+ CESA-2016:0695 Critical CentOS 7 firefox Security Update
http://lwn.net/Alerts/685265/
+ VU#718152 NTP.org ntpd contains multiple vulnerabilities
https://www.kb.cert.org/vuls/id/718152
+ Linux kernel 3.18.32, 3.12.59, 3.4.112 released
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.18.32
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.12.59
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.4.112
+ SA70200 NTP Information Disclosure and Security Bypass Multiple Vulnerabilities
https://secunia.com/advisories/70200/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1547
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1548
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1550
+ SA70179 PHP Multiple Vulnerabilities
https://secunia.com/advisories/70179/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3074
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3078
+ SA70201 Hitachi Cosminexus / uCosminexus Products Java Multiple Vulnerabilities
https://secunia.com/advisories/70201/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0636
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0687
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0695
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3422
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3425
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3426
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3427
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3443
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3449
+ HS16-012 Multiple Vulnerabilities in Cosminexus
http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS16-012/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0636
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0687
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0695
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3422
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3425
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3426
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3427
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3443
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3449
+ HS16-012 Cosminexusにおける複数の脆弱性
http://www.hitachi.co.jp/Prod/comp/soft1/security/info/vuls/HS16-012/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0636
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0687
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0695
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3422
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3425
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3426
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3427
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3443
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3449
+ GCC 6.1 released
https://gcc.gnu.org/gcc-6/changes.html
+ NTP 4.2.8p7 released
http://archive.ntp.org/ntp4/ChangeLog-stable
+ JVNVU#91375252 Apache Struts2 に任意のコード実行の脆弱性
http://jvn.jp/vu/JVNVU91375252/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3081
+ JVNVU#99234709 glibc ライブラリにバッファオーバーフローの脆弱性
http://jvn.jp/vu/JVNVU99234709/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-0235
チェックしておきたい脆弱性情報<2016.04.28>
http://itpro.nikkeibp.co.jp/atcl/column/14/268561/042200111/?ST=security
Windows 7 ユーザーのためのWindows 10 入門講座
[9]Windows 10でセーフモードはどうやって起動するの?
[F8]キーを押してセーフモードに移行する方法も解説
http://itpro.nikkeibp.co.jp/atcl/column/16/021900040/041800010/?ST=security
Struts 2の脆弱性狙う攻撃が国内でも発生、至急回避策を
Struts 1には影響しない可能性
http://itpro.nikkeibp.co.jp/atcl/news/16/042701268/?ST=security
NETSEAが脆弱性情報に報奨金、実動作環境で調査を受ける
http://itpro.nikkeibp.co.jp/atcl/news/16/042701258/?ST=security
B2B卸の「NETSEA」、約13万件の個人情報を流出
http://itpro.nikkeibp.co.jp/atcl/news/16/042601241/?ST=security
キヤノンITS、マルウエア解析・報告書作成のスポットサービスを7月開始
http://itpro.nikkeibp.co.jp/atcl/news/16/042701256/?ST=security
UPDATE: JVNVU#92116866 ケータイキット for Movable Type に OS コマンドインジェクションの脆弱性
http://jvn.jp/vu/JVNVU92116866/index.html
JVNVU#90405898 ManageEngine Password Manager Pro にアクセス制限不備の脆弱性
http://jvn.jp/vu/JVNVU90405898/index.html
JVNVU#92232364 Microsoft Windows および Samba の認証機能に脆弱性 ("Badlock")
http://jvn.jp/vu/JVNVU92232364/index.html
2016年4月28日木曜日
2016年4月27日水曜日
27日 水曜日、大安
+ RHSA-2016:0695 Critical: firefox security update
https://rhn.redhat.com/errata/RHSA-2016-0695.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2805
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2806
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2807
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2808
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2814
+ Mozilla Firefox 46.0 released
https://www.mozilla.org/en-US/firefox/46.0/releasenotes/
+ MFSA 2016-48 Firefox Health Reports could accept events from untrusted domains
https://www.mozilla.org/en-US/security/advisories/mfsa2016-48/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2820
+ MFSA 2016-47 Write to invalid HashMap entry through JavaScript.watch()
https://www.mozilla.org/en-US/security/advisories/mfsa2016-47/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2808
+ MFSA 2016-46 Elevation of privilege with chrome.tabs.update API in web extensions
https://www.mozilla.org/en-US/security/advisories/mfsa2016-46/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2817
+ MFSA 2016-45 CSP not applied to pages sent with multipart/x-mixed-replace
https://www.mozilla.org/en-US/security/advisories/mfsa2016-45/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2816
+ MFSA 2016-44 Buffer overflow in libstagefright with CENC offsets
https://www.mozilla.org/en-US/security/advisories/mfsa2016-44/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2814
+ MFSA 2016-43 Disclosure of user actions through JavaScript with motion and orientation sensors
https://www.mozilla.org/en-US/security/advisories/mfsa2016-43/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2813
+ MFSA 2016-42 Use-after-free and buffer overflow in Service Workers
https://www.mozilla.org/en-US/security/advisories/mfsa2016-42/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2811
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2812
+ MFSA 2016-41 Content provider permission bypass allows malicious application to access data
https://www.mozilla.org/en-US/security/advisories/mfsa2016-41/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2810
+ MFSA 2016-40 Privilege escalation through file deletion by Maintenance Service updater
https://www.mozilla.org/en-US/security/advisories/mfsa2016-40/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2809
+ MFSA 2016-39 Miscellaneous memory safety hazards (rv:46.0 / rv:45.1 / rv:38.8)
https://www.mozilla.org/en-US/security/advisories/mfsa2016-39/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2807
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2806
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2804
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2805
+ nginx 1.10.0 released
http://nginx.org/
+ CESA-2016:0684 Moderate CentOS 5 nspr Security Update
http://lwn.net/Alerts/685111/
+ CESA-2016:0684 Moderate CentOS 5 nss Security Update
http://lwn.net/Alerts/685112/
+ CESA-2016:0685 Moderate CentOS 7 nss-util Security Update
http://lwn.net/Alerts/685116/
+ CESA-2016:0685 Moderate CentOS 7 nspr Security Update
http://lwn.net/Alerts/685113/
+ CESA-2016:0685 Moderate CentOS 7 nss Security Update
http://lwn.net/Alerts/685114/
+ CESA-2016:0685 Moderate CentOS 7 nss-softokn Security Update
http://lwn.net/Alerts/685115/
+ Dovecot 2.2.24 released
http://www.dovecot.org/list/dovecot-news/2016-April/000320.html
+ Wireshark Multiple Dissector Bugs Let Remote Users Deny Service
http://www.securitytracker.com/id/1035685
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4006
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4076
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4077
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4078
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4079
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4080
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4081
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4082
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4083
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4084
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4085
JVNDB-2016-000053 EC-CUBE におけるクロスサイトリクエストフォージェリの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000053.html
JVNDB-2016-000057 株式会社シロハチ製の複数の EC-CUBE 用フリーエリア追加プラグインにおけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000057.html
JVNDB-2016-000052 EC-CUBE におけるアクセス制限不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000052.html
JVNDB-2016-000051 EC-CUBE におけるアクセス制限不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000051.html
Windows 7 ユーザーのためのWindows 10 入門講座
[8]Windows 10でパスワードはリセットできないの?
ローカルアカウントとMicrosoftアカウントでは違うので注意!
http://itpro.nikkeibp.co.jp/atcl/column/16/021900040/041200008/?ST=security
ファイア・アイがセキュリティ運用サービスの日本語対応を強化、2月に日本拠点を設置
http://itpro.nikkeibp.co.jp/atcl/news/16/042601239/?ST=security
JVNVU#92116866 ケータイキット for Movable Type に OS コマンドインジェクションの脆弱性
http://jvn.jp/vu/JVNVU92116866/
JVNVU#97339542 SaAT Netizen にダウンロードファイル検証不備の脆弱性
http://jvn.jp/vu/JVNVU97339542/
JVNVU#95625579 Allround Automations PL/SQL Developer が HTTP 経由でアップデートする問題
http://jvn.jp/vu/JVNVU95625579/index.html
https://rhn.redhat.com/errata/RHSA-2016-0695.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2805
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2806
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2807
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2808
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2814
+ Mozilla Firefox 46.0 released
https://www.mozilla.org/en-US/firefox/46.0/releasenotes/
+ MFSA 2016-48 Firefox Health Reports could accept events from untrusted domains
https://www.mozilla.org/en-US/security/advisories/mfsa2016-48/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2820
+ MFSA 2016-47 Write to invalid HashMap entry through JavaScript.watch()
https://www.mozilla.org/en-US/security/advisories/mfsa2016-47/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2808
+ MFSA 2016-46 Elevation of privilege with chrome.tabs.update API in web extensions
https://www.mozilla.org/en-US/security/advisories/mfsa2016-46/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2817
+ MFSA 2016-45 CSP not applied to pages sent with multipart/x-mixed-replace
https://www.mozilla.org/en-US/security/advisories/mfsa2016-45/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2816
+ MFSA 2016-44 Buffer overflow in libstagefright with CENC offsets
https://www.mozilla.org/en-US/security/advisories/mfsa2016-44/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2814
+ MFSA 2016-43 Disclosure of user actions through JavaScript with motion and orientation sensors
https://www.mozilla.org/en-US/security/advisories/mfsa2016-43/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2813
+ MFSA 2016-42 Use-after-free and buffer overflow in Service Workers
https://www.mozilla.org/en-US/security/advisories/mfsa2016-42/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2811
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2812
+ MFSA 2016-41 Content provider permission bypass allows malicious application to access data
https://www.mozilla.org/en-US/security/advisories/mfsa2016-41/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2810
+ MFSA 2016-40 Privilege escalation through file deletion by Maintenance Service updater
https://www.mozilla.org/en-US/security/advisories/mfsa2016-40/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2809
+ MFSA 2016-39 Miscellaneous memory safety hazards (rv:46.0 / rv:45.1 / rv:38.8)
https://www.mozilla.org/en-US/security/advisories/mfsa2016-39/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2807
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2806
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2804
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2805
+ nginx 1.10.0 released
http://nginx.org/
+ CESA-2016:0684 Moderate CentOS 5 nspr Security Update
http://lwn.net/Alerts/685111/
+ CESA-2016:0684 Moderate CentOS 5 nss Security Update
http://lwn.net/Alerts/685112/
+ CESA-2016:0685 Moderate CentOS 7 nss-util Security Update
http://lwn.net/Alerts/685116/
+ CESA-2016:0685 Moderate CentOS 7 nspr Security Update
http://lwn.net/Alerts/685113/
+ CESA-2016:0685 Moderate CentOS 7 nss Security Update
http://lwn.net/Alerts/685114/
+ CESA-2016:0685 Moderate CentOS 7 nss-softokn Security Update
http://lwn.net/Alerts/685115/
+ Dovecot 2.2.24 released
http://www.dovecot.org/list/dovecot-news/2016-April/000320.html
+ Wireshark Multiple Dissector Bugs Let Remote Users Deny Service
http://www.securitytracker.com/id/1035685
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4006
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4076
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4077
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4078
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4079
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4080
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4081
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4082
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4083
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4084
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4085
JVNDB-2016-000053 EC-CUBE におけるクロスサイトリクエストフォージェリの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000053.html
JVNDB-2016-000057 株式会社シロハチ製の複数の EC-CUBE 用フリーエリア追加プラグインにおけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000057.html
JVNDB-2016-000052 EC-CUBE におけるアクセス制限不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000052.html
JVNDB-2016-000051 EC-CUBE におけるアクセス制限不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000051.html
Windows 7 ユーザーのためのWindows 10 入門講座
[8]Windows 10でパスワードはリセットできないの?
ローカルアカウントとMicrosoftアカウントでは違うので注意!
http://itpro.nikkeibp.co.jp/atcl/column/16/021900040/041200008/?ST=security
ファイア・アイがセキュリティ運用サービスの日本語対応を強化、2月に日本拠点を設置
http://itpro.nikkeibp.co.jp/atcl/news/16/042601239/?ST=security
JVNVU#92116866 ケータイキット for Movable Type に OS コマンドインジェクションの脆弱性
http://jvn.jp/vu/JVNVU92116866/
JVNVU#97339542 SaAT Netizen にダウンロードファイル検証不備の脆弱性
http://jvn.jp/vu/JVNVU97339542/
JVNVU#95625579 Allround Automations PL/SQL Developer が HTTP 経由でアップデートする問題
http://jvn.jp/vu/JVNVU95625579/index.html
2016年4月26日火曜日
26日 火曜日、仏滅
+ UPDATE: マイクロソフト セキュリティ アドバイザリ 3152550 ワイヤレス マウス入力のフィルタリングを改善する更新プログラム
https://technet.microsoft.com/ja-jp/library/security/3152550
+ RHSA-2016:0684 Moderate: nss and nspr security, bug fix, and enhancement update
https://rhn.redhat.com/errata/RHSA-2016-0684.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1978
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1979
+ RHSA-2016:0685 Moderate: nss, nspr, nss-softokn, and nss-util security, bug fix, and enhancement update
https://rhn.redhat.com/errata/RHSA-2016-0685.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1978
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1979
+ SA70198 Apache Struts Two Code Execution Vulnerabilities
https://secunia.com/advisories/70198/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3081
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3082
+ SA70197 Apache Struts Multiple Code Execution Vulnerabilities
https://secunia.com/advisories/70197/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0785
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3081
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3082
+ SA70185 Docker Username Handling Security Bypass Vulnerability
https://secunia.com/advisories/70185/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3697
+ SA70190 Wireshark Multiple Denial of Service Vulnerabilities
https://secunia.com/advisories/70190/
+ NetBSD bozohttpd CGI Handling Flaw Lets Remote Users Execute Arbitrary Code on the Target System in Certain Cases
http://www.securitytracker.com/id/1035673
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8212
+ NetBSD Compatibility Layer Bugs Let Local Users Deny Service and Gain Elevated Privileges
http://www.securitytracker.com/id/1035672
VU#229047 Allround Automations PL/SQL Developer v11 performs updates over HTTP
https://www.kb.cert.org/vuls/id/229047
JVNDB-2016-000056 Android アプリ「kintone mobile for Android」における SSL サーバ証明書の検証不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000056.html
JVNDB-2016-000055 Android アプリ「kintone mobile for Android」における情報管理不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000055.html
JVNVU#98139587 SysLINK M2M Modular Gateway に複数の脆弱性
http://jvn.jp/vu/JVNVU98139587/index.html
JVNVU#97620397 HP Data Protector に複数の脆弱性
http://jvn.jp/vu/JVNVU97620397/index.html
UPDATE: JVN#11815655 スマートフォンアプリ「Photopt」における SSL サーバ証明書の検証不備の脆弱性
http://jvn.jp/jp/JVN11815655/index.html
Windows 7 ユーザーのためのWindows 10 入門講座
[7]なぜWindows 10ではパスワードではなくPINが推奨されるの?
2段階認証を導入してより安全に
http://itpro.nikkeibp.co.jp/atcl/column/16/021900040/040400007/?ST=security
チェックしておきたい脆弱性情報<2016.04.26>
http://itpro.nikkeibp.co.jp/atcl/column/14/268561/042200110/?ST=security
https://technet.microsoft.com/ja-jp/library/security/3152550
+ RHSA-2016:0684 Moderate: nss and nspr security, bug fix, and enhancement update
https://rhn.redhat.com/errata/RHSA-2016-0684.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1978
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1979
+ RHSA-2016:0685 Moderate: nss, nspr, nss-softokn, and nss-util security, bug fix, and enhancement update
https://rhn.redhat.com/errata/RHSA-2016-0685.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1978
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1979
+ SA70198 Apache Struts Two Code Execution Vulnerabilities
https://secunia.com/advisories/70198/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3081
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3082
+ SA70197 Apache Struts Multiple Code Execution Vulnerabilities
https://secunia.com/advisories/70197/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0785
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3081
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3082
+ SA70185 Docker Username Handling Security Bypass Vulnerability
https://secunia.com/advisories/70185/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3697
+ SA70190 Wireshark Multiple Denial of Service Vulnerabilities
https://secunia.com/advisories/70190/
+ NetBSD bozohttpd CGI Handling Flaw Lets Remote Users Execute Arbitrary Code on the Target System in Certain Cases
http://www.securitytracker.com/id/1035673
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8212
+ NetBSD Compatibility Layer Bugs Let Local Users Deny Service and Gain Elevated Privileges
http://www.securitytracker.com/id/1035672
VU#229047 Allround Automations PL/SQL Developer v11 performs updates over HTTP
https://www.kb.cert.org/vuls/id/229047
JVNDB-2016-000056 Android アプリ「kintone mobile for Android」における SSL サーバ証明書の検証不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000056.html
JVNDB-2016-000055 Android アプリ「kintone mobile for Android」における情報管理不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000055.html
JVNVU#98139587 SysLINK M2M Modular Gateway に複数の脆弱性
http://jvn.jp/vu/JVNVU98139587/index.html
JVNVU#97620397 HP Data Protector に複数の脆弱性
http://jvn.jp/vu/JVNVU97620397/index.html
UPDATE: JVN#11815655 スマートフォンアプリ「Photopt」における SSL サーバ証明書の検証不備の脆弱性
http://jvn.jp/jp/JVN11815655/index.html
Windows 7 ユーザーのためのWindows 10 入門講座
[7]なぜWindows 10ではパスワードではなくPINが推奨されるの?
2段階認証を導入してより安全に
http://itpro.nikkeibp.co.jp/atcl/column/16/021900040/040400007/?ST=security
チェックしておきたい脆弱性情報<2016.04.26>
http://itpro.nikkeibp.co.jp/atcl/column/14/268561/042200110/?ST=security
2016年4月25日月曜日
25日 月曜日、先負
+ CESA-2016:0676 Critical CentOS 5 java-1.7.0-openjdk Security Update
http://lwn.net/Alerts/684720/
+ CESA-2016:0650 Critical CentOS 7 java-1.8.0-openjdk Security Update
http://lwn.net/Alerts/684723/
+ CESA-2016:0676 Critical CentOS 7 java-1.7.0-openjdk Security Update
http://lwn.net/Alerts/684721/
+ CESA-2016:0675 Critical CentOS 6 java-1.7.0-openjdk Security Update
http://lwn.net/Alerts/684719/
+ CESA-2016:0651 Critical CentOS 6 java-1.8.0-openjdk Security Update
http://lwn.net/Alerts/684722/
+ VMware Workstation Player 12.1.1 released
http://pubs.vmware.com/Release_Notes/en/workstation/12player/player-1211-release-notes.html
+ Wireshark 2.0.3, 1.12.11 released
https://www.wireshark.org/docs/relnotes/wireshark-2.0.3.html
https://www.wireshark.org/docs/relnotes/wireshark-1.12.11.html
+ VU#267328 HP Data Protector does not perform authentication and contains an embedded SSL private key
https://www.kb.cert.org/vuls/id/267328
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2004
+ Adobe Analytics AppMeasurement for Flash Library Input Validation Flaw Lets Remote Conduct Cross-Site Scripting Attacks
http://www.securitytracker.com/id/1035671
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1036
+ Apache Struts Dynamic Method Invocation Bug Lets Remote Users Execute Arbitrary Code on the Target System
http://www.securitytracker.com/id/1035665
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3081
+ Apache Struts XSLTResult Stylesheet Location Validation Flaw Lets Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1035664
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3082
+ HP Data Protector 6.10 / 6.11 / 6.20 Install Service
https://cxsecurity.com/issue/WLB-2016040149
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0922
VU#822980 SysLINK M2M Modular Gateway contains multiple vulnerabilities
https://www.kb.cert.org/vuls/id/822980
JVNDB-2016-000054 Electron における Node モジュール読み込みに関する問題
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000054.html
Windows 7 ユーザーのためのWindows 10 入門講座
[6]どうしてWindows 10にロック画面があるの?
ロック画面を非表示にする手順とカスタマイズして便利に使う方法を紹介
http://itpro.nikkeibp.co.jp/atcl/column/16/021900040/030600006/?ST=security
J-WAVEでも64万件の個人情報流出の可能性、原因ソフトの利用者は至急パッチ適用を
http://itpro.nikkeibp.co.jp/atcl/news/16/042301210/?ST=security
NEC、ファイルをアップロードしてマルウエア判定するクラウドサービスを販売
http://itpro.nikkeibp.co.jp/atcl/news/16/042201205/?ST=security
グーグルがChrome拡張機能のデータポリシー変更、他のWeb解析サービスに打撃か
http://itpro.nikkeibp.co.jp/atcl/column/14/346926/042200513/?ST=security
http://lwn.net/Alerts/684720/
+ CESA-2016:0650 Critical CentOS 7 java-1.8.0-openjdk Security Update
http://lwn.net/Alerts/684723/
+ CESA-2016:0676 Critical CentOS 7 java-1.7.0-openjdk Security Update
http://lwn.net/Alerts/684721/
+ CESA-2016:0675 Critical CentOS 6 java-1.7.0-openjdk Security Update
http://lwn.net/Alerts/684719/
+ CESA-2016:0651 Critical CentOS 6 java-1.8.0-openjdk Security Update
http://lwn.net/Alerts/684722/
+ VMware Workstation Player 12.1.1 released
http://pubs.vmware.com/Release_Notes/en/workstation/12player/player-1211-release-notes.html
+ Wireshark 2.0.3, 1.12.11 released
https://www.wireshark.org/docs/relnotes/wireshark-2.0.3.html
https://www.wireshark.org/docs/relnotes/wireshark-1.12.11.html
+ VU#267328 HP Data Protector does not perform authentication and contains an embedded SSL private key
https://www.kb.cert.org/vuls/id/267328
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2004
+ Adobe Analytics AppMeasurement for Flash Library Input Validation Flaw Lets Remote Conduct Cross-Site Scripting Attacks
http://www.securitytracker.com/id/1035671
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1036
+ Apache Struts Dynamic Method Invocation Bug Lets Remote Users Execute Arbitrary Code on the Target System
http://www.securitytracker.com/id/1035665
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3081
+ Apache Struts XSLTResult Stylesheet Location Validation Flaw Lets Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1035664
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3082
+ HP Data Protector 6.10 / 6.11 / 6.20 Install Service
https://cxsecurity.com/issue/WLB-2016040149
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-0922
VU#822980 SysLINK M2M Modular Gateway contains multiple vulnerabilities
https://www.kb.cert.org/vuls/id/822980
JVNDB-2016-000054 Electron における Node モジュール読み込みに関する問題
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000054.html
Windows 7 ユーザーのためのWindows 10 入門講座
[6]どうしてWindows 10にロック画面があるの?
ロック画面を非表示にする手順とカスタマイズして便利に使う方法を紹介
http://itpro.nikkeibp.co.jp/atcl/column/16/021900040/030600006/?ST=security
J-WAVEでも64万件の個人情報流出の可能性、原因ソフトの利用者は至急パッチ適用を
http://itpro.nikkeibp.co.jp/atcl/news/16/042301210/?ST=security
NEC、ファイルをアップロードしてマルウエア判定するクラウドサービスを販売
http://itpro.nikkeibp.co.jp/atcl/news/16/042201205/?ST=security
グーグルがChrome拡張機能のデータポリシー変更、他のWeb解析サービスに打撃か
http://itpro.nikkeibp.co.jp/atcl/column/14/346926/042200513/?ST=security
2016年4月22日金曜日
情報セキュリティマネジメント試験
情報処理技術者試験の平成28年度春期から「情報セキュリティマネジメント試験」が新設されたので、受験してみた。
4/17 受験日
午前問題
https://www.jitec.ipa.go.jp/1_04hanni_sukiru/mondai_kaitou_2016h28_1/2016h28h_sg_am_qs.pdf
午後問題
https://www.jitec.ipa.go.jp/1_04hanni_sukiru/mondai_kaitou_2016h28_1/2016h28h_sg_pm_qs.pdf
早速、解答が発表されたので、自己採点してみた。
午前 正解84%
午後 正解81%
合格基準点が午前、午後それぞれ60点、ということでいい感じである。
5/16 正午の合格発表が楽しみだ…
これで肩書きから「新米」が取れるかもしれない (^^;;
4/17 受験日
午前問題
https://www.jitec.ipa.go.jp/1_04hanni_sukiru/mondai_kaitou_2016h28_1/2016h28h_sg_am_qs.pdf
午後問題
https://www.jitec.ipa.go.jp/1_04hanni_sukiru/mondai_kaitou_2016h28_1/2016h28h_sg_pm_qs.pdf
早速、解答が発表されたので、自己採点してみた。
午前 正解84%
午後 正解81%
合格基準点が午前、午後それぞれ60点、ということでいい感じである。
5/16 正午の合格発表が楽しみだ…
これで肩書きから「新米」が取れるかもしれない (^^;;
ubuntu 16.04 LTS Install MEMO
ubuntu 16.04 がリリースされたので、インストールしてみた。
1. DVD から起動
2. 「Welcome」画面が表示される。
3. 言語で「日本語」を選択すると、日本語表示に変わる。[Ubuntu をインストール] ボタンを押す。
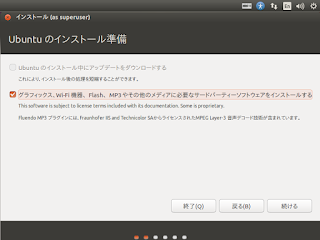
4. 「Ubuntu のインストール準備」画面が表示さえるので、「グラフィックス、…」を選択して、[続ける] ボタンを押す。
5. 「インストールの種類」画面が表示されるので、「ディスクを削除して…」を選択して、[インストール] ボタンを押す。
6. 「ディスクに変更を書き込みますか?」ダイアログが表示されるので、[続ける] ボタンを押す。
7. 「どこに住んでいますか?」画面が表示されるので、「Tokyo」と指定して、[続ける] ボタンを押す。
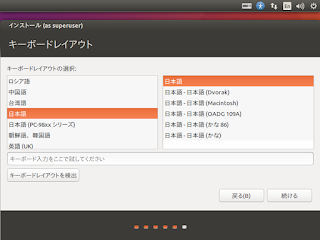
8. 「キーボードレイアウト」画面が表示されるので、「日本語」、「日本語」が選択されていることを確認して、[続ける] ボタンを押す。
9. 「あなたの情報を入力してください」画面が表示されるので、「あなたの名前、「コンピュータの名前」、「ユーザー名の入力」、「パスワードの入力」、「パスワードの確認」欄に入力して、「ログイン時にパスワードを要求する」を選択して、[続ける] ボタンを押す。
10. インストールが開始される。
11. インストール中
12. インストール中
13. インストール中
14. インストール中
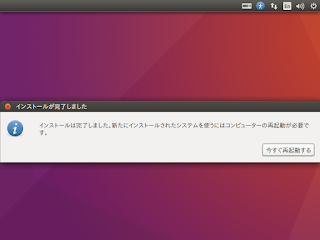
15. 「インストールが完了しました」ダイアログが表示されるので、[今すぐ再起動する] ボタンを押す。
16. 再起動が完了すると、ログイン画面が表示される。
17. ログインして、アプリケーション等を起動してみる。
1. DVD から起動
2. 「Welcome」画面が表示される。
3. 言語で「日本語」を選択すると、日本語表示に変わる。[Ubuntu をインストール] ボタンを押す。
4. 「Ubuntu のインストール準備」画面が表示さえるので、「グラフィックス、…」を選択して、[続ける] ボタンを押す。
5. 「インストールの種類」画面が表示されるので、「ディスクを削除して…」を選択して、[インストール] ボタンを押す。
6. 「ディスクに変更を書き込みますか?」ダイアログが表示されるので、[続ける] ボタンを押す。
7. 「どこに住んでいますか?」画面が表示されるので、「Tokyo」と指定して、[続ける] ボタンを押す。
8. 「キーボードレイアウト」画面が表示されるので、「日本語」、「日本語」が選択されていることを確認して、[続ける] ボタンを押す。
9. 「あなたの情報を入力してください」画面が表示されるので、「あなたの名前、「コンピュータの名前」、「ユーザー名の入力」、「パスワードの入力」、「パスワードの確認」欄に入力して、「ログイン時にパスワードを要求する」を選択して、[続ける] ボタンを押す。
10. インストールが開始される。
11. インストール中
12. インストール中
13. インストール中
14. インストール中
15. 「インストールが完了しました」ダイアログが表示されるので、[今すぐ再起動する] ボタンを押す。
16. 再起動が完了すると、ログイン画面が表示される。
17. ログインして、アプリケーション等を起動してみる。
22日 金曜日、赤口
+ UPDATE: MS16-039 - 緊急 Microsoft Graphics コンポーネントのセキュリティ更新プログラム (3148522)
https://technet.microsoft.com/ja-jp/library/security/MS16-039
+ RHSA-2016:0676 Critical: java-1.7.0-openjdk security update
https://rhn.redhat.com/errata/RHSA-2016-0676.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0687
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0695
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3425
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3427
+ RHSA-2016:0675 Critical: java-1.7.0-openjdk security update
https://rhn.redhat.com/errata/RHSA-2016-0675.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0687
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0695
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3425
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3427
+ RHSA-2016:0651 Critical: java-1.8.0-openjdk security update
https://rhn.redhat.com/errata/RHSA-2016-0651.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0687
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0695
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3425
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3426
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3427
+ RHSA-2016:0650 Critical: java-1.8.0-openjdk security update
https://rhn.redhat.com/errata/RHSA-2016-0650.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0687
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0695
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3425
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3426
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3427
+ Google Chrome 50.0.2661.87 released
http://googlechromereleases.blogspot.jp/2016/04/stable-channel-update_20.html
+ APSB16-13 Security update available for the Adobe Analytics AppMeasurement for Flash Library
https://helpx.adobe.com/security/products/analytics/APSB16-13.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1036
+ squid 3.5.17 released
http://www.squid-cache.org/Versions/v3/3.5/squid-3.5.17-RELEASENOTES.html
+ Ubuntu 16.04 LTS released
https://wiki.ubuntu.com/XenialXerus/ReleaseNotes?_ga=1.106222147.1754260706.1408405881
+ Multiple Cisco Products libSRTP Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160420-libsrtp
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-6360
+ Cisco Wireless LAN Controller Management Interface Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160420-wlc
+ Cisco Wireless LAN Controller Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160420-bdos
+ Cisco Adaptive Security Appliance Software DHCPv6 Relay Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160420-asa-dhcpv6
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1367
+ Cisco Wireless LAN Controller HTTP Parsing Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160420-htrd
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1363
+ UPDATE: Cisco IOS XR for Cisco ASR 9000 Series Aggregation Services Routers Interface Flap Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160412-asr
+ Linux kernel 4.5.2, 4.4.8, 4.1.22, 3.18.31, 3.14.67 released
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.5.2
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.4.8
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.1.22
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.18.31
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.14.67
+ SA70105 Squid Multiple Vulnerabilities
https://secunia.com/advisories/70105/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4051
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4052
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4053
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4054
+ SA70053 Linux Kernel "usbip_recv_xbuff()" Memory Corruption Vulnerability
https://secunia.com/advisories/70053/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3955
+ S2-032 Remote Code Execution can be performed via method: prefix when Dynamic Method Invocation is enabled.
http://struts.apache.org/docs/s2-032.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3081
+ S2-031 XSLTResult can be used to parse arbitrary stylesheet
http://struts.apache.org/docs/s2-031.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3082
+ Apache Struts 2.3.28.1, 2.3.20.3, 2.3.24.3 GA released
http://struts.apache.org/announce.html#a20160419
+ Wireshark <= 1.12.9 DLL hijacking exploit (riched20.dll.dll)
https://cxsecurity.com/issue/WLB-2016040132
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2521
図解で手口を学ぶ「脆弱性」セキュリティ
図解でわかるキャッシュポイズニング
http://itpro.nikkeibp.co.jp/atcl/column/16/041400084/041400005/?ST=security
サイバークライムアナリストが明かす標的型攻撃の実像
手法再現で理解する、標的型攻撃を受けた端末は一体何をされるのか(3)
http://itpro.nikkeibp.co.jp/atcl/column/16/041300083/041500004/?ST=security
日テレWebサイトに不正アクセス、約43万件の個人情報流出の恐れ
http://itpro.nikkeibp.co.jp/atcl/news/16/042101194/?ST=security
図解で手口を学ぶ「脆弱性」セキュリティ
図解でわかるSQLインジェクション
http://itpro.nikkeibp.co.jp/atcl/column/16/041400084/041400004/?ST=security
サイバークライムアナリストが明かす標的型攻撃の実像
手法再現で理解する、標的型攻撃を受けた端末は一体何をされるのか(2)
http://itpro.nikkeibp.co.jp/atcl/column/16/041300083/041500003/?ST=security
ほけんの窓口が米Taniumのセキュリティツール採用、PC約5500台を一元管理
http://itpro.nikkeibp.co.jp/atcl/news/16/042001178/?ST=security
UPDATE: JVNVU#92749596 BlueDriver LSB2 に認証なしで Bluetooth アクセスが可能な問題
http://jvn.jp/vu/JVNVU92749596/
UPDATE: JVNVU#95244076 DameWare Mini Remote Control にスタックバッファオーバーフローの脆弱性
http://jvn.jp/vu/JVNVU95244076/
https://technet.microsoft.com/ja-jp/library/security/MS16-039
+ RHSA-2016:0676 Critical: java-1.7.0-openjdk security update
https://rhn.redhat.com/errata/RHSA-2016-0676.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0687
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0695
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3425
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3427
+ RHSA-2016:0675 Critical: java-1.7.0-openjdk security update
https://rhn.redhat.com/errata/RHSA-2016-0675.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0687
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0695
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3425
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3427
+ RHSA-2016:0651 Critical: java-1.8.0-openjdk security update
https://rhn.redhat.com/errata/RHSA-2016-0651.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0687
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0695
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3425
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3426
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3427
+ RHSA-2016:0650 Critical: java-1.8.0-openjdk security update
https://rhn.redhat.com/errata/RHSA-2016-0650.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0687
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0695
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3425
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3426
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3427
+ Google Chrome 50.0.2661.87 released
http://googlechromereleases.blogspot.jp/2016/04/stable-channel-update_20.html
+ APSB16-13 Security update available for the Adobe Analytics AppMeasurement for Flash Library
https://helpx.adobe.com/security/products/analytics/APSB16-13.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1036
+ squid 3.5.17 released
http://www.squid-cache.org/Versions/v3/3.5/squid-3.5.17-RELEASENOTES.html
+ Ubuntu 16.04 LTS released
https://wiki.ubuntu.com/XenialXerus/ReleaseNotes?_ga=1.106222147.1754260706.1408405881
+ Multiple Cisco Products libSRTP Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160420-libsrtp
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-6360
+ Cisco Wireless LAN Controller Management Interface Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160420-wlc
+ Cisco Wireless LAN Controller Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160420-bdos
+ Cisco Adaptive Security Appliance Software DHCPv6 Relay Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160420-asa-dhcpv6
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1367
+ Cisco Wireless LAN Controller HTTP Parsing Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160420-htrd
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1363
+ UPDATE: Cisco IOS XR for Cisco ASR 9000 Series Aggregation Services Routers Interface Flap Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160412-asr
+ Linux kernel 4.5.2, 4.4.8, 4.1.22, 3.18.31, 3.14.67 released
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.5.2
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.4.8
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.1.22
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.18.31
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.14.67
+ SA70105 Squid Multiple Vulnerabilities
https://secunia.com/advisories/70105/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4051
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4052
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4053
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4054
+ SA70053 Linux Kernel "usbip_recv_xbuff()" Memory Corruption Vulnerability
https://secunia.com/advisories/70053/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3955
+ S2-032 Remote Code Execution can be performed via method: prefix when Dynamic Method Invocation is enabled.
http://struts.apache.org/docs/s2-032.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3081
+ S2-031 XSLTResult can be used to parse arbitrary stylesheet
http://struts.apache.org/docs/s2-031.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3082
+ Apache Struts 2.3.28.1, 2.3.20.3, 2.3.24.3 GA released
http://struts.apache.org/announce.html#a20160419
+ Wireshark <= 1.12.9 DLL hijacking exploit (riched20.dll.dll)
https://cxsecurity.com/issue/WLB-2016040132
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2521
図解で手口を学ぶ「脆弱性」セキュリティ
図解でわかるキャッシュポイズニング
http://itpro.nikkeibp.co.jp/atcl/column/16/041400084/041400005/?ST=security
サイバークライムアナリストが明かす標的型攻撃の実像
手法再現で理解する、標的型攻撃を受けた端末は一体何をされるのか(3)
http://itpro.nikkeibp.co.jp/atcl/column/16/041300083/041500004/?ST=security
日テレWebサイトに不正アクセス、約43万件の個人情報流出の恐れ
http://itpro.nikkeibp.co.jp/atcl/news/16/042101194/?ST=security
図解で手口を学ぶ「脆弱性」セキュリティ
図解でわかるSQLインジェクション
http://itpro.nikkeibp.co.jp/atcl/column/16/041400084/041400004/?ST=security
サイバークライムアナリストが明かす標的型攻撃の実像
手法再現で理解する、標的型攻撃を受けた端末は一体何をされるのか(2)
http://itpro.nikkeibp.co.jp/atcl/column/16/041300083/041500003/?ST=security
ほけんの窓口が米Taniumのセキュリティツール採用、PC約5500台を一元管理
http://itpro.nikkeibp.co.jp/atcl/news/16/042001178/?ST=security
UPDATE: JVNVU#92749596 BlueDriver LSB2 に認証なしで Bluetooth アクセスが可能な問題
http://jvn.jp/vu/JVNVU92749596/
UPDATE: JVNVU#95244076 DameWare Mini Remote Control にスタックバッファオーバーフローの脆弱性
http://jvn.jp/vu/JVNVU95244076/
2016年4月20日水曜日
20日 水曜日、仏滅
+ RHSA-2016:0561 Low: Red Hat Enterprise Linux 5 One-Year Retirement Notice
https://rhn.redhat.com/errata/RHSA-2016-0561.html
+ Cisco IOS and Cisco IOS XE ntp Subsystem Unauthorized Access Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160419-ios
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1384
+ Oracle Critical Patch Update Advisory - April 2016
http://www.oracle.com/technetwork/security-advisory/cpuapr2016v3-2985753.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3454
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0681
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0677
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0690
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0691
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3253
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0638
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3455
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7547
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3576
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0479
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0675
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0700
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3416
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3197
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3197
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0468
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0696
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3195
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3195
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0671
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0688
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7501
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3197
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3466
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3439
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3437
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3436
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3447
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0697
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3434
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3456
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3438
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3420
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3431
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3195
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3428
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0679
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3421
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0407
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3197
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3460
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0408
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0685
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3417
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3442
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0698
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3423
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0683
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0680
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3435
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3457
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-1793
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0673
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0674
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2532
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0684
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0469
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3429
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3195
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0699
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0672
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3463
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3464
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3443
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0687
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3427
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3449
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0695
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3425
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3422
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3426
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0693
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7547
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3441
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4786
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-1789
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7236
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-1793
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3238
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0669
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2566
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3462
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3465
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-4461
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0623
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0676
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4000
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3419
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3195
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3195
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0678
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3197
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0705
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0639
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3194
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3461
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0640
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2047
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0644
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0646
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0652
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0647
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0653
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0654
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0656
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0657
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0658
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0651
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0659
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0648
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0649
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0662
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0650
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0665
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0666
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0641
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0642
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0655
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0661
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0663
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0667
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0668
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0643
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0682
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0689
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0692
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0694
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3418
+ Oracle Solaris Third Party Bulletin - April 2016
http://www.oracle.com/technetwork/topics/security/bulletinapr2016-2952098.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0705
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0799
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0798
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3415
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5602
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4752
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2523
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1283
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-9766
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3885
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6720
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0702
+ Oracle Linux Bulletin - April 2016
http://www.oracle.com/technetwork/topics/security/linuxbulletinapr2016-2952096.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-5325
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2315
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2324
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1521
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1522
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1523
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0636
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0636
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1526
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2114
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7810
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0774
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0774
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8327
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8560
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0546
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1978
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1979
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2047
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1908
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4879
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5600
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2113
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8631
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4792
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4802
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4815
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4816
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4826
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4830
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4836
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4858
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4861
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4870
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4913
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0505
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0596
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0597
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0616
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0598
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0600
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0606
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0608
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8629
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8630
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0609
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4819
+ SA70087 Symantec Messaging Gateway AD Password Disclosure Vulnerability
https://secunia.com/advisories/70087/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2203
+ SA70079 Xen x86 Shadow Pagetables Superpage Mapping Vulnerability
https://secunia.com/advisories/70079/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3960
+ Java Platform, Standard Edition 8 Update 91 (Java SE 8u91) and 8 Update 92 (Java SE 8u92) are Now Available
http://www.oracle.com/technetwork/java/javase/8u92-relnotes-2949471.html
http://www.oracle.com/technetwork/java/javase/8u91-relnotes-2949462.html
+ Beta 2 (pre-release 5) of OpenSSL 1.1.0 is now available: please download and test it
https://www.openssl.org/
Postgres-XL 9.5 R1 Released!
http://www.postgresql.org/about/news/1662/
JVNDB-2016-000050 スマートフォンアプリ「Photopt」における SSL サーバ証明書の検証不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000050.html
図解で手口を学ぶ「脆弱性」セキュリティ
図解でわかるHeartBleed
http://itpro.nikkeibp.co.jp/atcl/column/16/041400084/041400003/?ST=security
サイバークライムアナリストが明かす標的型攻撃の実像
手法再現で理解する、標的型攻撃を受けた端末は一体何をされるのか(1)
http://itpro.nikkeibp.co.jp/atcl/column/16/041300083/041500002/?ST=security
アイキューブドシステムズ、MDMのオプションで電子証明書を販売
http://itpro.nikkeibp.co.jp/atcl/news/16/041901147/?ST=security
ウェブルートが脅威レポートを発表、「もはや自動検出では対応できない」
http://itpro.nikkeibp.co.jp/atcl/news/16/041901144/?ST=security
https://rhn.redhat.com/errata/RHSA-2016-0561.html
+ Cisco IOS and Cisco IOS XE ntp Subsystem Unauthorized Access Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160419-ios
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1384
+ Oracle Critical Patch Update Advisory - April 2016
http://www.oracle.com/technetwork/security-advisory/cpuapr2016v3-2985753.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3454
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0681
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0677
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0690
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0691
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3253
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0638
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3455
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7547
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3576
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0479
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0675
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0700
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3416
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3197
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3197
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0468
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0696
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3195
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3195
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0671
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0688
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7501
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3197
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3466
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3439
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3437
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3436
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3447
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0697
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3434
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3456
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3438
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3420
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3431
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3195
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3428
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0679
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3421
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0407
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3197
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3460
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0408
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0685
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3417
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3442
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0698
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3423
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0683
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0680
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3435
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3457
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-1793
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0673
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0674
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2532
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0684
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0469
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3429
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3195
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0699
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0672
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3463
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3464
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3443
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0687
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0686
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3427
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3449
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0695
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3425
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3422
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3426
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0693
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7547
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3441
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4786
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-1789
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7236
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-1793
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3238
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0669
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2566
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3462
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3465
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-4461
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0623
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0676
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4000
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3419
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3195
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3195
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0678
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3197
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0705
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0639
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3194
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3461
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0640
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2047
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0644
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0646
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0652
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0647
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0653
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0654
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0656
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0657
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0658
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0651
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0659
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0648
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0649
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0662
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0650
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0665
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0666
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0641
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0642
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0655
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0661
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0663
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0667
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0668
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0643
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0682
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0689
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0692
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0694
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3418
+ Oracle Solaris Third Party Bulletin - April 2016
http://www.oracle.com/technetwork/topics/security/bulletinapr2016-2952098.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0705
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0799
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0798
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3415
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5602
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4752
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2523
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1283
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-9766
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3885
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6720
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0702
+ Oracle Linux Bulletin - April 2016
http://www.oracle.com/technetwork/topics/security/linuxbulletinapr2016-2952096.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-5325
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2315
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2324
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1521
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1522
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1523
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0636
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0636
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1526
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2114
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7810
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0774
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0774
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8327
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8560
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0546
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1978
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1979
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2047
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1908
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4879
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5600
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2113
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8631
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4792
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4802
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4815
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4816
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4826
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4830
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4836
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4858
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4861
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4870
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4913
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0505
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0596
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0597
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0616
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0598
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0600
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0606
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0608
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8629
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8630
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0609
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4819
+ SA70087 Symantec Messaging Gateway AD Password Disclosure Vulnerability
https://secunia.com/advisories/70087/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2203
+ SA70079 Xen x86 Shadow Pagetables Superpage Mapping Vulnerability
https://secunia.com/advisories/70079/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3960
+ Java Platform, Standard Edition 8 Update 91 (Java SE 8u91) and 8 Update 92 (Java SE 8u92) are Now Available
http://www.oracle.com/technetwork/java/javase/8u92-relnotes-2949471.html
http://www.oracle.com/technetwork/java/javase/8u91-relnotes-2949462.html
+ Beta 2 (pre-release 5) of OpenSSL 1.1.0 is now available: please download and test it
https://www.openssl.org/
Postgres-XL 9.5 R1 Released!
http://www.postgresql.org/about/news/1662/
JVNDB-2016-000050 スマートフォンアプリ「Photopt」における SSL サーバ証明書の検証不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000050.html
図解で手口を学ぶ「脆弱性」セキュリティ
図解でわかるHeartBleed
http://itpro.nikkeibp.co.jp/atcl/column/16/041400084/041400003/?ST=security
サイバークライムアナリストが明かす標的型攻撃の実像
手法再現で理解する、標的型攻撃を受けた端末は一体何をされるのか(1)
http://itpro.nikkeibp.co.jp/atcl/column/16/041300083/041500002/?ST=security
アイキューブドシステムズ、MDMのオプションで電子証明書を販売
http://itpro.nikkeibp.co.jp/atcl/news/16/041901147/?ST=security
ウェブルートが脅威レポートを発表、「もはや自動検出では対応できない」
http://itpro.nikkeibp.co.jp/atcl/news/16/041901144/?ST=security
2016年4月19日火曜日
19日 火曜日、先負
+ Apache Tomcat 7.0.69 Released
http://tomcat.apache.org/tomcat-7.0-doc/changelog.html
+ UPDATE: JVNVU#92232364 Microsoft Windows および Samba の認証機能に脆弱性 ("Badlock")
http://jvn.jp/vu/JVNVU92232364/
+ UPDATE: JVNVU#95402108 ISC BIND にサービス運用妨害 (DoS) の脆弱性
http://jvn.jp/vu/JVNVU95402108/
+ UPADTE: JVNVU#96567499 ISC DHCP にサービス運用妨害 (DoS) の脆弱性
http://jvn.jp/vu/JVNVU96567499/
+ UPDATE: JVNTA#92371676 QuickTime for Windows に複数のヒープバッファオーバフローの脆弱性
http://jvn.jp/ta/JVNTA92371676/index.html
+ Xen x86 Shadow Pagetable Overflow Lets Local Guest Users Deny Service and Potentially Gain Elevated Privileges on the Host System
http://www.securitytracker.com/id/1035587
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3960
+ NetBSD calendar(1) Permission Flaw Lets Local Users Obtain Elevated Privileges
http://www.securitytracker.com/id/1035585
PostgresOpen 2016 - Call For Papers!
http://www.postgresql.org/about/news/1663/
pgBackRest 1.0 Released
http://www.postgresql.org/about/news/1661/
図解で手口を学ぶ「脆弱性」セキュリティ
図解でわかるバッファーオーバーフロー
http://itpro.nikkeibp.co.jp/atcl/column/16/041400084/041400002/?ST=security
記者の眼
事前準備ゼロで「情報セキュリティマネジメント試験」を受けてみた
http://itpro.nikkeibp.co.jp/atcl/watcher/14/334361/041800539/?ST=security
サイバークライムアナリストが明かす標的型攻撃の実像
攻撃者視点で考えるサイバーアタック、異常すぎる「普通の動き」を検知できるかがポイント
http://itpro.nikkeibp.co.jp/atcl/column/16/041300083/041400001/?ST=security
改正サイバー法が成立、国家資格「情報処理安全確保支援士」を新設
http://itpro.nikkeibp.co.jp/atcl/news/16/041801134/?ST=security
UPDATE: JVN#82020528 Aterm WG300HP におけるクロスサイトリクエストフォージェリの脆弱性
http://jvn.jp/jp/JVN82020528/
UPDATE: JVN#07818796 Aterm WF800HP におけるクロスサイトリクエストフォージェリの脆弱性
http://jvn.jp/jp/JVN07818796/
http://tomcat.apache.org/tomcat-7.0-doc/changelog.html
+ UPDATE: JVNVU#92232364 Microsoft Windows および Samba の認証機能に脆弱性 ("Badlock")
http://jvn.jp/vu/JVNVU92232364/
+ UPDATE: JVNVU#95402108 ISC BIND にサービス運用妨害 (DoS) の脆弱性
http://jvn.jp/vu/JVNVU95402108/
+ UPADTE: JVNVU#96567499 ISC DHCP にサービス運用妨害 (DoS) の脆弱性
http://jvn.jp/vu/JVNVU96567499/
+ UPDATE: JVNTA#92371676 QuickTime for Windows に複数のヒープバッファオーバフローの脆弱性
http://jvn.jp/ta/JVNTA92371676/index.html
+ Xen x86 Shadow Pagetable Overflow Lets Local Guest Users Deny Service and Potentially Gain Elevated Privileges on the Host System
http://www.securitytracker.com/id/1035587
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3960
+ NetBSD calendar(1) Permission Flaw Lets Local Users Obtain Elevated Privileges
http://www.securitytracker.com/id/1035585
PostgresOpen 2016 - Call For Papers!
http://www.postgresql.org/about/news/1663/
pgBackRest 1.0 Released
http://www.postgresql.org/about/news/1661/
図解で手口を学ぶ「脆弱性」セキュリティ
図解でわかるバッファーオーバーフロー
http://itpro.nikkeibp.co.jp/atcl/column/16/041400084/041400002/?ST=security
記者の眼
事前準備ゼロで「情報セキュリティマネジメント試験」を受けてみた
http://itpro.nikkeibp.co.jp/atcl/watcher/14/334361/041800539/?ST=security
サイバークライムアナリストが明かす標的型攻撃の実像
攻撃者視点で考えるサイバーアタック、異常すぎる「普通の動き」を検知できるかがポイント
http://itpro.nikkeibp.co.jp/atcl/column/16/041300083/041400001/?ST=security
改正サイバー法が成立、国家資格「情報処理安全確保支援士」を新設
http://itpro.nikkeibp.co.jp/atcl/news/16/041801134/?ST=security
UPDATE: JVN#82020528 Aterm WG300HP におけるクロスサイトリクエストフォージェリの脆弱性
http://jvn.jp/jp/JVN82020528/
UPDATE: JVN#07818796 Aterm WF800HP におけるクロスサイトリクエストフォージェリの脆弱性
http://jvn.jp/jp/JVN07818796/
2016年4月18日月曜日
18日 月曜日、友引
+ psqlodbc_09_05_0210 released
http://www.postgresql.org/ftp/odbc/versions/msi/
+ UPDATE: Cisco Prime Infrastructure and Evolved Programmable Network Manager Privilege Escalation API Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160406-privauth
+ SA70040 VMware Multiple Products VMware Client Integration Plugin Session Hijacking Vulnerability
https://secunia.com/advisories/70040/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2076
+ SA70031 Linux Kernel Xen PV x86 hugelbfs Denial of Service Vulnerability
https://secunia.com/advisories/70031/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3961
+ GCC 6.1 released
https://gcc.gnu.org/gcc-6/changes.html
+ UPDATE: JVNVU#92232364 Microsoft Windows および Samba の認証機能に脆弱性 ("Badlock")
http://jvn.jp/vu/JVNVU92232364/
+ JVNTA#92371676 QuickTime for Windows に複数のヒープバッファオーバフローの脆弱性
http://jvn.jp/ta/JVNTA92371676/
+ Apple QuickTime for Windows Heap Overflows in Processing Files Lets Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1035579
+ Microsoft Internet Explorer 11 MSHTML.DLL Remote Binary Planting Vulnerability
https://cxsecurity.com/issue/WLB-2016040113
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0160
+ Microsoft Office Excel Out-of-Bounds Read Remote Code Execution
https://cxsecurity.com/issue/WLB-2016040107
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0122
+ Internet Explorer 9, 10, 11 - CDOMStringDataList::InitFromString Out-of-Bounds Read
https://cxsecurity.com/issue/WLB-2016040105
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-6086
Amazon RDS for PostgreSQL now supports PostgreSQL 9.5
http://www.postgresql.org/about/news/1659/
+ Sysstat 11.2.3 released
http://sebastien.godard.pagesperso-orange.fr/
図解で手口を学ぶ「脆弱性」セキュリティ
図解でわかる脆弱性でひどい目に遭う理由
http://itpro.nikkeibp.co.jp/atcl/column/16/041400084/041400001/?ST=security
チェックしておきたい脆弱性情報<2016.04.18>
http://itpro.nikkeibp.co.jp/atcl/column/14/268561/041400109/?ST=security
パロアルト、マルウエア対策サンドボックスにOS X環境を追加
http://itpro.nikkeibp.co.jp/atcl/news/16/041501106/?ST=security
DNP、個人番号カードを本人確認に活用できるようにするサービスを発表
http://itpro.nikkeibp.co.jp/atcl/news/16/041501105/?ST=security
Microsoftが米政府を提訴、「顧客データ要請の守秘命令は違憲」
http://itpro.nikkeibp.co.jp/atcl/news/16/041501096/?ST=security
[データは語る]2016年第1四半期のインシデントは4587件、前期比で33%増加―JPCERT/CC
http://itpro.nikkeibp.co.jp/atcl/news/14/110601779/041400581/?ST=security
[データは語る]2016年度の情報セキュリティ投資が「増加する」企業は27.0%―IDC
http://itpro.nikkeibp.co.jp/atcl/news/14/110601779/041400579/?ST=security
HTTPSの証明書を無料で発行する「Let's Encrypt」、正式版へ移行
http://internet.watch.impress.co.jp/docs/news/20160414_753266.html
http://www.postgresql.org/ftp/odbc/versions/msi/
+ UPDATE: Cisco Prime Infrastructure and Evolved Programmable Network Manager Privilege Escalation API Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160406-privauth
+ SA70040 VMware Multiple Products VMware Client Integration Plugin Session Hijacking Vulnerability
https://secunia.com/advisories/70040/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2076
+ SA70031 Linux Kernel Xen PV x86 hugelbfs Denial of Service Vulnerability
https://secunia.com/advisories/70031/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3961
+ GCC 6.1 released
https://gcc.gnu.org/gcc-6/changes.html
+ UPDATE: JVNVU#92232364 Microsoft Windows および Samba の認証機能に脆弱性 ("Badlock")
http://jvn.jp/vu/JVNVU92232364/
+ JVNTA#92371676 QuickTime for Windows に複数のヒープバッファオーバフローの脆弱性
http://jvn.jp/ta/JVNTA92371676/
+ Apple QuickTime for Windows Heap Overflows in Processing Files Lets Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1035579
+ Microsoft Internet Explorer 11 MSHTML.DLL Remote Binary Planting Vulnerability
https://cxsecurity.com/issue/WLB-2016040113
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0160
+ Microsoft Office Excel Out-of-Bounds Read Remote Code Execution
https://cxsecurity.com/issue/WLB-2016040107
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0122
+ Internet Explorer 9, 10, 11 - CDOMStringDataList::InitFromString Out-of-Bounds Read
https://cxsecurity.com/issue/WLB-2016040105
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-6086
Amazon RDS for PostgreSQL now supports PostgreSQL 9.5
http://www.postgresql.org/about/news/1659/
+ Sysstat 11.2.3 released
http://sebastien.godard.pagesperso-orange.fr/
図解で手口を学ぶ「脆弱性」セキュリティ
図解でわかる脆弱性でひどい目に遭う理由
http://itpro.nikkeibp.co.jp/atcl/column/16/041400084/041400001/?ST=security
チェックしておきたい脆弱性情報<2016.04.18>
http://itpro.nikkeibp.co.jp/atcl/column/14/268561/041400109/?ST=security
パロアルト、マルウエア対策サンドボックスにOS X環境を追加
http://itpro.nikkeibp.co.jp/atcl/news/16/041501106/?ST=security
DNP、個人番号カードを本人確認に活用できるようにするサービスを発表
http://itpro.nikkeibp.co.jp/atcl/news/16/041501105/?ST=security
Microsoftが米政府を提訴、「顧客データ要請の守秘命令は違憲」
http://itpro.nikkeibp.co.jp/atcl/news/16/041501096/?ST=security
[データは語る]2016年第1四半期のインシデントは4587件、前期比で33%増加―JPCERT/CC
http://itpro.nikkeibp.co.jp/atcl/news/14/110601779/041400581/?ST=security
[データは語る]2016年度の情報セキュリティ投資が「増加する」企業は27.0%―IDC
http://itpro.nikkeibp.co.jp/atcl/news/14/110601779/041400579/?ST=security
HTTPSの証明書を無料で発行する「Let's Encrypt」、正式版へ移行
http://internet.watch.impress.co.jp/docs/news/20160414_753266.html
2016年4月15日金曜日
15日 金曜日、大安
+ RHSA-2016:0621 Important: samba security update
https://rhn.redhat.com/errata/RHSA-2016-0621.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ Cisco Unified Computing System Platform Emulator Command Injection Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160414-ucspe1
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1339
+ Cisco Unified Computing System Platform Emulator Filename Argument Handling Buffer Overflow Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160414-ucspe2
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1340
+ SA70041 Google Chrome Multiple Vulnerabilities
https://secunia.com/advisories/70041/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1651
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1652
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1653
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1654
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1655
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1657
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1659
+ Oracle Critical Patch Update Pre-Release Announcement - April 2016
http://www.oracle.com/technetwork/topics/security/cpuapr2016-2881694.html
+ VMSA-2016-0004 VMware product updates address a critical security issue in the VMware Client Integration Plugin
http://www.vmware.com/security/advisories/VMSA-2016-0004.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2076
+ VMware vCenter Server VMware Client Integration Plugin Session Handling Flaw Lets Remote Users Hijack the Target User's Session
http://www.securitytracker.com/id/1035572
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2076
+ VMware vCloud Director VMware Client Integration Plugin Session Handling Flaw Lets Remote Users Hijack the Target User's Session
http://www.securitytracker.com/id/1035571
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2076
+ VMware vRealize Automation Identity Appliance VMware Client Integration Plugin Session Handling Flaw Lets Remote Users Hijack the Target User's Session
http://www.securitytracker.com/id/1035570
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2076
+ Dell OpenManage Server Administrator Input Validation Flaw Lets Remote Authenticated Users View Files on the Target System
http://www.securitytracker.com/id/1035564
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4004
E-Maj 1.3.0 is released
http://www.postgresql.org/about/news/1657/
https://rhn.redhat.com/errata/RHSA-2016-0621.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ Cisco Unified Computing System Platform Emulator Command Injection Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160414-ucspe1
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1339
+ Cisco Unified Computing System Platform Emulator Filename Argument Handling Buffer Overflow Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160414-ucspe2
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1340
+ SA70041 Google Chrome Multiple Vulnerabilities
https://secunia.com/advisories/70041/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1651
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1652
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1653
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1654
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1655
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1657
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1659
+ Oracle Critical Patch Update Pre-Release Announcement - April 2016
http://www.oracle.com/technetwork/topics/security/cpuapr2016-2881694.html
+ VMSA-2016-0004 VMware product updates address a critical security issue in the VMware Client Integration Plugin
http://www.vmware.com/security/advisories/VMSA-2016-0004.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2076
+ VMware vCenter Server VMware Client Integration Plugin Session Handling Flaw Lets Remote Users Hijack the Target User's Session
http://www.securitytracker.com/id/1035572
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2076
+ VMware vCloud Director VMware Client Integration Plugin Session Handling Flaw Lets Remote Users Hijack the Target User's Session
http://www.securitytracker.com/id/1035571
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2076
+ VMware vRealize Automation Identity Appliance VMware Client Integration Plugin Session Handling Flaw Lets Remote Users Hijack the Target User's Session
http://www.securitytracker.com/id/1035570
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2076
+ Dell OpenManage Server Administrator Input Validation Flaw Lets Remote Authenticated Users View Files on the Target System
http://www.securitytracker.com/id/1035564
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-4004
E-Maj 1.3.0 is released
http://www.postgresql.org/about/news/1657/
2016年4月14日木曜日
14日 木曜日、仏滅
+ Google Chrome 50.0.2661.75 released
http://googlechromereleases.blogspot.jp/2016/04/stable-channel-update_13.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1652
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1653
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1651
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1654
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1655
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1656
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1657
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1658
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-1659
+ CESA-2016:0612 Critical CentOS 7 samba Security Update
http://lwn.net/Alerts/683695/
+ CESA-2016:0621 Important CentOS 5 samba Security Update
http://lwn.net/Alerts/683681/
+ CESA-2016:0612 Critical CentOS 7 libtevent Security Update
http://lwn.net/Alerts/683693/
+ CESA-2016:0612 Critical CentOS 6 openchange Security Update
http://lwn.net/Alerts/683687/
+ CESA-2016:0612 Critical CentOS 6 samba4 Security Update
http://lwn.net/Alerts/683688/
+ CESA-2016:0613 Critical CentOS 5 samba3x Security Update
http://lwn.net/Alerts/683696/
+ CESA-2016:0612 Critical CentOS 6 libtalloc Security Update
http://lwn.net/Alerts/683684/
+ CESA-2016:0612 Critical CentOS 6 libldb Security Update
http://lwn.net/Alerts/683683/
+ CESA-2016:0612 Critical CentOS 6 libtevent Security Update
http://lwn.net/Alerts/683686/
+ CESA-2016:0612 Critical CentOS 7 libldb Security Update
http://lwn.net/Alerts/683690/
+ CESA-2016:0612 Critical CentOS 7 ipa Security Update
http://lwn.net/Alerts/683689/
+ CESA-2016:0612 Critical CentOS 6 ipa Security Update
http://lwn.net/Alerts/683682/
+ CESA-2016:0612 Critical CentOS 7 libtalloc Security Update
http://lwn.net/Alerts/683691/
+ CESA-2016:0612 Critical CentOS 7 openchange Security Update
http://lwn.net/Alerts/683694/
+ CESA-2016:0611 Critical CentOS 6 samba Security Update
http://lwn.net/Alerts/683680/
+ CESA-2016:0612 Critical CentOS 7 libtdb Security Update
http://lwn.net/Alerts/683692/
+ CESA-2016:0612 Critical CentOS 6 libtdb Security Update
http://lwn.net/Alerts/683685/
+ Mozilla Thunderbird 45.0 released
https://www.mozilla.org/en-US/thunderbird/45.0/releasenotes/
+ Cisco Catalyst Switches Network Mobility Services Protocol Port Information Disclosure Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160413-nms
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1378
+ Cisco Unified Computing System Central Software Arbitrary Command Execution Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160413-ucs
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1352
+ Linux kernel 3.12.58 released
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.12.58
+ SA70055 Samba Multiple Vulnerabilities
https://secunia.com/advisories/70055/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ SA70007 Samba Multiple Vulnerabilities
https://secunia.com/advisories/70007/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2113
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ SA70056 McAfee Web Gateway Multiple Vulnerabilities
https://secunia.com/advisories/70056/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0705
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0787
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0797
+ JVNVU#92232364 Microsoft Windows および Samba の認証機能に脆弱性 ("Badlock")
http://jvn.jp/vu/JVNVU92232364/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0128
JVNDB-2016-000049 スマートフォンアプリ「東京スター銀行アプリ」における SSL サーバ証明書の検証不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000049.html
JVN#00272277 スマートフォンアプリ「東京スター銀行アプリ」における SSL サーバ証明書の検証不備の脆弱性
http://jvn.jp/jp/JVN00272277/
LINE×サイボウズのバグバウンティ対談
サイボウズとLINEが語る報奨金制度、脆弱性報告への報酬金額はどうやって決める?
http://itpro.nikkeibp.co.jp/atcl/column/16/040600081/040700002/?ST=security
http://googlechromereleases.blogspot.jp/2016/04/stable-channel-update_13.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1652
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1653
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1651
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1654
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1655
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1656
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1657
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1658
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-1659
+ CESA-2016:0612 Critical CentOS 7 samba Security Update
http://lwn.net/Alerts/683695/
+ CESA-2016:0621 Important CentOS 5 samba Security Update
http://lwn.net/Alerts/683681/
+ CESA-2016:0612 Critical CentOS 7 libtevent Security Update
http://lwn.net/Alerts/683693/
+ CESA-2016:0612 Critical CentOS 6 openchange Security Update
http://lwn.net/Alerts/683687/
+ CESA-2016:0612 Critical CentOS 6 samba4 Security Update
http://lwn.net/Alerts/683688/
+ CESA-2016:0613 Critical CentOS 5 samba3x Security Update
http://lwn.net/Alerts/683696/
+ CESA-2016:0612 Critical CentOS 6 libtalloc Security Update
http://lwn.net/Alerts/683684/
+ CESA-2016:0612 Critical CentOS 6 libldb Security Update
http://lwn.net/Alerts/683683/
+ CESA-2016:0612 Critical CentOS 6 libtevent Security Update
http://lwn.net/Alerts/683686/
+ CESA-2016:0612 Critical CentOS 7 libldb Security Update
http://lwn.net/Alerts/683690/
+ CESA-2016:0612 Critical CentOS 7 ipa Security Update
http://lwn.net/Alerts/683689/
+ CESA-2016:0612 Critical CentOS 6 ipa Security Update
http://lwn.net/Alerts/683682/
+ CESA-2016:0612 Critical CentOS 7 libtalloc Security Update
http://lwn.net/Alerts/683691/
+ CESA-2016:0612 Critical CentOS 7 openchange Security Update
http://lwn.net/Alerts/683694/
+ CESA-2016:0611 Critical CentOS 6 samba Security Update
http://lwn.net/Alerts/683680/
+ CESA-2016:0612 Critical CentOS 7 libtdb Security Update
http://lwn.net/Alerts/683692/
+ CESA-2016:0612 Critical CentOS 6 libtdb Security Update
http://lwn.net/Alerts/683685/
+ Mozilla Thunderbird 45.0 released
https://www.mozilla.org/en-US/thunderbird/45.0/releasenotes/
+ Cisco Catalyst Switches Network Mobility Services Protocol Port Information Disclosure Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160413-nms
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1378
+ Cisco Unified Computing System Central Software Arbitrary Command Execution Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160413-ucs
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1352
+ Linux kernel 3.12.58 released
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.12.58
+ SA70055 Samba Multiple Vulnerabilities
https://secunia.com/advisories/70055/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ SA70007 Samba Multiple Vulnerabilities
https://secunia.com/advisories/70007/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2113
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ SA70056 McAfee Web Gateway Multiple Vulnerabilities
https://secunia.com/advisories/70056/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0705
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0787
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0797
+ JVNVU#92232364 Microsoft Windows および Samba の認証機能に脆弱性 ("Badlock")
http://jvn.jp/vu/JVNVU92232364/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0128
JVNDB-2016-000049 スマートフォンアプリ「東京スター銀行アプリ」における SSL サーバ証明書の検証不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000049.html
JVN#00272277 スマートフォンアプリ「東京スター銀行アプリ」における SSL サーバ証明書の検証不備の脆弱性
http://jvn.jp/jp/JVN00272277/
LINE×サイボウズのバグバウンティ対談
サイボウズとLINEが語る報奨金制度、脆弱性報告への報酬金額はどうやって決める?
http://itpro.nikkeibp.co.jp/atcl/column/16/040600081/040700002/?ST=security
2016年4月13日水曜日
13日 水曜日、先負
+ 2016 年 4 月のマイクロソフト セキュリティ情報の概要
https://technet.microsoft.com/ja-jp/library/security/ms16-apr
+ MS16-037 - 緊急 Internet Explorer 用の累積的なセキュリティ更新プログラム (3148531)
https://technet.microsoft.com/library/security/MS16-037
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0154
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0159
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0160
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0162
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0164
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0166
+ MS16-038 - 緊急 Microsoft Edge 用の累積的なセキュリティ更新プログラム (3148532)
https://technet.microsoft.com/library/security/MS16-038
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0154
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0155
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0156
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0157
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0158
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0161
+ MS16-039 - 緊急 Microsoft Graphics コンポーネントのセキュリティ更新プログラム (3148522)
https://technet.microsoft.com/library/security/MS16-039
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0143
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0165
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0167
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0145
+ MS16-040 - 緊急 Microsoft XML Core Services 3148541 用のセキュリティ更新プログラム (3148541)
https://technet.microsoft.com/library/security/MS16-040
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0147
+ MS16-041 - 重要 .NET Framework 用のセキュリティ更新プログラム (3148789)
https://technet.microsoft.com/library/security/MS16-041
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0148
+ MS16-042 - 緊急 Microsoft Office 用のセキュリティ更新プログラム (3148775)
https://technet.microsoft.com/library/security/MS16-042
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0122
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0127
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0136
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0139
+ MS16-044 - 重要 Windows OLE 用のセキュリティ更新プログラム (3146706)
https://technet.microsoft.com/library/security/MS16-044
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0153
+ MS16-045 - 重要 Windows Hyper-V 用のセキュリティ更新プログラム (3143118)
https://technet.microsoft.com/library/security/MS16-045
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0088
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0089
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0090
+ MS16-046 - 重要 セカンダリ ログオン用のセキュリティ更新プログラム (3148538)
https://technet.microsoft.com/library/security/MS16-046
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0135
+ MS16-047 - 重要 SAM および LSAD リモート プロトコル用のセキュリティ更新プログラム (3148527)
https://technet.microsoft.com/library/security/MS16-047
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0128
+ MS16-048 - 重要 CSRSS 用のセキュリティ更新プログラム (3148528)
https://technet.microsoft.com/library/security/MS16-048
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0151
+ MS16-049 - 重要 HTTP.sys 用のセキュリティ更新プログラム (3148795)
https://technet.microsoft.com/library/security/MS16-049
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0150
+ MS16-050 - 緊急 Adobe Flash Player のセキュリティ更新プログラム (3154132)
https://technet.microsoft.com/library/security/MS16-050
+ マイクロソフト セキュリティ アドバイザリ 3152550 ワイヤレス マウス入力のフィルタリングを改善する更新プログラム
https://technet.microsoft.com/ja-jp/library/security/3152550
+ RHSA-2016:0621 Important: samba security update
https://rhn.redhat.com/errata/RHSA-2016-0621.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ RHSA-2016:0613 Critical: samba3x security update
https://rhn.redhat.com/errata/RHSA-2016-0613.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ RHSA-2016:0612 Critical: samba and samba4 security, bug fix, and enhancement update
https://rhn.redhat.com/errata/RHSA-2016-0612.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2113
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2114
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ RHSA-2016:0611 Critical: samba security update
https://rhn.redhat.com/errata/RHSA-2016-0611.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ APSB16-12 Security hotfix available for RoboHelp Server
https://helpx.adobe.com/security/products/robohelp-server/apsb16-12.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1035
+ APSB16-11 Security update available for the Creative Cloud Desktop Application
https://helpx.adobe.com/security/products/creative-cloud/apsb16-11.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1034
+ APSB16-10 Security updates available for Adobe Flash Player
https://helpx.adobe.com/security/products/flash-player/apsb16-10.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1006
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1011
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1012
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1013
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1014
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1015
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1016
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1017
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1018
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1019
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1020
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1021
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1022
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1023
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1024
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1025
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1026
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1027
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1028
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1029
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1030
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1031
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1032
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1033
+ Cisco Unity Connection Cross-Site Scripting Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160412-unity
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1377
+ Cisco IOS XR for Cisco ASR 9000 Series Aggregation Services Routers Interface Flap Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160412-asr
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1376
+ sk110978 Check Point Response to BadLock vulnerabilities
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk110978&src=securityAlerts
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0128
+ VU#813296 Microsoft Windows and Samba may allow spoofing of authenticated users ("Badlock")
https://www.kb.cert.org/vuls/id/813296
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0128
+ Linux kernel 4.5.1, 4.4.7, 3.14.66 released
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.5.1
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.4.7
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.14.66
+ UPDATE: Oracle Solaris Third Party Bulletin - January 2016
http://www.oracle.com/technetwork/topics/security/bulletinjan2016-2867206.html
+ Samba 4.4.2, 4.3.8 and 4.2.11 Security Releases Available for Download
https://www.samba.org/samba/latest_news.html#4.4.2
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2113
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2114
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ SA69985 Oracle MySQL OpenSSL Multiple Denial of Service Vulnerabilities
https://secunia.com/advisories/69985/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0705
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0797
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0798
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0799
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2842
+ Apache Ant 1.9.7 Released
http://ant.apache.org/
+ Android - IMemory Native Interface is Insecure for IPC Use
https://cxsecurity.com/issue/WLB-2016040083
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0846
+ Android - IOMX getConfig/getParameter Information Disclosure
https://cxsecurity.com/issue/WLB-2016040084
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2417
+ Perl 5.22 VDir::MapPathA/W Out-Of-Bounds Reads / Buffer Over-Reads
https://cxsecurity.com/issue/WLB-2016040080
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8608
PGConf US 2016 One Week Away - Registrations Closing
http://www.postgresql.org/about/news/1658/
LINE×サイボウズのバグバウンティ対談
先進2社が語るバグ報奨金制度、「やはり社内でも反対意見はありました」
http://itpro.nikkeibp.co.jp/atcl/column/16/040600081/040700001/?ST=security
UPDATE: JVNVU#92749596 BlueDriver LSB2 に認証なしで Bluetooth アクセスが可能な問題
http://jvn.jp/vu/JVNVU92749596/index.html
https://technet.microsoft.com/ja-jp/library/security/ms16-apr
+ MS16-037 - 緊急 Internet Explorer 用の累積的なセキュリティ更新プログラム (3148531)
https://technet.microsoft.com/library/security/MS16-037
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0154
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0159
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0160
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0162
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0164
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0166
+ MS16-038 - 緊急 Microsoft Edge 用の累積的なセキュリティ更新プログラム (3148532)
https://technet.microsoft.com/library/security/MS16-038
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0154
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0155
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0156
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0157
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0158
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0161
+ MS16-039 - 緊急 Microsoft Graphics コンポーネントのセキュリティ更新プログラム (3148522)
https://technet.microsoft.com/library/security/MS16-039
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0143
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0165
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0167
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0145
+ MS16-040 - 緊急 Microsoft XML Core Services 3148541 用のセキュリティ更新プログラム (3148541)
https://technet.microsoft.com/library/security/MS16-040
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0147
+ MS16-041 - 重要 .NET Framework 用のセキュリティ更新プログラム (3148789)
https://technet.microsoft.com/library/security/MS16-041
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0148
+ MS16-042 - 緊急 Microsoft Office 用のセキュリティ更新プログラム (3148775)
https://technet.microsoft.com/library/security/MS16-042
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0122
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0127
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0136
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0139
+ MS16-044 - 重要 Windows OLE 用のセキュリティ更新プログラム (3146706)
https://technet.microsoft.com/library/security/MS16-044
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0153
+ MS16-045 - 重要 Windows Hyper-V 用のセキュリティ更新プログラム (3143118)
https://technet.microsoft.com/library/security/MS16-045
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0088
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0089
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0090
+ MS16-046 - 重要 セカンダリ ログオン用のセキュリティ更新プログラム (3148538)
https://technet.microsoft.com/library/security/MS16-046
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0135
+ MS16-047 - 重要 SAM および LSAD リモート プロトコル用のセキュリティ更新プログラム (3148527)
https://technet.microsoft.com/library/security/MS16-047
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0128
+ MS16-048 - 重要 CSRSS 用のセキュリティ更新プログラム (3148528)
https://technet.microsoft.com/library/security/MS16-048
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0151
+ MS16-049 - 重要 HTTP.sys 用のセキュリティ更新プログラム (3148795)
https://technet.microsoft.com/library/security/MS16-049
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0150
+ MS16-050 - 緊急 Adobe Flash Player のセキュリティ更新プログラム (3154132)
https://technet.microsoft.com/library/security/MS16-050
+ マイクロソフト セキュリティ アドバイザリ 3152550 ワイヤレス マウス入力のフィルタリングを改善する更新プログラム
https://technet.microsoft.com/ja-jp/library/security/3152550
+ RHSA-2016:0621 Important: samba security update
https://rhn.redhat.com/errata/RHSA-2016-0621.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ RHSA-2016:0613 Critical: samba3x security update
https://rhn.redhat.com/errata/RHSA-2016-0613.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ RHSA-2016:0612 Critical: samba and samba4 security, bug fix, and enhancement update
https://rhn.redhat.com/errata/RHSA-2016-0612.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2113
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2114
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ RHSA-2016:0611 Critical: samba security update
https://rhn.redhat.com/errata/RHSA-2016-0611.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ APSB16-12 Security hotfix available for RoboHelp Server
https://helpx.adobe.com/security/products/robohelp-server/apsb16-12.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1035
+ APSB16-11 Security update available for the Creative Cloud Desktop Application
https://helpx.adobe.com/security/products/creative-cloud/apsb16-11.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1034
+ APSB16-10 Security updates available for Adobe Flash Player
https://helpx.adobe.com/security/products/flash-player/apsb16-10.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1006
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1011
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1012
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1013
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1014
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1015
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1016
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1017
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1018
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1019
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1020
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1021
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1022
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1023
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1024
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1025
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1026
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1027
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1028
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1029
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1030
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1031
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1032
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1033
+ Cisco Unity Connection Cross-Site Scripting Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160412-unity
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1377
+ Cisco IOS XR for Cisco ASR 9000 Series Aggregation Services Routers Interface Flap Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160412-asr
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1376
+ sk110978 Check Point Response to BadLock vulnerabilities
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk110978&src=securityAlerts
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0128
+ VU#813296 Microsoft Windows and Samba may allow spoofing of authenticated users ("Badlock")
https://www.kb.cert.org/vuls/id/813296
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0128
+ Linux kernel 4.5.1, 4.4.7, 3.14.66 released
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.5.1
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.4.7
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.14.66
+ UPDATE: Oracle Solaris Third Party Bulletin - January 2016
http://www.oracle.com/technetwork/topics/security/bulletinjan2016-2867206.html
+ Samba 4.4.2, 4.3.8 and 4.2.11 Security Releases Available for Download
https://www.samba.org/samba/latest_news.html#4.4.2
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5370
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2110
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2111
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2112
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2113
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2114
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2115
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2118
+ SA69985 Oracle MySQL OpenSSL Multiple Denial of Service Vulnerabilities
https://secunia.com/advisories/69985/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0705
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0797
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0798
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0799
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2842
+ Apache Ant 1.9.7 Released
http://ant.apache.org/
+ Android - IMemory Native Interface is Insecure for IPC Use
https://cxsecurity.com/issue/WLB-2016040083
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0846
+ Android - IOMX getConfig/getParameter Information Disclosure
https://cxsecurity.com/issue/WLB-2016040084
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2417
+ Perl 5.22 VDir::MapPathA/W Out-Of-Bounds Reads / Buffer Over-Reads
https://cxsecurity.com/issue/WLB-2016040080
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8608
PGConf US 2016 One Week Away - Registrations Closing
http://www.postgresql.org/about/news/1658/
LINE×サイボウズのバグバウンティ対談
先進2社が語るバグ報奨金制度、「やはり社内でも反対意見はありました」
http://itpro.nikkeibp.co.jp/atcl/column/16/040600081/040700001/?ST=security
UPDATE: JVNVU#92749596 BlueDriver LSB2 に認証なしで Bluetooth アクセスが可能な問題
http://jvn.jp/vu/JVNVU92749596/index.html
2016年4月12日火曜日
12日 火曜日、友引
+ Mozilla Firefox 45.0.2 released
https://www.mozilla.org/en-US/firefox/45.0.2/releasenotes/
+ UPDATE: Multiple Vulnerabilities in OpenSSL Affecting Cisco Products: March 2016
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160302-openssl
+ MySQL 5.7.12, 5.6.30, 5.5.49 released
http://dev.mysql.com/doc/relnotes/mysql/5.7/en/news-5-7-12.html
http://dev.mysql.com/doc/relnotes/mysql/5.6/en/news-5-6-30.html
http://dev.mysql.com/doc/relnotes/mysql/5.5/en/news-5-5-49.html
+ Apple Intel HD 3000 Graphics Driver 10.0.0 Privilege Escalation
https://cxsecurity.com/issue/WLB-2016040064
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1743
https://www.mozilla.org/en-US/firefox/45.0.2/releasenotes/
+ UPDATE: Multiple Vulnerabilities in OpenSSL Affecting Cisco Products: March 2016
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160302-openssl
+ MySQL 5.7.12, 5.6.30, 5.5.49 released
http://dev.mysql.com/doc/relnotes/mysql/5.7/en/news-5-7-12.html
http://dev.mysql.com/doc/relnotes/mysql/5.6/en/news-5-6-30.html
http://dev.mysql.com/doc/relnotes/mysql/5.5/en/news-5-5-49.html
+ Apple Intel HD 3000 Graphics Driver 10.0.0 Privilege Escalation
https://cxsecurity.com/issue/WLB-2016040064
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1743
2016年4月11日月曜日
11日 月曜日、先勝
+ psqlodbc 09.05.0200 released
http://www.postgresql.org/ftp/odbc/versions/msi/
+ Symantec Altiris IT Management Suite Security Bypass Vulnerability
https://secunia.com/advisories/69954/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2202
+ Apache HTTP Server 2.4.20 Released
http://www.apache.org/dist/httpd/Announcement2.4.html
+ Adobe Flash Player Multiple Bugs Lets Remote Users Execute Arbitrary Code and Bypass Security Restrictions
http://www.securitytracker.com/id/1035509
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1006
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1011
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1012
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1013
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1014
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1015
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1016
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1017
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1018
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1020
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1021
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1022
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1023
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1024
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1025
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1026
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1027
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1028
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1029
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1030
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1031
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1032
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1033
+ PostgreSQL CREATE LANGUAGE Execution
https://cxsecurity.com/issue/WLB-2016040060
JVNDB-2016-000048 EC-CUBE 用プラグイン「ソーシャルボタン設置プラグイン -プレミアム-」におけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000048.html
JVNVU#92749596 BlueDriver LSB2 に Bluetooth アクセスを認証しない問題
http://jvn.jp/vu/JVNVU92749596/
チェックしておきたい脆弱性情報<2016.04.11>
http://itpro.nikkeibp.co.jp/atcl/column/14/268561/033100108/?ST=security
http://www.postgresql.org/ftp/odbc/versions/msi/
+ Symantec Altiris IT Management Suite Security Bypass Vulnerability
https://secunia.com/advisories/69954/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2202
+ Apache HTTP Server 2.4.20 Released
http://www.apache.org/dist/httpd/Announcement2.4.html
+ Adobe Flash Player Multiple Bugs Lets Remote Users Execute Arbitrary Code and Bypass Security Restrictions
http://www.securitytracker.com/id/1035509
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1006
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1011
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1012
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1013
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1014
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1015
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1016
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1017
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1018
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1020
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1021
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1022
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1023
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1024
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1025
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1026
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1027
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1028
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1029
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1030
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1031
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1032
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1033
+ PostgreSQL CREATE LANGUAGE Execution
https://cxsecurity.com/issue/WLB-2016040060
JVNDB-2016-000048 EC-CUBE 用プラグイン「ソーシャルボタン設置プラグイン -プレミアム-」におけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000048.html
JVNVU#92749596 BlueDriver LSB2 に Bluetooth アクセスを認証しない問題
http://jvn.jp/vu/JVNVU92749596/
チェックしておきたい脆弱性情報<2016.04.11>
http://itpro.nikkeibp.co.jp/atcl/column/14/268561/033100108/?ST=security
2016年4月8日金曜日
8日 金曜日、仏滅
+ Google Chrome 49.0.2623.112 released
http://googlechromereleases.blogspot.jp/2016/04/stable-channel-update.html
+ Cisco IP Interoperability and Collaboration System Cross-Site Scripting Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160407-cic
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1375
+ SA69912 McAfee Email Gateway Multiple Vulnerabilities
https://secunia.com/advisories/69912/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7181
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7183
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7547
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7981
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8000
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8126
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8472
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0705
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0797
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0798
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0799
+ LibTIFF Divide-by-Zero Error and Multiple Read Errors Let Remote Users Cause the Target Application to Crash
http://www.securitytracker.com/id/1035508
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3619
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3620
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3621
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3622
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3631
+ Linux ASLR Weakness Addressed
https://cxsecurity.com/issue/WLB-2016040049
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3672
VU#615456 Lemur Vehicle Monitors BlueDriver LSB2 does not authenticate users for Bluetooth access
https://www.kb.cert.org/vuls/id/615456
UPDATE: JVN#55801246 baserCMS 用プラグイン「ケースブックプラグイン」における複数の脆弱性
http://jvn.jp/jp/JVN55801246/index.html
UPDATE: JVN#26627848 baserCMS 用プラグイン「メニューブックプラグイン」における複数の脆弱性
http://jvn.jp/jp/JVN26627848/index.html
UPDATE: JVN#13288761 baserCMS 用プラグイン「求人情報プラグイン」における複数の脆弱性
http://jvn.jp/jp/JVN13288761/index.html
News & Trend
セキュリティ人材の発掘急げ、NECが初の全社セキュリティコンテスト
http://itpro.nikkeibp.co.jp/atcl/column/14/346926/040700503/?ST=security
暗号化された添付ファイルのみ送信、日立ソリューションズがFortiGateと秘文を連携
http://itpro.nikkeibp.co.jp/atcl/news/16/040701023/?ST=security
http://googlechromereleases.blogspot.jp/2016/04/stable-channel-update.html
+ Cisco IP Interoperability and Collaboration System Cross-Site Scripting Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160407-cic
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1375
+ SA69912 McAfee Email Gateway Multiple Vulnerabilities
https://secunia.com/advisories/69912/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7181
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7182
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7183
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7547
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7981
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8000
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8126
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8472
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0705
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0797
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0798
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0799
+ LibTIFF Divide-by-Zero Error and Multiple Read Errors Let Remote Users Cause the Target Application to Crash
http://www.securitytracker.com/id/1035508
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3619
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3620
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3621
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3622
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3631
+ Linux ASLR Weakness Addressed
https://cxsecurity.com/issue/WLB-2016040049
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3672
VU#615456 Lemur Vehicle Monitors BlueDriver LSB2 does not authenticate users for Bluetooth access
https://www.kb.cert.org/vuls/id/615456
UPDATE: JVN#55801246 baserCMS 用プラグイン「ケースブックプラグイン」における複数の脆弱性
http://jvn.jp/jp/JVN55801246/index.html
UPDATE: JVN#26627848 baserCMS 用プラグイン「メニューブックプラグイン」における複数の脆弱性
http://jvn.jp/jp/JVN26627848/index.html
UPDATE: JVN#13288761 baserCMS 用プラグイン「求人情報プラグイン」における複数の脆弱性
http://jvn.jp/jp/JVN13288761/index.html
News & Trend
セキュリティ人材の発掘急げ、NECが初の全社セキュリティコンテスト
http://itpro.nikkeibp.co.jp/atcl/column/14/346926/040700503/?ST=security
暗号化された添付ファイルのみ送信、日立ソリューションズがFortiGateと秘文を連携
http://itpro.nikkeibp.co.jp/atcl/news/16/040701023/?ST=security
2016年4月7日木曜日
7日 木曜日、先負
+ CVE-2016-1019 Security Advisory for Adobe Flash Player
https://helpx.adobe.com/security/products/flash-player/apsa16-01.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1019
+ CESA-2016:0591 Moderate CentOS 6 nss-util Security Update
http://lwn.net/Alerts/682730/
+ CESA-2016:0591 Moderate CentOS 6 nspr Security Update
http://lwn.net/Alerts/682728/
+ CESA-2016:0591 Moderate CentOS 6 nss Security Update
http://lwn.net/Alerts/682729/
+ CESA-2016:0594 Important CentOS 7 graphite2 Security Update
http://lwn.net/Alerts/682727/
+ Mozilla Thunderbird 38.7.2 released
https://www.mozilla.org/en-US/thunderbird/38.7.2/releasenotes/
+ UPDATE: Vulnerability in GNU glibc Affecting Cisco Products: February 2016
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160218-glibc
+ UPDATE: Cisco IOS XR Software SCP and SFTP Modules Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160323-ncs
+ UPDATE: Cisco Prime Infrastructure and Evolved Programmable Network Manager Privilege Escalation API Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160406-privauth
+ Cisco UCS Invicta Default SSH Key Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160406-ucs
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1313
+ Cisco TelePresence Server Crafted URL Handling Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160406-cts1
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-6313
+ Cisco TelePresence Server Crafted IPv6 Packet Handling Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160406-cts
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1346
+ Cisco Prime Infrastructure and Evolved Programmable Network Manager Remote Code Execution Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160406-remcode
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1291
+ Linux kernel 4.1.21, 3.18.30 released
https://cdn.kernel.org/pub/linux/kernel/v4.x/ChangeLog-4.1.21
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.18.30
+ Adobe Flash Player Flaw Lets Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1035491
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1019
JVNDB-2016-000045 baserCMS 用プラグイン「ケースブックプラグイン」におけるクロスサイトリクエストフォージェリの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000045.html
JVNDB-2016-000044 baserCMS 用プラグイン「ケースブックプラグイン」におけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000044.html
JVNDB-2016-000043 baserCMS 用プラグイン「メニューブックプラグイン」におけるクロスサイトリクエストフォージュリの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000043.html
JVNDB-2016-000042 baserCMS 用プラグイン「メニューブックプラグイン」におけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000042.html
JVNDB-2016-000041 baserCMS 用プラグイン「求人情報プラグイン」におけるクロスサイトリクエストフォージェリの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000041.html
JVNDB-2016-000040 baserCMS 用プラグイン「求人情報プラグイン」におけるクロスサイトスクリプティングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000040.html
瀧口範子のシリコンバレー通信シリコンバレー
OSベンダーだけじゃない、一般企業や政府も始めた「バグ発見報奨金制度」
http://itpro.nikkeibp.co.jp/atcl/column/15/060200138/040600044/?ST=security
デジタルアーツ、i-FILTERと米FireEyeとの連携オプションを強化
http://itpro.nikkeibp.co.jp/atcl/news/16/040601010/?ST=security
マイナンバーカードのICチップ不具合が大都市で多発、横浜市はシステム改修へ
http://itpro.nikkeibp.co.jp/atcl/news/16/040601008/?ST=security
ウイルスメールに注意! ユーザー名を固定してドメイン名を入れ替える珍しい手法
http://itpro.nikkeibp.co.jp/atcl/news/16/040601002/?ST=security
2016年4月6日水曜日
6日 水曜日、赤口
+ Gpg4win 2.3.1 released
https://www.gpg4win.org/change-history.html
+ RHSA-2016:0591 Moderate: nss, nss-util, and nspr security, bug fix, and enhancement update
https://rhn.redhat.com/errata/RHSA-2016-0591.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1978
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1979
+ RHSA-2016:0594 Important: graphite2 security, bug fix, and enhancement update
https://rhn.redhat.com/errata/RHSA-2016-0594.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1521
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1522
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1523
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1526
+ About the security content of iOS 9.3.1
https://support.apple.com/ja-jp/HT206225
+ nginx 1.9.14 released
http://nginx.org/en/CHANGES
+ SA69882 Android Multiple Vulnerabilities
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6060
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0834
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0835
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0836
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0837
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0838
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0839
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0840
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0841
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0842
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0850
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1503
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2416
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2417
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2418
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2419
+ PostgreSQL Bugs Let Remote Authenticated Users Access and Modify Data and Obtain Potentially Sensitive Information
http://www.securitytracker.com/id/1035468
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2193
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3065
+ Facebook Change cover Group with out acces admin
https://cxsecurity.com/issue/WLB-2016040027
CSAジャパンがIoTセキュリティのリスク評価ガイドを公開
http://itpro.nikkeibp.co.jp/atcl/news/16/040500986/?ST=security
JVNVU#90364741 Autodesk Backburner にスタックバッファオーバーフローの脆弱性
http://jvn.jp/vu/JVNVU90364741/index.html
2016年4月5日火曜日
5日 火曜日、大安
+ UPDATE: Cisco Videoscape Distribution Suite for Internet Streaming TCP Session Handling Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160226-vds-is
+ UPDATE: Cisco Unified Communications Domain Manager Cross-Site Scripting Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160328-ucdm
+ SA69837 Squid Two Vulnerabilities
https://secunia.com/advisories/69837/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3947
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3948
+ SA69852 Sharp AQUOS PhotoPlayer HN-PP150 Cross-Site Request Forgery Vulnerability
https://secunia.com/advisories/69852/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1175
+ FreeBSD 10.3-RELEASE released
https://www.freebsd.org/releases/10.3R/relnotes.html
+ JVNDB-2016-000039 AQUOSフォトプレーヤー HN-PP150 におけるクロスサイトリクエストフォージェリの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000039.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1175
+ Squid HTTP Response Processing Bug Lets Remote Users Cause Denial of Service Conditions
http://www.securitytracker.com/id/1035458
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3948
+ Squid Bug in ICMPv6 Pinger Lets Remote Users Deny Service and Local Users Obtain Potentially Sensitive Heap Memory Contents
http://www.securitytracker.com/id/1035457
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3947
+ PHP 5.5.33 Invalid Memory Write
https://cxsecurity.com/issue/WLB-2016040010
+ PHP <= 7.0.4/5.5.33 - SNMP Format String Exploit
https://cxsecurity.com/issue/WLB-2016040017
JVNDB-2016-000037 WisePoint におけるクリックジャッキングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000037.html
JVNDB-2016-000038 EVAアニメータ用 ActiveX コントロールにおけるバッファオーバーフローの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000038.html
News & Trend
攻めを学ばせ守りに生かす、会津で進むセキュリティ人材育成
http://itpro.nikkeibp.co.jp/atcl/column/14/346926/040300498/?ST=security
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160226-vds-is
+ UPDATE: Cisco Unified Communications Domain Manager Cross-Site Scripting Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160328-ucdm
+ SA69837 Squid Two Vulnerabilities
https://secunia.com/advisories/69837/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3947
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3948
+ SA69852 Sharp AQUOS PhotoPlayer HN-PP150 Cross-Site Request Forgery Vulnerability
https://secunia.com/advisories/69852/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1175
+ FreeBSD 10.3-RELEASE released
https://www.freebsd.org/releases/10.3R/relnotes.html
+ JVNDB-2016-000039 AQUOSフォトプレーヤー HN-PP150 におけるクロスサイトリクエストフォージェリの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000039.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1175
+ Squid HTTP Response Processing Bug Lets Remote Users Cause Denial of Service Conditions
http://www.securitytracker.com/id/1035458
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3948
+ Squid Bug in ICMPv6 Pinger Lets Remote Users Deny Service and Local Users Obtain Potentially Sensitive Heap Memory Contents
http://www.securitytracker.com/id/1035457
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3947
+ PHP 5.5.33 Invalid Memory Write
https://cxsecurity.com/issue/WLB-2016040010
+ PHP <= 7.0.4/5.5.33 - SNMP Format String Exploit
https://cxsecurity.com/issue/WLB-2016040017
JVNDB-2016-000037 WisePoint におけるクリックジャッキングの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000037.html
JVNDB-2016-000038 EVAアニメータ用 ActiveX コントロールにおけるバッファオーバーフローの脆弱性
http://jvndb.jvn.jp/ja/contents/2016/JVNDB-2016-000038.html
News & Trend
攻めを学ばせ守りに生かす、会津で進むセキュリティ人材育成
http://itpro.nikkeibp.co.jp/atcl/column/14/346926/040300498/?ST=security
2016年4月4日月曜日
4日 月曜日、仏滅
+ CESA-2016:0534 Moderate CentOS 7 mariadb Security Update
http://lwn.net/Alerts/682142/
+ CESA-2016:0532 Moderate CentOS 7 krb5 Security Update
http://lwn.net/Alerts/682141/
+ squid 3.5.16 released
http://www.squid-cache.org/Versions/v3/3.5/squid-3.5.16-RELEASENOTES.html
+ UPDATE: Multiple Vulnerabilities in OpenSSL Affecting Cisco Products: March 2016
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160302-openssl
+ Linux kernel 3.2.79 released
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.2.79
+ PostgreSQL Two Vulnerabilities
https://secunia.com/advisories/69848/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2193
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3065
+ Linux Kernel ext4 Race Condition Lets Local Users Corrupt the Target Filesystem
http://www.securitytracker.com/id/1035455
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8839
+ Wireshark dissect_pktc_rekey Heap-based Out-of-Bounds Read
https://cxsecurity.com/issue/WLB-2016040014
+ PHP 5.5.33 Invalid Memory Write
https://cxsecurity.com/issue/WLB-2016040010
+ TrendMicro SSO Redirect / Session Theft
https://cxsecurity.com/issue/WLB-2016040007
チェックしておきたい脆弱性情報<2016.04.04>
http://itpro.nikkeibp.co.jp/atcl/column/14/268561/033100107/?ST=security
LANDesk、クライアント管理ソフト新版でMDM機能を追加
http://itpro.nikkeibp.co.jp/atcl/news/16/040100967/?ST=security
http://lwn.net/Alerts/682142/
+ CESA-2016:0532 Moderate CentOS 7 krb5 Security Update
http://lwn.net/Alerts/682141/
+ squid 3.5.16 released
http://www.squid-cache.org/Versions/v3/3.5/squid-3.5.16-RELEASENOTES.html
+ UPDATE: Multiple Vulnerabilities in OpenSSL Affecting Cisco Products: March 2016
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160302-openssl
+ Linux kernel 3.2.79 released
https://cdn.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.2.79
+ PostgreSQL Two Vulnerabilities
https://secunia.com/advisories/69848/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2193
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3065
+ Linux Kernel ext4 Race Condition Lets Local Users Corrupt the Target Filesystem
http://www.securitytracker.com/id/1035455
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8839
+ Wireshark dissect_pktc_rekey Heap-based Out-of-Bounds Read
https://cxsecurity.com/issue/WLB-2016040014
+ PHP 5.5.33 Invalid Memory Write
https://cxsecurity.com/issue/WLB-2016040010
+ TrendMicro SSO Redirect / Session Theft
https://cxsecurity.com/issue/WLB-2016040007
チェックしておきたい脆弱性情報<2016.04.04>
http://itpro.nikkeibp.co.jp/atcl/column/14/268561/033100107/?ST=security
LANDesk、クライアント管理ソフト新版でMDM機能を追加
http://itpro.nikkeibp.co.jp/atcl/news/16/040100967/?ST=security
2016年4月1日金曜日
1日 金曜日、先勝
+ RHSA-2016:0561 Low: Red Hat Enterprise Linux 5 One-Year Retirement Notice
https://rhn.redhat.com/errata/RHSA-2016-0561.html
+ RHSA-2016:0534 Moderate: mariadb security and bug fix update
https://rhn.redhat.com/errata/RHSA-2016-0534.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4792
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4802
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4815
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4816
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4819
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4826
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4830
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4836
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4858
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4861
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4870
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4879
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4913
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0505
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0546
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0596
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0597
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0598
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0600
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0606
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0608
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0609
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0616
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2047
+ RHSA-2016:0532 Moderate: krb5 security update
https://rhn.redhat.com/errata/RHSA-2016-0532.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8629
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8630
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8631
+ About the security content of iBooks Author 2.4.1
https://support.apple.com/ja-jp/HT206224
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1789
+ UPDATE: Cisco Unified Communications Domain Manager Cross-Site Scripting Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160328-ucdm
+ Citrix XenServer Security Update for CVE-2016-0800
http://support.citrix.com/article/CTX208403
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0800
+ HS16-011 Multiple Vulnerabilities in Cosminexus XML Processor
http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS16-011/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4803
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0466
+ HS16-011 Cosminexus XML Processorにおける複数の脆弱性
http://www.hitachi.co.jp/Prod/comp/soft1/security/info/vuls/HS16-011/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4803
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0466
+ PHP 7.0.5, 5.6.20, 5.5.34 Released
http://www.php.net/ChangeLog-7.php#7.0.5
http://www.php.net/ChangeLog-5.php#5.6.20
http://www.php.net/ChangeLog-5.php#5.5.34
+ 2016-03-31 Security Update Release
http://www.postgresql.org/about/news/1656/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2193
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3065
+ PostgreSQL 9.5.2, 9.4.7, 9.3.12, 9.2.16 and 9.1.21 Released!
http://www.postgresql.org/docs/9.5/static/release-9-5-2.html
http://www.postgresql.org/docs/9.4/static/release-9-4-7.html
http://www.postgresql.org/docs/9.3/static/release-9-3-12.html
http://www.postgresql.org/docs/9.2/static/release-9-2-16.html
http://www.postgresql.org/docs/9.1/static/release-9-1-21.html
+ LibTIFF Buffer Overflow in gif2tiff Lets Remote Users Deny Service
http://www.securitytracker.com/id/1035442
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3186
+ Linux Kernel ims_pcu_parse_cdc_data() Device Driver Flaw Lets Local Users Cause Denial of Service Conditions on the Target System
http://www.securitytracker.com/id/1035441
記者の眼
分かりにくいよセキュリティ用語、ばらまき型で標的型って何?
http://itpro.nikkeibp.co.jp/atcl/watcher/14/334361/032500517/?ST=security
サイバー犯罪にどう立ち向かうか~JC3イベントレポート
「サイバー犯罪者は楽に成功している、被害公表を褒めて被害共有で手口封じる」、パネル討議
http://itpro.nikkeibp.co.jp/atcl/column/16/032400067/032500006/?ST=security
米当局のデバイスロック解除命令、AppleだけでなくGoogleも受けていた
http://itpro.nikkeibp.co.jp/atcl/news/16/033100939/?ST=security
JVNVU#91828421 Eaglesoft (Patterson Dental) でパスワードがハードコードされている問題
http://jvn.jp/vu/JVNVU91828421/
https://rhn.redhat.com/errata/RHSA-2016-0561.html
+ RHSA-2016:0534 Moderate: mariadb security and bug fix update
https://rhn.redhat.com/errata/RHSA-2016-0534.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4792
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4802
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4815
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4816
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4819
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4826
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4830
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4836
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4858
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4861
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4870
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4879
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4913
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0505
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0546
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0596
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0597
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0598
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0600
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0606
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0608
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0609
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0616
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2047
+ RHSA-2016:0532 Moderate: krb5 security update
https://rhn.redhat.com/errata/RHSA-2016-0532.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8629
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8630
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-8631
+ About the security content of iBooks Author 2.4.1
https://support.apple.com/ja-jp/HT206224
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1789
+ UPDATE: Cisco Unified Communications Domain Manager Cross-Site Scripting Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160328-ucdm
+ Citrix XenServer Security Update for CVE-2016-0800
http://support.citrix.com/article/CTX208403
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0800
+ HS16-011 Multiple Vulnerabilities in Cosminexus XML Processor
http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS16-011/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4803
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0466
+ HS16-011 Cosminexus XML Processorにおける複数の脆弱性
http://www.hitachi.co.jp/Prod/comp/soft1/security/info/vuls/HS16-011/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4803
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0466
+ PHP 7.0.5, 5.6.20, 5.5.34 Released
http://www.php.net/ChangeLog-7.php#7.0.5
http://www.php.net/ChangeLog-5.php#5.6.20
http://www.php.net/ChangeLog-5.php#5.5.34
+ 2016-03-31 Security Update Release
http://www.postgresql.org/about/news/1656/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-2193
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3065
+ PostgreSQL 9.5.2, 9.4.7, 9.3.12, 9.2.16 and 9.1.21 Released!
http://www.postgresql.org/docs/9.5/static/release-9-5-2.html
http://www.postgresql.org/docs/9.4/static/release-9-4-7.html
http://www.postgresql.org/docs/9.3/static/release-9-3-12.html
http://www.postgresql.org/docs/9.2/static/release-9-2-16.html
http://www.postgresql.org/docs/9.1/static/release-9-1-21.html
+ LibTIFF Buffer Overflow in gif2tiff Lets Remote Users Deny Service
http://www.securitytracker.com/id/1035442
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3186
+ Linux Kernel ims_pcu_parse_cdc_data() Device Driver Flaw Lets Local Users Cause Denial of Service Conditions on the Target System
http://www.securitytracker.com/id/1035441
記者の眼
分かりにくいよセキュリティ用語、ばらまき型で標的型って何?
http://itpro.nikkeibp.co.jp/atcl/watcher/14/334361/032500517/?ST=security
サイバー犯罪にどう立ち向かうか~JC3イベントレポート
「サイバー犯罪者は楽に成功している、被害公表を褒めて被害共有で手口封じる」、パネル討議
http://itpro.nikkeibp.co.jp/atcl/column/16/032400067/032500006/?ST=security
米当局のデバイスロック解除命令、AppleだけでなくGoogleも受けていた
http://itpro.nikkeibp.co.jp/atcl/news/16/033100939/?ST=security
JVNVU#91828421 Eaglesoft (Patterson Dental) でパスワードがハードコードされている問題
http://jvn.jp/vu/JVNVU91828421/
登録:
投稿 (Atom)