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1701
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1702
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1704
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1705
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1706
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1707
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1708
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1709
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1710
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1711
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1712
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1713
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1714
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1715
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1717
+ PuTTY 0.62 Heap Overflow
http://cxsecurity.com/issue/WLB-2013080054
+ Linux Kernel MSR Driver Privilege Escalation
http://cxsecurity.com/issue/WLB-2013080050
+ Linux Kernel CVE-2013-4205 Local Denial of Service Vulnerability
http://www.securityfocus.com/bid/61636
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4205
ウイルスバスター ビジネスセキュリティ 7.0 Service Pack1 Patch2公開のお知らせ
http://www.trendmicro.co.jp/support/news.asp?id=1995
世界のセキュリティ・ラボから
標的型攻撃の検出支援システム
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495465/?ST=security
ネットワーク・ホットトピックス
カーネルに権限昇格バグが見つかる、Android 4.0~4.2系では要注意
http://itpro.nikkeibp.co.jp/article/COLUMN/20130723/493624/?ST=security
スマホ少女の憂鬱、スマホ少年の暴走~今、10代が危ない
第10回 「ネット依存の中高生が約52万人」の波紋、スマホで増幅される依存の連鎖
http://itpro.nikkeibp.co.jp/article/COLUMN/20130805/496708/?ST=security
【デジタル世界の知られざる真相、米国10代のネット事情】
第3回:「開かれた世界」へとティーンを誘うソーシャル
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495367/?ST=security
JVNVU#94916481 HTTPS レスポンスから暗号化されたデータの一部を推測可能な脆弱性 (BREACH)
http://jvn.jp/cert/JVNVU94916481/
2013年8月6日火曜日
6日 火曜日、大安
+ UPDATE: OSPF LSA Manipulation Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130801-lsaospf
+ マイクロソフト セキュリティ アドバイザリ (2876146) ワイヤレス PEAP-MS-CHAPv2 認証により、情報漏えいが起こる可能性がある
http://technet.microsoft.com/ja-jp/security/advisory/2876146
+ RHSA-2013:1135 Moderate: nss and nspr security, bug fix, and enhancement update
http://rhn.redhat.com/errata/RHSA-2013-1135.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0791
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1620
+ Dovecot 2.2.5 released
http://www.dovecot.org/list/dovecot-news/2013-August/000261.html
+ Samba 4.0.8, 3.6.17, 3.5.22 released
http://samba.org/samba/history/samba-4.0.8.html
http://samba.org/samba/history/samba-3.6.17.html
http://samba.org/samba/history/samba-3.5.22.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4124
+ Samba smbd CPU Processing Loop Lets Remote Users Deny Service
http://www.securitytracker.com/id/1028882
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4124
+ Windows Phone PEAP-MS-CHAPv2 Authentication Protocol Weakness May Let Remote Users Obtain Authentication Information
http://www.securitytracker.com/id/1028874
+ Google Web Toolkit (GWT) XSS
http://cxsecurity.com/issue/WLB-2013080038
+ SA54354 PuTTY SSH Handshake Integer Overflow Vulnerabilities
http://secunia.com/advisories/54354/
+ SA54409 phpMyAdmin Clickjacking Vulnerability
http://secunia.com/advisories/54409/
+ SA54381 phpMyAdmin Clickjacking Vulnerability
http://secunia.com/advisories/54381/
+ PuTTY 'getstring()' Function Multiple Integer Overflow Vulnerabilities
http://www.securityfocus.com/bid/61599
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4852
+ Samba CVE-2013-4124 Local Denial of Service Vulnerability
http://www.securityfocus.com/bid/61597
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4124
+ Microsoft Windows Phone PEAP-MS-CHAPv2 Authentication Protocol Security Weakness
http://www.securityfocus.com/bid/61592
【デジタル世界の知られざる真相、米国10代のネット事情】
第2回:スマートデバイスに精通、驚くべき10代の行動
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495366/?ST=security
富士通研究所、手のひら静脈認証で特徴をビット化する新技術を発表
http://itpro.nikkeibp.co.jp/article/NEWS/20130805/496692/?ST=security
JVNVU#94916481 HTTPS レスポンスから暗号化されたデータの一部を推測可能な脆弱性 (BREACH)
http://jvn.jp/cert/JVNVU94916481/index.html
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130801-lsaospf
+ マイクロソフト セキュリティ アドバイザリ (2876146) ワイヤレス PEAP-MS-CHAPv2 認証により、情報漏えいが起こる可能性がある
http://technet.microsoft.com/ja-jp/security/advisory/2876146
+ RHSA-2013:1135 Moderate: nss and nspr security, bug fix, and enhancement update
http://rhn.redhat.com/errata/RHSA-2013-1135.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0791
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1620
+ Dovecot 2.2.5 released
http://www.dovecot.org/list/dovecot-news/2013-August/000261.html
+ Samba 4.0.8, 3.6.17, 3.5.22 released
http://samba.org/samba/history/samba-4.0.8.html
http://samba.org/samba/history/samba-3.6.17.html
http://samba.org/samba/history/samba-3.5.22.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4124
+ Samba smbd CPU Processing Loop Lets Remote Users Deny Service
http://www.securitytracker.com/id/1028882
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4124
+ Windows Phone PEAP-MS-CHAPv2 Authentication Protocol Weakness May Let Remote Users Obtain Authentication Information
http://www.securitytracker.com/id/1028874
+ Google Web Toolkit (GWT) XSS
http://cxsecurity.com/issue/WLB-2013080038
+ SA54354 PuTTY SSH Handshake Integer Overflow Vulnerabilities
http://secunia.com/advisories/54354/
+ SA54409 phpMyAdmin Clickjacking Vulnerability
http://secunia.com/advisories/54409/
+ SA54381 phpMyAdmin Clickjacking Vulnerability
http://secunia.com/advisories/54381/
+ PuTTY 'getstring()' Function Multiple Integer Overflow Vulnerabilities
http://www.securityfocus.com/bid/61599
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4852
+ Samba CVE-2013-4124 Local Denial of Service Vulnerability
http://www.securityfocus.com/bid/61597
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4124
+ Microsoft Windows Phone PEAP-MS-CHAPv2 Authentication Protocol Security Weakness
http://www.securityfocus.com/bid/61592
【デジタル世界の知られざる真相、米国10代のネット事情】
第2回:スマートデバイスに精通、驚くべき10代の行動
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495366/?ST=security
富士通研究所、手のひら静脈認証で特徴をビット化する新技術を発表
http://itpro.nikkeibp.co.jp/article/NEWS/20130805/496692/?ST=security
JVNVU#94916481 HTTPS レスポンスから暗号化されたデータの一部を推測可能な脆弱性 (BREACH)
http://jvn.jp/cert/JVNVU94916481/index.html
2013年8月5日月曜日
5日 月曜日、仏滅
+ phpMyAdmin 4.0.5 is released
http://sourceforge.net/p/phpmyadmin/news/2013/08/phpmyadmin-405-is-released/
+ SYM13-011 Symantec Workspace Virtualization のローカルカーネルに特権昇格の問題
http://www.symantec.com/ja/jp/security_response/securityupdates/detail.jsp?fid=security_advisory&pvid=security_advisory&year=&suid=20130801_02
+ Apache Struts Bugs Permit Remote Code Execution and URL Redirection Attacks
http://www.securitytracker.com/id/1028865
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2248
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2251
+ Apache Struts Wildcard Matching and Expression Evaluation Bugs Let Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1028864
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2134
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2135
+ Symantec Encryption Desktop CVE-2013-1610 Local Privilege Escalation Vulnerability
http://www.securityfocus.com/bid/61489
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1610
+ Symantec Backup Exec CVE-2013-4575 Remote Heap Buffer Overflow Vulnerability
http://www.securityfocus.com/bid/61485
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4575
+ Symantec Backup Exec CVE-2013-4677 Local Insecure File Permissions Vulnerability
http://www.securityfocus.com/bid/61487
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4677
+ Symantec Backup Exec CVE-2013-4676 Multiple Cross Site Scripting Vulnerabilities
http://www.securityfocus.com/bid/61486
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4676
+ Symantec Backup Exec CVE-2013-4678 Information Disclosure Vulnerability
http://www.securityfocus.com/bid/61488
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4678
Check Point response to HTTPS BREACH attack
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk93971&src=securityAlerts
JVNDB-2013-000076 JP1/IT Desktop Management - Manager および Hitachi IT Operations Director における権限昇格の脆弱性
http://jvndb.jvn.jp/ja/contents/2013/JVNDB-2013-000076.html
チェックしておきたい脆弱性情報<2013.8.5>
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495463/?ST=security
APT攻撃対策、ネットワーク内を動き回る脅威を検出するには
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495464/?ST=security
【デジタル世界の知られざる真相、米国10代のネット事情】
第1回:親と子がオンラインで断絶する米国、その実態は
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495365/?ST=security
NAVERへの不正アクセス、侵入者を特定し流出データ約170万件を削除
http://itpro.nikkeibp.co.jp/article/NEWS/20130802/496342/?ST=security
[続報]オプトアウト受付は既に8800件、Suica履歴提供の仕組みをJR東日本に改めて聞く
http://itpro.nikkeibp.co.jp/article/NEWS/20130802/496182/?ST=security
米政府の監視活動、電子メールやチャットの内容も閲覧---英紙が報道
http://itpro.nikkeibp.co.jp/article/NEWS/20130802/496202/?ST=security
JVNVU#96465452 Open Shortest Path First (OSPF) プロトコルの Link State Advertisement (LSA) に関する問題
http://jvn.jp/cert/JVNVU96465452/index.html
VU#987798 BREACH vulnerability in compressed HTTPS
http://www.kb.cert.org/vuls/id/987798
REMOTE: Easy LAN Folder Share Version 3.2.0.100 - Buffer Overflow Exploit (SEH)
http://www.exploit-db.com/exploits/27316
DoS/PoC: StarUML WinGraphviz.dll - ActiveX Buffer Overflow Vulnerability
http://www.exploit-db.com/exploits/27317
http://sourceforge.net/p/phpmyadmin/news/2013/08/phpmyadmin-405-is-released/
+ SYM13-011 Symantec Workspace Virtualization のローカルカーネルに特権昇格の問題
http://www.symantec.com/ja/jp/security_response/securityupdates/detail.jsp?fid=security_advisory&pvid=security_advisory&year=&suid=20130801_02
+ Apache Struts Bugs Permit Remote Code Execution and URL Redirection Attacks
http://www.securitytracker.com/id/1028865
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2248
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2251
+ Apache Struts Wildcard Matching and Expression Evaluation Bugs Let Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1028864
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2134
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2135
+ Symantec Encryption Desktop CVE-2013-1610 Local Privilege Escalation Vulnerability
http://www.securityfocus.com/bid/61489
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1610
+ Symantec Backup Exec CVE-2013-4575 Remote Heap Buffer Overflow Vulnerability
http://www.securityfocus.com/bid/61485
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4575
+ Symantec Backup Exec CVE-2013-4677 Local Insecure File Permissions Vulnerability
http://www.securityfocus.com/bid/61487
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4677
+ Symantec Backup Exec CVE-2013-4676 Multiple Cross Site Scripting Vulnerabilities
http://www.securityfocus.com/bid/61486
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4676
+ Symantec Backup Exec CVE-2013-4678 Information Disclosure Vulnerability
http://www.securityfocus.com/bid/61488
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4678
Check Point response to HTTPS BREACH attack
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk93971&src=securityAlerts
JVNDB-2013-000076 JP1/IT Desktop Management - Manager および Hitachi IT Operations Director における権限昇格の脆弱性
http://jvndb.jvn.jp/ja/contents/2013/JVNDB-2013-000076.html
チェックしておきたい脆弱性情報<2013.8.5>
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495463/?ST=security
APT攻撃対策、ネットワーク内を動き回る脅威を検出するには
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495464/?ST=security
【デジタル世界の知られざる真相、米国10代のネット事情】
第1回:親と子がオンラインで断絶する米国、その実態は
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495365/?ST=security
NAVERへの不正アクセス、侵入者を特定し流出データ約170万件を削除
http://itpro.nikkeibp.co.jp/article/NEWS/20130802/496342/?ST=security
[続報]オプトアウト受付は既に8800件、Suica履歴提供の仕組みをJR東日本に改めて聞く
http://itpro.nikkeibp.co.jp/article/NEWS/20130802/496182/?ST=security
米政府の監視活動、電子メールやチャットの内容も閲覧---英紙が報道
http://itpro.nikkeibp.co.jp/article/NEWS/20130802/496202/?ST=security
JVNVU#96465452 Open Shortest Path First (OSPF) プロトコルの Link State Advertisement (LSA) に関する問題
http://jvn.jp/cert/JVNVU96465452/index.html
VU#987798 BREACH vulnerability in compressed HTTPS
http://www.kb.cert.org/vuls/id/987798
REMOTE: Easy LAN Folder Share Version 3.2.0.100 - Buffer Overflow Exploit (SEH)
http://www.exploit-db.com/exploits/27316
DoS/PoC: StarUML WinGraphviz.dll - ActiveX Buffer Overflow Vulnerability
http://www.exploit-db.com/exploits/27317
2013年8月2日金曜日
2日 金曜日、先勝
+ OSPF LSA Manipulation Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130801-lsaospf
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0149
+ HPSBUX02909 SSRT101289 rev.1 - HP-UX Apache Web Server, Remote Denial of Service (DoS)
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03883001-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-2686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0166
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0169
+ SYM13-011 Security Advisories Relating to Symantec Products - Symantec Workspace Virtualization Local Kernel Elevation of Privilege
http://www.symantec.com/security_response/securityupdates/detail.jsp?fid=security_advisory&pvid=security_advisory&year=&suid=20130801_02
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4679
+ SYM13-010 Security Advisories Relating to Symantec Products - Symantec Endpoint Encryption Unquoted Search Path
http://www.symantec.com/security_response/securityupdates/detail.jsp?fid=security_advisory&pvid=security_advisory&year=&suid=20130801_01
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1610
+ SYM13-009 Security Advisories Relating to Symantec Products - Symantec Backup Exec Multiple Issues
http://www.symantec.com/security_response/securityupdates/detail.jsp?fid=security_advisory&pvid=security_advisory&year=&suid=20130801_00
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4575
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4676
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4677
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4678
+ Subversion 1.8.0 Assertion failed remote DoS
http://cxsecurity.com/issue/WLB-2013080005
+ Subversion 1.7.9 remote DoS vulnerability
http://cxsecurity.com/issue/WLB-2013080004
+ Subversion 1.7.9 newline denial of service
http://cxsecurity.com/issue/WLB-2013080002
+ Subversion 1.6.21 arbitrary code execution
http://cxsecurity.com/issue/WLB-2013080003
+ SA54345 VMware ESX Server Multiple Vulnerabilities
http://secunia.com/advisories/54345/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0166
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0169
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0268
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0338
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0871
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2116
+ SA54339 VMware ESXi Multiple Vulnerabilities
http://secunia.com/advisories/54339/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0166
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0169
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0338
+ SA54358 McAfee Firewall Enterprise BIND RDATA Handling Assertion Failure Denial of Service Vulnerability
http://secunia.com/advisories/54358/
+ Symantec Workspace Virtualization 'fslx.sys' Local Privilege Escalation Vulnerability
http://www.securityfocus.com/bid/61349
「自動車ハッキング論文」:英法廷が差し止め(WIRED.jp)
http://itpro.nikkeibp.co.jp/article/NEWS/20130802/496165/?ST=security
Windows向け偽アンチウイルスの新顔「System Doctor 2014」
http://itpro.nikkeibp.co.jp/article/COLUMN/20130725/494203/?ST=security
第5回 標的型攻撃や難読化…新型不正アプリの防衛策
http://itpro.nikkeibp.co.jp/article/COLUMN/20130725/494094/?ST=security
チェックしておきたい脆弱性情報<2013.8.1>
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495462/?ST=security
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130801-lsaospf
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0149
+ HPSBUX02909 SSRT101289 rev.1 - HP-UX Apache Web Server, Remote Denial of Service (DoS)
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03883001-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-2686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0166
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0169
+ SYM13-011 Security Advisories Relating to Symantec Products - Symantec Workspace Virtualization Local Kernel Elevation of Privilege
http://www.symantec.com/security_response/securityupdates/detail.jsp?fid=security_advisory&pvid=security_advisory&year=&suid=20130801_02
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4679
+ SYM13-010 Security Advisories Relating to Symantec Products - Symantec Endpoint Encryption Unquoted Search Path
http://www.symantec.com/security_response/securityupdates/detail.jsp?fid=security_advisory&pvid=security_advisory&year=&suid=20130801_01
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1610
+ SYM13-009 Security Advisories Relating to Symantec Products - Symantec Backup Exec Multiple Issues
http://www.symantec.com/security_response/securityupdates/detail.jsp?fid=security_advisory&pvid=security_advisory&year=&suid=20130801_00
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4575
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4676
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4677
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4678
+ Subversion 1.8.0 Assertion failed remote DoS
http://cxsecurity.com/issue/WLB-2013080005
+ Subversion 1.7.9 remote DoS vulnerability
http://cxsecurity.com/issue/WLB-2013080004
+ Subversion 1.7.9 newline denial of service
http://cxsecurity.com/issue/WLB-2013080002
+ Subversion 1.6.21 arbitrary code execution
http://cxsecurity.com/issue/WLB-2013080003
+ SA54345 VMware ESX Server Multiple Vulnerabilities
http://secunia.com/advisories/54345/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0166
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0169
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0268
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0338
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0871
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2116
+ SA54339 VMware ESXi Multiple Vulnerabilities
http://secunia.com/advisories/54339/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0166
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0169
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0338
+ SA54358 McAfee Firewall Enterprise BIND RDATA Handling Assertion Failure Denial of Service Vulnerability
http://secunia.com/advisories/54358/
+ Symantec Workspace Virtualization 'fslx.sys' Local Privilege Escalation Vulnerability
http://www.securityfocus.com/bid/61349
「自動車ハッキング論文」:英法廷が差し止め(WIRED.jp)
http://itpro.nikkeibp.co.jp/article/NEWS/20130802/496165/?ST=security
Windows向け偽アンチウイルスの新顔「System Doctor 2014」
http://itpro.nikkeibp.co.jp/article/COLUMN/20130725/494203/?ST=security
第5回 標的型攻撃や難読化…新型不正アプリの防衛策
http://itpro.nikkeibp.co.jp/article/COLUMN/20130725/494094/?ST=security
チェックしておきたい脆弱性情報<2013.8.1>
http://itpro.nikkeibp.co.jp/article/COLUMN/20130730/495462/?ST=security
2013年8月1日木曜日
1日 木曜日、赤口
+ CESA-2013:1119 Moderate CentOS 6 389-ds-base Update
http://lwn.net/Alerts/561598/
+ CESA-2013:1120 Moderate CentOS 6 haproxy Update
http://lwn.net/Alerts/561599/
+ CESA-2013:1121 Low CentOS 5 sos Update
http://lwn.net/Alerts/561600/
+ Cisco WAAS Central Manager Remote Code Execution Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130731-waascm
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3443
+ Authenticated Command Injection Vulnerability in Multiple Cisco Content Network and Video Delivery Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130731-cm
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3444
+ HPSBMU02902 rev.1 - HP Integrated Lights-Out iLO3, iLO4 IPMI Cipher Suite 0 Authentication Bypass Vulnerability
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03844348-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4805
+ UPDATE: HPSBPI02887 rev.2 - Certain HP LaserJet Pro Printers, Remote Information Disclosure
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03825817-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HPSBUX02907 rev.1 - HP-UX Running Java7, Remote Unauthorized Access, Disclosure of Information, and Other Vulnerabilities
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03868911-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HPSBUX02908 rev.1 - HP-UX Running Java6, Remote Unauthorized Access, Disclosure of Information, and Other Vulnerabilities
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03874547-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ IE9/10 information disclosure vulnerability
http://cxsecurity.com/issue/WLB-2013070232
+ phpMyAdmin 3.5.x/4.0.x self-XSS
http://cxsecurity.com/issue/WLB-2013070229
+ phpMyAdmin 3.5.x/4.0.x privilege escalation
http://cxsecurity.com/issue/WLB-2013070230
世界のセキュリティ・ラボから日経コミュニケーション
UI redressの新たな手法、キージャッキング
http://itpro.nikkeibp.co.jp/article/COLUMN/20130725/494202/?ST=security
第4回 国を超え行き交うアプリ、通じない日本の常識
http://itpro.nikkeibp.co.jp/article/COLUMN/20130725/494093/?ST=security
RSA、オンラインバンキングを狙ったトロイの木馬の新定番「KINS」を報告
http://itpro.nikkeibp.co.jp/article/NEWS/20130731/495740/?ST=security
三和コムテックがマルウエア119番サービス、ツールの短期ライセンスを新設し安価に提供
http://itpro.nikkeibp.co.jp/article/NEWS/20130731/495605/?ST=security
http://lwn.net/Alerts/561598/
+ CESA-2013:1120 Moderate CentOS 6 haproxy Update
http://lwn.net/Alerts/561599/
+ CESA-2013:1121 Low CentOS 5 sos Update
http://lwn.net/Alerts/561600/
+ Cisco WAAS Central Manager Remote Code Execution Vulnerability
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130731-waascm
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3443
+ Authenticated Command Injection Vulnerability in Multiple Cisco Content Network and Video Delivery Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130731-cm
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3444
+ HPSBMU02902 rev.1 - HP Integrated Lights-Out iLO3, iLO4 IPMI Cipher Suite 0 Authentication Bypass Vulnerability
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03844348-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4805
+ UPDATE: HPSBPI02887 rev.2 - Certain HP LaserJet Pro Printers, Remote Information Disclosure
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03825817-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HPSBUX02907 rev.1 - HP-UX Running Java7, Remote Unauthorized Access, Disclosure of Information, and Other Vulnerabilities
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03868911-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HPSBUX02908 rev.1 - HP-UX Running Java6, Remote Unauthorized Access, Disclosure of Information, and Other Vulnerabilities
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c03874547-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ IE9/10 information disclosure vulnerability
http://cxsecurity.com/issue/WLB-2013070232
+ phpMyAdmin 3.5.x/4.0.x self-XSS
http://cxsecurity.com/issue/WLB-2013070229
+ phpMyAdmin 3.5.x/4.0.x privilege escalation
http://cxsecurity.com/issue/WLB-2013070230
世界のセキュリティ・ラボから日経コミュニケーション
UI redressの新たな手法、キージャッキング
http://itpro.nikkeibp.co.jp/article/COLUMN/20130725/494202/?ST=security
第4回 国を超え行き交うアプリ、通じない日本の常識
http://itpro.nikkeibp.co.jp/article/COLUMN/20130725/494093/?ST=security
RSA、オンラインバンキングを狙ったトロイの木馬の新定番「KINS」を報告
http://itpro.nikkeibp.co.jp/article/NEWS/20130731/495740/?ST=security
三和コムテックがマルウエア119番サービス、ツールの短期ライセンスを新設し安価に提供
http://itpro.nikkeibp.co.jp/article/NEWS/20130731/495605/?ST=security
登録:
投稿 (Atom)