+ Apache OpenOffice 4.1.0 released
https://cwiki.apache.org/confluence/display/OOOUSERS/AOO+4.1+Release+Notes
+ RHSA-2014:0449 Important: thunderbird security update
https://rhn.redhat.com/errata/RHSA-2014-0449.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1518
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1523
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1524
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1529
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1530
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1531
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1532
+ RHSA-2014:0448 Critical: firefox security update
https://rhn.redhat.com/errata/RHSA-2014-0448.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1518
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1523
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1524
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1529
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1530
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1531
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1532
+ MFSA 2014-47 Debugger can bypass XrayWrappers with JavaScript
http://www.mozilla.org/security/announce/2014/mfsa2014-47.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1526
+ MFSA 2014-46 Use-after-free in nsHostResolve
http://www.mozilla.org/security/announce/2014/mfsa2014-46.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1532
+ MFSA 2014-45 Incorrect IDNA domain name matching for wildcard certificates
http://www.mozilla.org/security/announce/2014/mfsa2014-45.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1492
+ MFSA 2014-44 Use-after-free in imgLoader while resizing images
http://www.mozilla.org/security/announce/2014/mfsa2014-44.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1531
+ MFSA 2014-43 Cross-site scripting (XSS) using history navigations
http://www.mozilla.org/security/announce/2014/mfsa2014-43.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1530
+ MFSA 2014-42 Privilege escalation through Web Notification API
http://www.mozilla.org/security/announce/2014/mfsa2014-42.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1529
+ MFSA 2014-41 Out-of-bounds write in Cairo
http://www.mozilla.org/security/announce/2014/mfsa2014-41.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1528
+ MFSA 2014-40 Firefox for Android addressbar suppression
http://www.mozilla.org/security/announce/2014/mfsa2014-40.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1527
+ MFSA 2014-39 Use-after-free in the Text Track Manager for HTML video
http://www.mozilla.org/security/announce/2014/mfsa2014-39.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1525
+ MFSA 2014-38 Buffer overflow when using non-XBL object as XBL
http://www.mozilla.org/security/announce/2014/mfsa2014-38.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1524
+ MFSA 2014-37 Out of bounds read while decoding JPG images
http://www.mozilla.org/security/announce/2014/mfsa2014-37.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1523
+ MFSA 2014-36 Web Audio memory corruption issues
http://www.mozilla.org/security/announce/2014/mfsa2014-36.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1522
+ MFSA 2014-35 Privilege escalation through Mozilla Maintenance Service Installer
http://www.mozilla.org/security/announce/2014/mfsa2014-35.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1520
+ MFSA 2014-34 Miscellaneous memory safety hazards (rv:29.0 / rv:24.5)
http://www.mozilla.org/security/announce/2014/mfsa2014-34.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1519
+ APSB14-13 Security updates available for Adobe Flash Player
http://helpx.adobe.com/security/products/flash-player/apsb14-13.html
+ Mozilla Firefox 29.0 released
http://www.mozilla.org/en-US/firefox/29.0/releasenotes/
+ Mozilla Thunderbird 24.5.0 released
http://www.mozilla.org/en-US/thunderbird/24.5.0/releasenotes/
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ UPDATE: HPSBMU03020 rev.2 - HP Version Control Agent (VCA) and Version Control Repository Manager (VCRM) running OpenSSL on Linux and Windows, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04262472-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ Citrix Security Advisory for CVE-2014-0160, aka the Heartbleed vulnerability
http://support.citrix.com/article/CTX140605
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ Citrix NetScaler Application Delivery Controller and NetScaler Gateway Multiple Security Updates
http://support.citrix.com/article/CTX140651
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2881
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2882
+ UPDATE: Oracle Critical Patch Update Advisory - April 2014
http://www.oracle.com/technetwork/topics/security/cpuapr2014-1972952.html
+ Apache Struts Flaw Lets Remote Users Manipulate the ClassLoader to Execute Arbitrary Code
http://www.securitytracker.com/id/1030159
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0114
+ Adobe Flash Player Buffer Overflow Lets Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1030155
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0515
+ REMOTE: Adobe Flash Player Type Confusion Remote Code Execution
http://www.exploit-db.com/exploits/33095
+ REMOTE: McAfee ePolicy Orchestrator 4.6.0-4.6.5 (ePowner) - Multiple Vulnerabilities
http://www.exploit-db.com/exploits/33071
+ LOCAL: Wireshark <= 1.8.12/1.10.5 wiretap/mpeg.c Stack Buffer Overflow
http://www.exploit-db.com/exploits/33069
+ DoS/PoC: NTP ntpd monlist Query Reflection - Denial of Service
http://www.exploit-db.com/exploits/33073
+ Wireshark <= 1.8.12/1.10.5 wiretap/mpeg.c Stack Buffer Overflow
http://cxsecurity.com/issue/WLB-2014040194
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2299
+ ntp monlist DDoS issue Exploit
http://cxsecurity.com/issue/WLB-2014040193
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5211
+ Adobe Flash Player Type Confusion Remote Code Execution Exploit
http://cxsecurity.com/issue/WLB-2014040192
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5331
+ SA58220 Microsoft Windows Flash Player Buffer Overflow Vulnerability
http://secunia.com/advisories/58220/
+ SA58085 Adobe Flash Player Buffer Overflow Vulnerability
http://secunia.com/advisories/58085/
+ 2014年4月 Microsoft Internet Explorer の未修正の脆弱性に関する注意喚起
http://www.jpcert.or.jp/at/2014/at140018.html
+ Apache Struts ClassLoader Manipulation CVE-2014-0114 Security Bypass Vulnerability
http://www.securityfocus.com/bid/67121
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0114
警察庁、「Struts 2」の脆弱性を狙ったアクセスを検知
http://itpro.nikkeibp.co.jp/article/NEWS/20140428/553742/?ST=security
IE 6~11に深刻なゼロデイ脆弱性、米FireEyeが標的型攻撃への悪用を観測
http://itpro.nikkeibp.co.jp/article/NEWS/20140428/553585/?ST=security
UPDATE: JVNVU#94401838 OpenSSL の heartbeat 拡張に情報漏えいの脆弱性
http://jvn.jp/vu/JVNVU94401838/index.html
JVNVU#92280347 Internet Explorer に解放済みメモリ使用 (use-after-free) の脆弱性
http://jvn.jp/vu/JVNVU92280347/index.html
JVN#19294237 Apache Struts において ClassLoader が操作可能な脆弱性
http://jvn.jp/jp/JVN19294237/index.html
VU#489228 Ignite Realtime Smack XMPP API contains multiple vulnerabilities
http://www.kb.cert.org/vuls/id/489228
2014年4月30日水曜日
2014年4月28日月曜日
28日 月曜日、先勝
+ MantisTouch 1.3.2 released
http://www.mantisbt.org/blog/?p=293
+ CESA-2014:0433 Moderate CentOS 5 kernel Update
http://lwn.net/Alerts/596215/
+ PDFCreator 1.7.3 released
http://www.pdfforge.org/blog/pdf-architect-20-and-pdfcreator-173-released
+ phpMyAdmin 4.1.14 released
http://sourceforge.net/p/phpmyadmin/news/2014/04/phpmyadmin-4114-has-been-released/
+ UPDATE: HPSBGN03010 rev.2 - HP Software Server Automation running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04250814-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HPSBMU03025 rev.1 - HP Diagnostics running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04267775-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBMU03023 rev.1 - HP BladeSystem c-Class Virtual Connect Support Utility (VCSU) running OpenSSL on Linux and Windows, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04264271-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBMU03022 rev.1 - HP Systems Insight Manager (SIM) Bundled Software running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04263236-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ UPDATE: HPSBMU03017 rev.2 - HP Software Connect-IT running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04260456-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ Linux kernel 3.14.2, 3.10.38, 3.4.88 released
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.14.2
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.10.38
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.4.88
+ Struts 2.3.16.2 released
http://struts.apache.org/release/2.3.x/docs/version-notes-23162.html
+ Microsoft Internet Explorer Object Access Flaw Lets Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1030154
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1776
+ VU#222929 Microsoft Internet Explorer use-after-free vulnerability
http://www.kb.cert.org/vuls/id/222929
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1776
+ VU#719225 Apache Struts2 ClassLoader allows access to class properties via request parameters
http://www.kb.cert.org/vuls/id/719225
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0094
+ DoS/PoC: Symantec Endpoint Protection Manager 12.1.x - SEH Overflow POC
http://www.exploit-db.com/exploits/33056
+ Ubuntu 14.04 security problem in the lock screen
http://cxsecurity.com/issue/WLB-2014040176
+ Symantec Endpoint Protection Manager 12.1.x - SEH Overflow POC
http://cxsecurity.com/issue/WLB-2014040178
+ Mac OS X 10.7 Lion x64 NFS Mount Privilege Escalation
http://cxsecurity.com/issue/WLB-2014040174
+ SA57908 Microsoft Internet Explorer Use-After-Free Vulnerability
http://secunia.com/advisories/57908/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1776
JVNDB-2014-000045 Apache Struts において ClassLoader が操作可能な脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000045.html
国税庁がStruts脆弱性で確定申告書作成サービス停止、「再開までは手書きで」
http://itpro.nikkeibp.co.jp/article/NEWS/20140425/553462/?ST=security
「Strutsの脆弱性を突く攻撃を検知、早急な対策を」、ラック西本専務
http://itpro.nikkeibp.co.jp/article/NEWS/20140425/553442/?ST=security
Google、MS、Facebookなど大手IT企業、Heartbleed再発防止を支援
http://itpro.nikkeibp.co.jp/article/NEWS/20140425/553266/?ST=security
JVNVU#94401838 OpenSSL の heartbeat 拡張に情報漏えいの脆弱性
http://jvn.jp/vu/JVNVU94401838/
JVNVU#90945962 POCO C++ Libraries の NetSSL ライブラリにおけるワイルドカード証明書を適切に検証しない脆弱性
http://jvn.jp/vu/JVNVU90945962/
JVN#19294237 Apache Struts において ClassLoader が操作可能な脆弱性
http://jvn.jp/jp/JVN19294237/
REMOTE: Kolibri 2.0 GET Request - Stack Buffer Overflow
http://www.exploit-db.com/exploits/33027
LOCAL: JRuby Sandbox 0.2.2 - Sandbox Escape
http://www.exploit-db.com/exploits/33028
PoC/DoS: cFos Personal Net 3.09 - Remote Heap Memory Corruption Denial of Service
http://www.exploit-db.com/exploits/33018
http://www.mantisbt.org/blog/?p=293
+ CESA-2014:0433 Moderate CentOS 5 kernel Update
http://lwn.net/Alerts/596215/
+ PDFCreator 1.7.3 released
http://www.pdfforge.org/blog/pdf-architect-20-and-pdfcreator-173-released
+ phpMyAdmin 4.1.14 released
http://sourceforge.net/p/phpmyadmin/news/2014/04/phpmyadmin-4114-has-been-released/
+ UPDATE: HPSBGN03010 rev.2 - HP Software Server Automation running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04250814-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HPSBMU03025 rev.1 - HP Diagnostics running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04267775-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBMU03023 rev.1 - HP BladeSystem c-Class Virtual Connect Support Utility (VCSU) running OpenSSL on Linux and Windows, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04264271-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBMU03022 rev.1 - HP Systems Insight Manager (SIM) Bundled Software running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04263236-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ UPDATE: HPSBMU03017 rev.2 - HP Software Connect-IT running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04260456-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ Linux kernel 3.14.2, 3.10.38, 3.4.88 released
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.14.2
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.10.38
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.4.88
+ Struts 2.3.16.2 released
http://struts.apache.org/release/2.3.x/docs/version-notes-23162.html
+ Microsoft Internet Explorer Object Access Flaw Lets Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1030154
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1776
+ VU#222929 Microsoft Internet Explorer use-after-free vulnerability
http://www.kb.cert.org/vuls/id/222929
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1776
+ VU#719225 Apache Struts2 ClassLoader allows access to class properties via request parameters
http://www.kb.cert.org/vuls/id/719225
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0094
+ DoS/PoC: Symantec Endpoint Protection Manager 12.1.x - SEH Overflow POC
http://www.exploit-db.com/exploits/33056
+ Ubuntu 14.04 security problem in the lock screen
http://cxsecurity.com/issue/WLB-2014040176
+ Symantec Endpoint Protection Manager 12.1.x - SEH Overflow POC
http://cxsecurity.com/issue/WLB-2014040178
+ Mac OS X 10.7 Lion x64 NFS Mount Privilege Escalation
http://cxsecurity.com/issue/WLB-2014040174
+ SA57908 Microsoft Internet Explorer Use-After-Free Vulnerability
http://secunia.com/advisories/57908/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1776
JVNDB-2014-000045 Apache Struts において ClassLoader が操作可能な脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000045.html
国税庁がStruts脆弱性で確定申告書作成サービス停止、「再開までは手書きで」
http://itpro.nikkeibp.co.jp/article/NEWS/20140425/553462/?ST=security
「Strutsの脆弱性を突く攻撃を検知、早急な対策を」、ラック西本専務
http://itpro.nikkeibp.co.jp/article/NEWS/20140425/553442/?ST=security
Google、MS、Facebookなど大手IT企業、Heartbleed再発防止を支援
http://itpro.nikkeibp.co.jp/article/NEWS/20140425/553266/?ST=security
JVNVU#94401838 OpenSSL の heartbeat 拡張に情報漏えいの脆弱性
http://jvn.jp/vu/JVNVU94401838/
JVNVU#90945962 POCO C++ Libraries の NetSSL ライブラリにおけるワイルドカード証明書を適切に検証しない脆弱性
http://jvn.jp/vu/JVNVU90945962/
JVN#19294237 Apache Struts において ClassLoader が操作可能な脆弱性
http://jvn.jp/jp/JVN19294237/
REMOTE: Kolibri 2.0 GET Request - Stack Buffer Overflow
http://www.exploit-db.com/exploits/33027
LOCAL: JRuby Sandbox 0.2.2 - Sandbox Escape
http://www.exploit-db.com/exploits/33028
PoC/DoS: cFos Personal Net 3.09 - Remote Heap Memory Corruption Denial of Service
http://www.exploit-db.com/exploits/33018
2014年4月25日金曜日
25日 金曜日、仏滅
+ RHSA-2014:0429 Moderate: tomcat6 security update
http://rhn.redhat.com/errata/RHSA-2014-0429.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4286
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4322
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0050
+ Google Chrome 34.0.1847.131 released
http://googlechromereleases.blogspot.jp/2014/04/stable-channel-update_24.html
+ CESA-2014:0429 Moderate CentOS 6 tomcat6 Update
http://lwn.net/Alerts/595970/
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ HPSBHF03021 rev.1 - HP Thin Client with ThinPro OS or Smart Zero Core Services, Running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04262670-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBHF03006 rev.1 - HP Integrated Lights-Out 2 (iLO 2) Denial of Service
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04244787-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2601
+ HPSBMU03020 rev.1 - HP Version Control Agent (VCA) and Version Control Repository Manager (VCRM) running OpenSSL on Linux and Windows, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04262472-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBPI03014 rev.1 - HP LaserJet Pro MFP Printers, HP Color LaserJet Pro MFP Printers, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04262495-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBST03016 rev.1 - HP P2000 G3 MSA Array Systems, HP MSA 2040 Storage, and HP MSA 1040 Storage Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04263038-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ Linux kernel 3.12.18 released
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.12.18
+ RHSA-2014:0433 Moderate: kernel security, bug fix, and enhancement update
http://rhn.redhat.com/errata/RHSA-2014-0433.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-6638
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2888
+ Apache Struts Bug Lets Remote Users Manipulate the ClassLoader to Execute Arbitrary Code
http://www.securitytracker.com/id/1030152
+ REMOTE: Heartbleed OpenSSL - Information Leak Exploit (2) - DTLS Support
http://www.exploit-db.com/exploits/32998
+ OpenSSL DTLS Support Information Leak Exploit 2
http://cxsecurity.com/issue/WLB-2014040161
ウイルスバスター コーポレートエディション 10.6 Service Pack 3 Patch1 Critical patch (ビルド 5495) 公開のお知らせ
http://app.trendmicro.co.jp/support/news.asp?id=2115
ソフトウェア等の脆弱性関連情報に関する届出状況[2014年第1四半期(1月~3月)]
http://www.ipa.go.jp/security/vuln/report/vuln2014q1.html
Apache Struts最新版に脆弱性対策の漏れ、IPAがWAFやIPSでの対策呼びかけ
http://itpro.nikkeibp.co.jp/article/NEWS/20140424/553126/?ST=security
VU#118748 POCO C++ Libraries NetSSL library fails to properly validate wildcard certificates
http://www.kb.cert.org/vuls/id/118748
REMOTE: Acunetix 8 build 20120704 - Remote Stack Based Overflow
http://www.exploit-db.com/exploits/32997
http://rhn.redhat.com/errata/RHSA-2014-0429.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4286
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4322
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0050
+ Google Chrome 34.0.1847.131 released
http://googlechromereleases.blogspot.jp/2014/04/stable-channel-update_24.html
+ CESA-2014:0429 Moderate CentOS 6 tomcat6 Update
http://lwn.net/Alerts/595970/
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ HPSBHF03021 rev.1 - HP Thin Client with ThinPro OS or Smart Zero Core Services, Running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04262670-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBHF03006 rev.1 - HP Integrated Lights-Out 2 (iLO 2) Denial of Service
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04244787-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2601
+ HPSBMU03020 rev.1 - HP Version Control Agent (VCA) and Version Control Repository Manager (VCRM) running OpenSSL on Linux and Windows, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04262472-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBPI03014 rev.1 - HP LaserJet Pro MFP Printers, HP Color LaserJet Pro MFP Printers, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04262495-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBST03016 rev.1 - HP P2000 G3 MSA Array Systems, HP MSA 2040 Storage, and HP MSA 1040 Storage Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04263038-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ Linux kernel 3.12.18 released
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.12.18
+ RHSA-2014:0433 Moderate: kernel security, bug fix, and enhancement update
http://rhn.redhat.com/errata/RHSA-2014-0433.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-6638
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2888
+ Apache Struts Bug Lets Remote Users Manipulate the ClassLoader to Execute Arbitrary Code
http://www.securitytracker.com/id/1030152
+ REMOTE: Heartbleed OpenSSL - Information Leak Exploit (2) - DTLS Support
http://www.exploit-db.com/exploits/32998
+ OpenSSL DTLS Support Information Leak Exploit 2
http://cxsecurity.com/issue/WLB-2014040161
ウイルスバスター コーポレートエディション 10.6 Service Pack 3 Patch1 Critical patch (ビルド 5495) 公開のお知らせ
http://app.trendmicro.co.jp/support/news.asp?id=2115
ソフトウェア等の脆弱性関連情報に関する届出状況[2014年第1四半期(1月~3月)]
http://www.ipa.go.jp/security/vuln/report/vuln2014q1.html
Apache Struts最新版に脆弱性対策の漏れ、IPAがWAFやIPSでの対策呼びかけ
http://itpro.nikkeibp.co.jp/article/NEWS/20140424/553126/?ST=security
VU#118748 POCO C++ Libraries NetSSL library fails to properly validate wildcard certificates
http://www.kb.cert.org/vuls/id/118748
REMOTE: Acunetix 8 build 20120704 - Remote Stack Based Overflow
http://www.exploit-db.com/exploits/32997
2014年4月24日木曜日
24日 木曜日、先負
+ RHSA-2014:0429 Moderate: tomcat6 security update
http://rhn.redhat.com/errata/RHSA-2014-0429.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4286
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4322
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0050
+ CESA-2014:0420 Moderate CentOS 6 qemu-kvm Update
http://lwn.net/Alerts/595767/
+ Squid 3.4.4.2 released
http://www.squid-cache.org/Versions/v3/3.4/RELEASENOTES.html
+ AirPort Base Station Firmware Update 7.7.3
http://support.apple.com/kb/HT6203
+ About the security content of Apple TV 6.1.1
http://support.apple.com/kb/HT6209
+ About the security content of iOS 7.1.1
http://support.apple.com/kb/HT6208
+ Security Update 2014-002
http://support.apple.com/kb/HT6207
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ UPDATE: Undocumented Test Interface in Cisco Small Business Devices
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140110-sbd
+ HPSBGN03011 rev.1 - HP IceWall MCRP running OpenSSL on Red Hat Enterprise Linux 6 (RHEL6), Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04259321-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ UPDATE: HPSBMU02997 rev.2 - HP Smart Update Manager (SUM) running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04239375-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ UPDATE: HPSBMU02995 rev.5 - HP Software HP Service Manager, Asset Manager, UCMDB Browser, UCMDB Configuration Manager, Executive Scorecard, Server Automation, Diagnostics, LoadRunner, and Performance Center, running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04236102-5%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HPSBMU02895 SSRT101253 rev.1 - HP データプロテクタ、権限のリモート強化、サービス拒否 (DoS)、任意コードの実行
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04083772-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2344
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2345
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2346
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2347
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2348
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2349
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2350
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6194
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6195
+ UPDATE: HPSBST03015 rev.2 - HP 3PAR OS running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04261644-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ Linux kernel 3.13.11 released
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.13.11
+ SYM14-007 Security Advisories Relating to Symantec Products - Symantec Encryption Desktop Memory Access Violations
http://www.symantec.com/security_response/securityupdates/detail.jsp?fid=security_advisory&pvid=security_advisory&year=&suid=20140423_00
+ Symantec Messaging Gateway Input Validation Flaw in 'displayTab' Parameter Permits Cross-Site Scripting Attacks
http://www.securitytracker.com/id/1030136
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1648
+ Apple OS X Multiple Bugs Let Remote Users Execute Arbitrary Code and Deny Service and Local Users Gain Elevated Privileges
http://www.securitytracker.com/id/1030133
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5170
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1295
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1296
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1314
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1315
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1316
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1318
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1319
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1320
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1321
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1322
+ AirPort Extreme and AirPort Time Capsule OpenSSL TLS Heartbeat Buffer Overread Lets Remote Users Obtain Potentially Sensitive Information
http://www.securitytracker.com/id/1030132
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ SA58217 Wireshark RTP Dissector Denial of Service Vulnerability
http://secunia.com/advisories/58217/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2907
+ Symantec Messaging Gateway 10.5.1 Cross Site Scripting
http://cxsecurity.com/issue/WLB-2014040148
+ Symantec Encryption Desktop Memory Block Data Read Access Violation Denial of Service Vulnerability
http://www.securityfocus.com/bid/67020
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1647
+ Symantec Encryption Desktop Memory Copy Read Access Violation Denial of Service Vulnerability
http://www.securityfocus.com/bid/67016
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1646
脆弱性対策情報データベースJVN iPediaの登録状況 [2014年第1四半期(1月~3月)]
http://www.ipa.go.jp/security/vuln/report/JVNiPedia2014q1.html
パナソニックの会員サイトで情報漏洩のおそれ、不正ログイン試行460万件超
http://itpro.nikkeibp.co.jp/article/NEWS/20140423/552845/?ST=security
ワコール、不正アクセス受け閉鎖中だったWebサイトを一部再開
http://itpro.nikkeibp.co.jp/article/NEWS/20140423/552827/?ST=security
JVNVU#95860341 複数の Apple 製品の脆弱性に対するアップデート
http://jvn.jp/vu/JVNVU95860341/
JVNVU#98935174 IBM Notes および IBM Domino に問題
http://jvn.jp/vu/JVNVU98935174/
http://rhn.redhat.com/errata/RHSA-2014-0429.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4286
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4322
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0050
+ CESA-2014:0420 Moderate CentOS 6 qemu-kvm Update
http://lwn.net/Alerts/595767/
+ Squid 3.4.4.2 released
http://www.squid-cache.org/Versions/v3/3.4/RELEASENOTES.html
+ AirPort Base Station Firmware Update 7.7.3
http://support.apple.com/kb/HT6203
+ About the security content of Apple TV 6.1.1
http://support.apple.com/kb/HT6209
+ About the security content of iOS 7.1.1
http://support.apple.com/kb/HT6208
+ Security Update 2014-002
http://support.apple.com/kb/HT6207
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ UPDATE: Undocumented Test Interface in Cisco Small Business Devices
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140110-sbd
+ HPSBGN03011 rev.1 - HP IceWall MCRP running OpenSSL on Red Hat Enterprise Linux 6 (RHEL6), Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04259321-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ UPDATE: HPSBMU02997 rev.2 - HP Smart Update Manager (SUM) running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04239375-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ UPDATE: HPSBMU02995 rev.5 - HP Software HP Service Manager, Asset Manager, UCMDB Browser, UCMDB Configuration Manager, Executive Scorecard, Server Automation, Diagnostics, LoadRunner, and Performance Center, running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04236102-5%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HPSBMU02895 SSRT101253 rev.1 - HP データプロテクタ、権限のリモート強化、サービス拒否 (DoS)、任意コードの実行
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04083772-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2344
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2345
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2346
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2347
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2348
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2349
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2350
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6194
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6195
+ UPDATE: HPSBST03015 rev.2 - HP 3PAR OS running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04261644-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ Linux kernel 3.13.11 released
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.13.11
+ SYM14-007 Security Advisories Relating to Symantec Products - Symantec Encryption Desktop Memory Access Violations
http://www.symantec.com/security_response/securityupdates/detail.jsp?fid=security_advisory&pvid=security_advisory&year=&suid=20140423_00
+ Symantec Messaging Gateway Input Validation Flaw in 'displayTab' Parameter Permits Cross-Site Scripting Attacks
http://www.securitytracker.com/id/1030136
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1648
+ Apple OS X Multiple Bugs Let Remote Users Execute Arbitrary Code and Deny Service and Local Users Gain Elevated Privileges
http://www.securitytracker.com/id/1030133
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5170
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1295
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1296
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1314
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1315
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1316
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1318
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1319
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1320
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1321
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1322
+ AirPort Extreme and AirPort Time Capsule OpenSSL TLS Heartbeat Buffer Overread Lets Remote Users Obtain Potentially Sensitive Information
http://www.securitytracker.com/id/1030132
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ SA58217 Wireshark RTP Dissector Denial of Service Vulnerability
http://secunia.com/advisories/58217/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2907
+ Symantec Messaging Gateway 10.5.1 Cross Site Scripting
http://cxsecurity.com/issue/WLB-2014040148
+ Symantec Encryption Desktop Memory Block Data Read Access Violation Denial of Service Vulnerability
http://www.securityfocus.com/bid/67020
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1647
+ Symantec Encryption Desktop Memory Copy Read Access Violation Denial of Service Vulnerability
http://www.securityfocus.com/bid/67016
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1646
脆弱性対策情報データベースJVN iPediaの登録状況 [2014年第1四半期(1月~3月)]
http://www.ipa.go.jp/security/vuln/report/JVNiPedia2014q1.html
パナソニックの会員サイトで情報漏洩のおそれ、不正ログイン試行460万件超
http://itpro.nikkeibp.co.jp/article/NEWS/20140423/552845/?ST=security
ワコール、不正アクセス受け閉鎖中だったWebサイトを一部再開
http://itpro.nikkeibp.co.jp/article/NEWS/20140423/552827/?ST=security
JVNVU#95860341 複数の Apple 製品の脆弱性に対するアップデート
http://jvn.jp/vu/JVNVU95860341/
JVNVU#98935174 IBM Notes および IBM Domino に問題
http://jvn.jp/vu/JVNVU98935174/
2014年4月23日水曜日
23日 水曜日、友引
+ RHSA-2014:0420 Moderate: qemu-kvm security update
http://rhn.redhat.com/errata/RHSA-2014-0420.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0142
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0143
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0144
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0145
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0146
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0147
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0148
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0150
+ Wireshark 1.10.7 released
http://www.wireshark.org/docs/relnotes/wireshark-1.10.7.html
+ HPSBMU03013 rev.1 - WMI Mapper for HP Systems Insight Manager running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04260385-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBST03015 rev.1 - HP 3PAR OS running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04261644-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBST03000 rev.1 - HP StoreEver ESL G3 Tape Library and Enterprise Library LTO-6 Tape Drives running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04260637-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HS14-011 Vulnerability about TLS Protocol in Cosminexus HTTP Server and Hitachi Web Server
http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS14-011/index.html
+ HS14-010 Issues in Cosminexus
http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS14-010/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-1473
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3389
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0625
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0626
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0627
+ HS14-009 Multiple Vulnerabilities in Cosminexus
http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS14-009/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6629
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6954
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0429
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0432
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0446
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0449
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0451
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0452
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0453
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0454
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0455
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0456
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0457
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0458
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0459
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0460
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0461
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1876
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2397
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2398
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2401
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2402
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2403
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2409
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2412
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2413
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2414
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2420
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2421
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2423
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2427
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2428
+ HS14-011 Cosminexus HTTP Server, Hitachi Web ServerにおけるTLSプロトコルの脆弱性
http://www.hitachi.co.jp/Prod/comp/soft1/security/info/vuls/HS14-011/index.html
+ HS14-010 Cosminexusにおける問題
http://www.hitachi.co.jp/Prod/comp/soft1/security/info/vuls/HS14-010/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-1473
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3389
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0625
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0626
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0627
+ HS14-009 Cosminexusにおける複数の脆弱性
http://www.hitachi.co.jp/Prod/comp/soft1/security/info/vuls/HS14-009/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6629
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6954
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0429
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0432
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0446
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0449
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0451
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0452
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0453
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0454
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0455
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0456
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0457
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0458
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0459
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0460
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0461
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1876
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2397
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2398
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2401
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2402
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2403
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2409
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2412
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2413
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2414
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2420
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2421
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2423
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2427
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2428
+ SYM14-006 Security Advisories Relating to Symantec Products - Symantec Messaging Gateway Management Console Reflected XSS
http://www.symantec.com/security_response/securityupdates/detail.jsp?fid=security_advisory&pvid=security_advisory&year=&suid=20140422_00
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1648
+ GCC 4.9.0 released
http://gcc.gnu.org/gcc-4.9/
+ UPDATE: JVNVU#94401838 OpenSSL の heartbeat 拡張に情報漏えいの脆弱性
http://jvn.jp/vu/JVNVU94401838/index.html
+ VU#350089 IBM Notes and Domino on x86 Linux specify an executable stack
http://www.kb.cert.org/vuls/id/350089
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0892
ゴールデンウイーク期間の営業に関するご案内
http://app.trendmicro.co.jp/support/news.asp?id=2117
パソコンに顔を向けるだけでログイン完了、NECが顔認証ソフト
http://itpro.nikkeibp.co.jp/article/NEWS/20140422/552405/?ST=security
JVNVU#93141759 Toshiba 4690 Operating System に脆弱性
http://jvn.jp/vu/JVNVU93141759/
http://rhn.redhat.com/errata/RHSA-2014-0420.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0142
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0143
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0144
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0145
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0146
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0147
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0148
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0150
+ Wireshark 1.10.7 released
http://www.wireshark.org/docs/relnotes/wireshark-1.10.7.html
+ HPSBMU03013 rev.1 - WMI Mapper for HP Systems Insight Manager running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04260385-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBST03015 rev.1 - HP 3PAR OS running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04261644-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBST03000 rev.1 - HP StoreEver ESL G3 Tape Library and Enterprise Library LTO-6 Tape Drives running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04260637-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HS14-011 Vulnerability about TLS Protocol in Cosminexus HTTP Server and Hitachi Web Server
http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS14-011/index.html
+ HS14-010 Issues in Cosminexus
http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS14-010/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-1473
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3389
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0625
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0626
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0627
+ HS14-009 Multiple Vulnerabilities in Cosminexus
http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS14-009/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6629
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6954
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0429
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0432
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0446
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0449
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0451
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0452
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0453
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0454
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0455
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0456
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0457
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0458
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0459
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0460
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0461
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1876
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2397
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2398
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2401
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2402
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2403
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2409
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2412
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2413
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2414
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2420
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2421
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2423
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2427
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2428
+ HS14-011 Cosminexus HTTP Server, Hitachi Web ServerにおけるTLSプロトコルの脆弱性
http://www.hitachi.co.jp/Prod/comp/soft1/security/info/vuls/HS14-011/index.html
+ HS14-010 Cosminexusにおける問題
http://www.hitachi.co.jp/Prod/comp/soft1/security/info/vuls/HS14-010/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-1473
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3389
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0625
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0626
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0627
+ HS14-009 Cosminexusにおける複数の脆弱性
http://www.hitachi.co.jp/Prod/comp/soft1/security/info/vuls/HS14-009/index.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6629
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6954
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0429
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0432
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0446
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0449
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0451
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0452
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0453
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0454
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0455
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0456
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0457
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0458
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0459
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0460
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0461
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1876
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2397
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2398
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2401
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2402
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2403
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2409
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2412
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2413
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2414
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2420
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2421
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2423
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2427
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2428
+ SYM14-006 Security Advisories Relating to Symantec Products - Symantec Messaging Gateway Management Console Reflected XSS
http://www.symantec.com/security_response/securityupdates/detail.jsp?fid=security_advisory&pvid=security_advisory&year=&suid=20140422_00
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1648
+ GCC 4.9.0 released
http://gcc.gnu.org/gcc-4.9/
+ UPDATE: JVNVU#94401838 OpenSSL の heartbeat 拡張に情報漏えいの脆弱性
http://jvn.jp/vu/JVNVU94401838/index.html
+ VU#350089 IBM Notes and Domino on x86 Linux specify an executable stack
http://www.kb.cert.org/vuls/id/350089
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0892
ゴールデンウイーク期間の営業に関するご案内
http://app.trendmicro.co.jp/support/news.asp?id=2117
パソコンに顔を向けるだけでログイン完了、NECが顔認証ソフト
http://itpro.nikkeibp.co.jp/article/NEWS/20140422/552405/?ST=security
JVNVU#93141759 Toshiba 4690 Operating System に脆弱性
http://jvn.jp/vu/JVNVU93141759/
2014年4月22日火曜日
22日 火曜日、先勝
 + HPSBMU03018 rev.1 - HP Software Asset Manager running OpenSSL, Remote Disclosure of Information
+ HPSBMU03018 rev.1 - HP Software Asset Manager running OpenSSL, Remote Disclosure of Informationhttps://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04260505-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
 + HPSBMU03017 rev.1 - HP Software Connect-IT running OpenSSL, Remote Disclosure of Information
+ HPSBMU03017 rev.1 - HP Software Connect-IT running OpenSSL, Remote Disclosure of Informationhttps://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04260456-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
 + HPSBMU03019 rev.1 - HP Software UCMDB Browser and Configuration Manager running OpenSSL, Remote Disclosure of Information
+ HPSBMU03019 rev.1 - HP Software UCMDB Browser and Configuration Manager running OpenSSL, Remote Disclosure of Informationhttp://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
 + Bugzilla Input Validation Flaw Permits Cross-Site Request Forgery Attacks
+ Bugzilla Input Validation Flaw Permits Cross-Site Request Forgery Attackshttp://www.securitytracker.com/id/1030128
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1517
+ REMOTE: Adobe Flash Player Regular Expression Heap Overflow
http://www.exploit-db.com/exploits/32959
 + SA57862 Linux Kernel "ping_init_sock()" Reference Count Denial of Service Vulnerability
+ SA57862 Linux Kernel "ping_init_sock()" Reference Count Denial of Service Vulnerabilityhttp://secunia.com/advisories/57862/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2851
+ SA57911 Oracle Multiple Products OpenSSL Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57911/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
 + Bugzilla CVE-2014-1517 Cross Site Request Forgery Vulnerability
+ Bugzilla CVE-2014-1517 Cross Site Request Forgery Vulnerabilityhttp://www.securityfocus.com/bid/66984
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1517
+ Cybozu Remote Service Manager CVE-2014-1983 Denial of Service Vulnerability
http://www.securityfocus.com/bid/66983
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1983
+ Cybozu Remote Service Manager CVE-2014-1984 Session Fixation Vulnerability
http://www.securityfocus.com/bid/66982
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1984
Advisory: Critical vulnerability found in OpenSSL affecting Sophos products
http://www.sophos.com/en-us/support/knowledgebase/120854.aspx
国内でもOpenSSL「心臓出血」が悪用、三菱UFJニコスから894人の情報流出か
http://itpro.nikkeibp.co.jp/article/NEWS/20140421/551884/?ST=security
オバマケアのWebサイトがパスワードリセット、Heartbleed対策で
http://itpro.nikkeibp.co.jp/article/NEWS/20140421/551822/?ST=security
VU#622950 Toshiba Global Commerce Solutions' 4690 Point of Sale operating system contains a password hashing algorithm that can be reversed
http://www.kb.cert.org/vuls/id/622950
2014年4月21日月曜日
ubuntu 14.04 LTS Install MEMO
ubuntu 14.04 がリリースされたので、インストールしてみた。
1. DVD から起動
2. 「ようこそ」:言語で「日本語」を選択して [Ubuntu をインストール] ボタンを押す。
3. 「Ubuntu のインストール準備」:を確認して [続ける] ボタンを押す。
4. 「インストールの種類」:「ディスクを削除して Ubuntu をインストール」を選択して、
[インストール] ボタンを押す。
5. 「どこに住んでいますか?」:"Tokyo" であることを確認して [続ける] ボタンを押す。
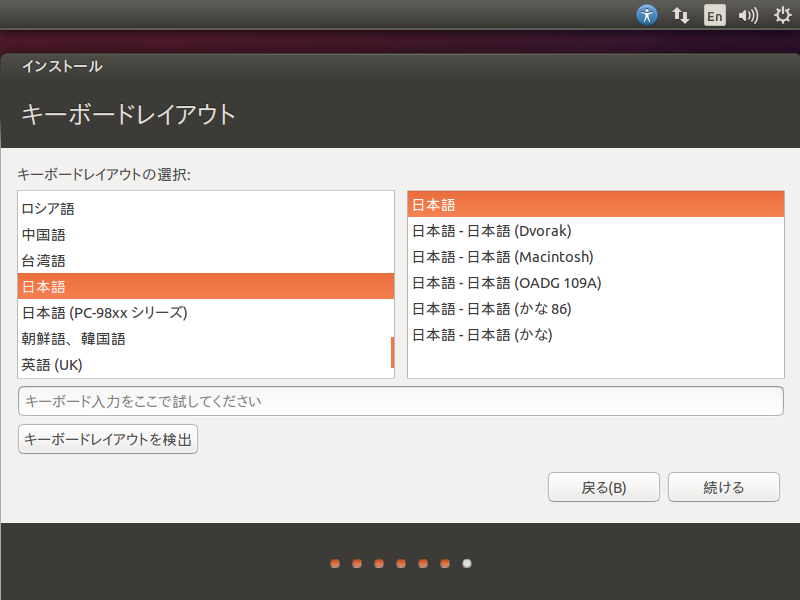
6. 「キーボードレイアウト」:「日本語」、「日本語」であることを確認して [続ける] ボタンを押す。
7. 「あなたの情報を入力してください」:適宜入力項目を設定して [続ける] ボタンを押す。
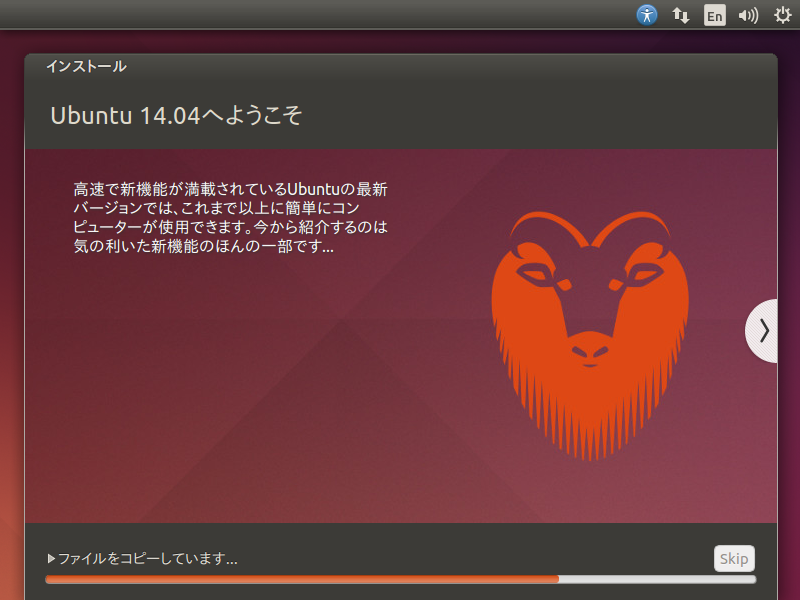
8. 「Ubuntu 14.04へようこそ」:インストール中 その1
9. 「追加のソフツェアを見つけましょう」:インストール中 その2
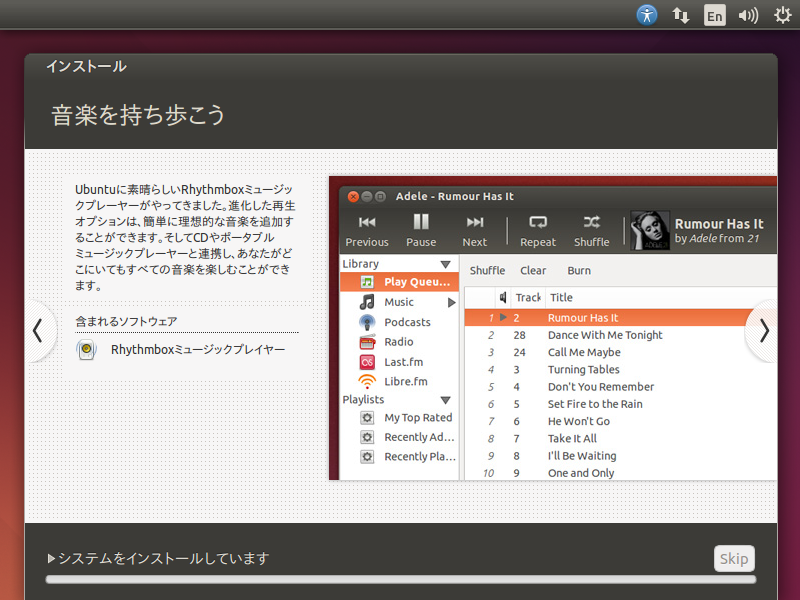
10. 「音楽を持ち歩こう」:インストール中 その3
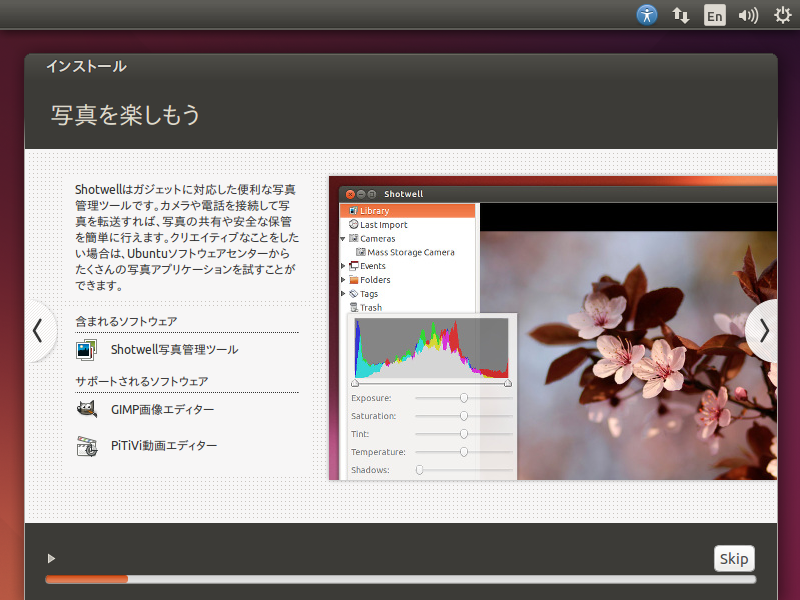
11. 「写真を楽しもう」:インストール中 その4
12. 「ウェブを最大限に活用」:インストール中 その5
13. 「オフィスに必要なものをすべてあなたに」:インストール中 その6
14. 「すべての人へ」:インストール中 その7
15. 「質問がありますか?:インストール中 その8
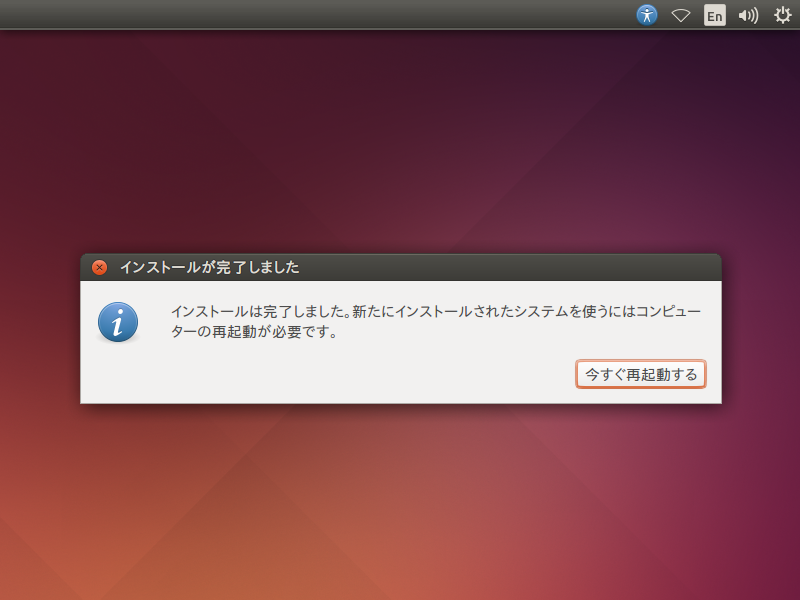
16: 「インストールが完了しました」:[今すぐ再起動する] ボタンを押す。
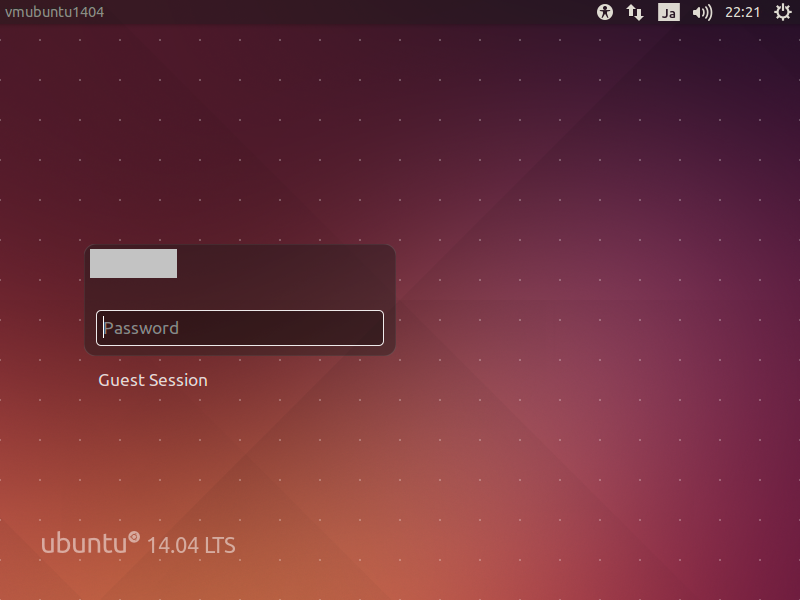
17. ログイン画面が表示される。
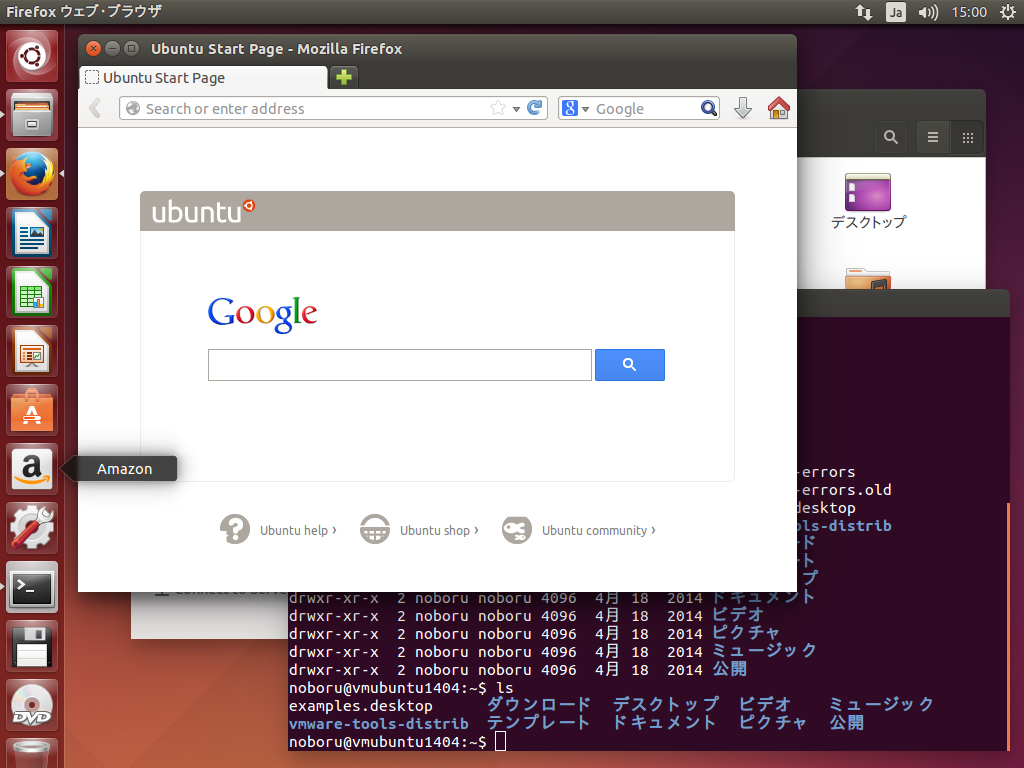
18. ログインしていくつかアプリを起動してみた。
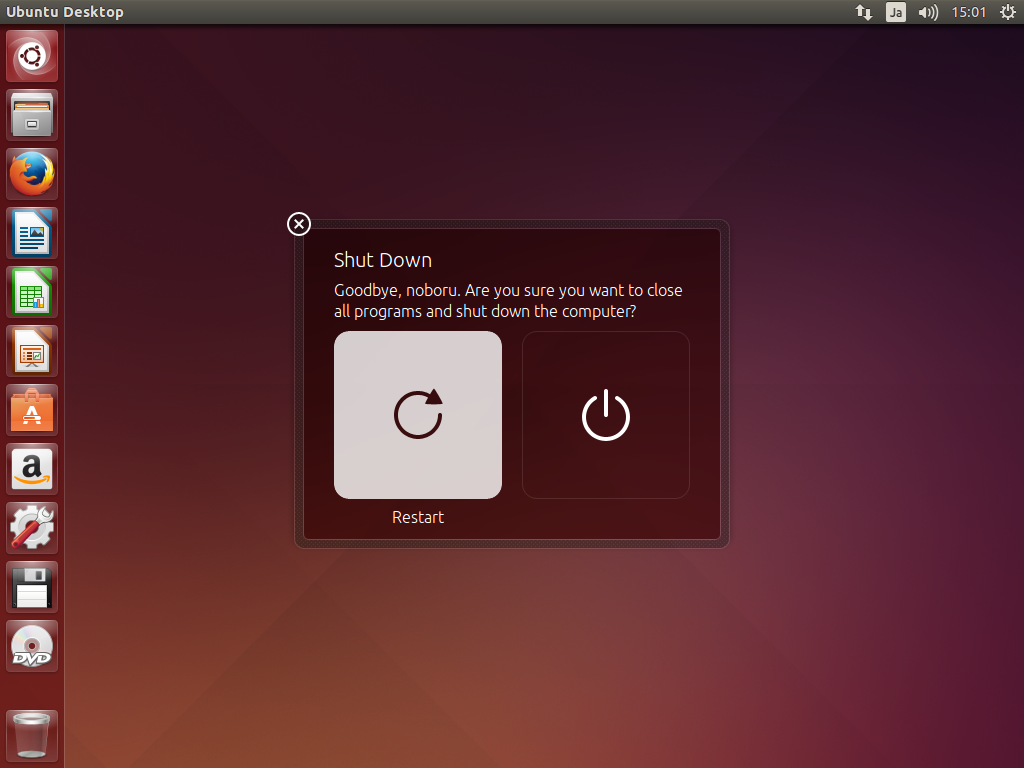
19. 再起動やシャットダウンはこんな画面から操作するようだ…
1. DVD から起動
2. 「ようこそ」:言語で「日本語」を選択して [Ubuntu をインストール] ボタンを押す。
3. 「Ubuntu のインストール準備」:を確認して [続ける] ボタンを押す。
4. 「インストールの種類」:「ディスクを削除して Ubuntu をインストール」を選択して、
[インストール] ボタンを押す。
5. 「どこに住んでいますか?」:"Tokyo" であることを確認して [続ける] ボタンを押す。
6. 「キーボードレイアウト」:「日本語」、「日本語」であることを確認して [続ける] ボタンを押す。
7. 「あなたの情報を入力してください」:適宜入力項目を設定して [続ける] ボタンを押す。
8. 「Ubuntu 14.04へようこそ」:インストール中 その1
9. 「追加のソフツェアを見つけましょう」:インストール中 その2
10. 「音楽を持ち歩こう」:インストール中 その3
11. 「写真を楽しもう」:インストール中 その4
12. 「ウェブを最大限に活用」:インストール中 その5
13. 「オフィスに必要なものをすべてあなたに」:インストール中 その6
14. 「すべての人へ」:インストール中 その7
15. 「質問がありますか?:インストール中 その8
16: 「インストールが完了しました」:[今すぐ再起動する] ボタンを押す。
17. ログイン画面が表示される。
18. ログインしていくつかアプリを起動してみた。
19. 再起動やシャットダウンはこんな画面から操作するようだ…
21日 月曜日、赤口
+ VMware Player 6.0.2 released
https://www.vmware.com/support/player60/doc/player-602-release-notes.html
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ UPDATE: Multiple Vulnerabilities in Cisco ASA Software
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-asa
+ HPSBMU03012 rev.1 - HP Insight Management VCEM Web Client SDK (VCEMSDK) running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04255796-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ UPDATE: HPSBMU02995 rev.4 - HP Software HP Service Manager, Asset Manager, UCMDB Browser, UCMDB Configuration Manager, Executive Scorecard, Server Automation, Diagnostics, LoadRunner, and Performance Center, running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04236102-4%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ UPDATE: HPSBMU02994 rev.2 - HP BladeSystem c-Class Onboard Administrator (OA) running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04236062-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ UPDATE: HPSBMU02999 rev.2 - HP Software Autonomy WorkSite Server (On-Premises Software), Running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04239374-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ UPDATE: HPSBNS03003 rev.3 - HP NonStop Volume Level Encryption (VLE) running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04242672-3%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ Critical Patch Update Advisory - April 2014
http://www.oracle.com/technetwork/jp/topics/security/top-2190049-ja.html
+ Oracle Security Alert for CVE-2014-0160
http://www.oracle.com/technetwork/topics/security/alert-cve-2014-0160-2190703.html
+ UPDATE: VMSA-2014-0004.6 VMware product updates address OpenSSL security vulnerabilities
http://www.vmware.com/security/advisories/VMSA-2014-0004.html
+ VMSA-2014-0003 VMware vSphere Client updates address security vulnerabilities
http://www.vmware.com/security/advisories/VMSA-2014-0003.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1209
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1210
+ jetty-hightide 9.1.4, 8.1.15, 7.6.15 released
http://download.eclipse.org/jetty/stable-9/dist/
http://dist.codehaus.org/jetty/jetty-hightide-8.1.15/
http://dist.codehaus.org/jetty/jetty-hightide-7.6.15/
+ VMware Workstation, Fusion, and Player OpenSSL TLS Heartbeat Buffer Overread Lets Remote Users Obtain Potentially Sensitive Information
http://www.securitytracker.com/id/1030125
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ Apache Tomcat Native Library OpenSSL TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57852/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ MySQL Connector/C TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/58008/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ MySQL Connector/ODBC TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57983/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ MySQL Enterprise Backup TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57969/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ MySQL Workbench TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57961/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ Oracle MySQL Enterprise Monitor OpenSSL TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57851/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ LOCAL: Linux group_info refcounter - Overflow Memory Corruption
http://www.exploit-db.com/exploits/32926
JVNDB-2014-000038 東芝テック製 e-Studio シリーズにおけるクロスサイトリクエストフォージェリの脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000038.html
JVNDB-2014-000040 サイボウズ リモートサービスマネージャーにおけるセッション固定の脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000040.html
JVNDB-2014-000039 サイボウズ リモートサービスマネージャーにおけるサービス運用妨害 (DoS) の脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000039.html
JVNDB-2014-000037 AndExplorer におけるディレクトリトラバーサルの脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000037.html
REMOTE: NRPE <= 2.15 - Remote Command Execution
http://www.exploit-db.com/exploits/32925
https://www.vmware.com/support/player60/doc/player-602-release-notes.html
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ UPDATE: Multiple Vulnerabilities in Cisco ASA Software
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-asa
+ HPSBMU03012 rev.1 - HP Insight Management VCEM Web Client SDK (VCEMSDK) running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04255796-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ UPDATE: HPSBMU02995 rev.4 - HP Software HP Service Manager, Asset Manager, UCMDB Browser, UCMDB Configuration Manager, Executive Scorecard, Server Automation, Diagnostics, LoadRunner, and Performance Center, running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04236102-4%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ UPDATE: HPSBMU02994 rev.2 - HP BladeSystem c-Class Onboard Administrator (OA) running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04236062-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ UPDATE: HPSBMU02999 rev.2 - HP Software Autonomy WorkSite Server (On-Premises Software), Running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04239374-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ UPDATE: HPSBNS03003 rev.3 - HP NonStop Volume Level Encryption (VLE) running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04242672-3%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ Critical Patch Update Advisory - April 2014
http://www.oracle.com/technetwork/jp/topics/security/top-2190049-ja.html
+ Oracle Security Alert for CVE-2014-0160
http://www.oracle.com/technetwork/topics/security/alert-cve-2014-0160-2190703.html
+ UPDATE: VMSA-2014-0004.6 VMware product updates address OpenSSL security vulnerabilities
http://www.vmware.com/security/advisories/VMSA-2014-0004.html
+ VMSA-2014-0003 VMware vSphere Client updates address security vulnerabilities
http://www.vmware.com/security/advisories/VMSA-2014-0003.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1209
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1210
+ jetty-hightide 9.1.4, 8.1.15, 7.6.15 released
http://download.eclipse.org/jetty/stable-9/dist/
http://dist.codehaus.org/jetty/jetty-hightide-8.1.15/
http://dist.codehaus.org/jetty/jetty-hightide-7.6.15/
+ VMware Workstation, Fusion, and Player OpenSSL TLS Heartbeat Buffer Overread Lets Remote Users Obtain Potentially Sensitive Information
http://www.securitytracker.com/id/1030125
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ Apache Tomcat Native Library OpenSSL TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57852/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ MySQL Connector/C TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/58008/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ MySQL Connector/ODBC TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57983/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ MySQL Enterprise Backup TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57969/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ MySQL Workbench TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57961/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ Oracle MySQL Enterprise Monitor OpenSSL TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57851/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ LOCAL: Linux group_info refcounter - Overflow Memory Corruption
http://www.exploit-db.com/exploits/32926
JVNDB-2014-000038 東芝テック製 e-Studio シリーズにおけるクロスサイトリクエストフォージェリの脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000038.html
JVNDB-2014-000040 サイボウズ リモートサービスマネージャーにおけるセッション固定の脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000040.html
JVNDB-2014-000039 サイボウズ リモートサービスマネージャーにおけるサービス運用妨害 (DoS) の脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000039.html
JVNDB-2014-000037 AndExplorer におけるディレクトリトラバーサルの脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000037.html
REMOTE: NRPE <= 2.15 - Remote Command Execution
http://www.exploit-db.com/exploits/32925
2014年4月18日金曜日
18日 金曜日、先負
+ Ubuntu 14.04 LTS released
https://wiki.ubuntu.com/TrustyTahr/ReleaseNotes
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ HPSBGN03010 rev.1 - HP Software Server Automation, "HeartBleed" OpenSSL Vulnerability, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04250814-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBGN03008 rev.1 - HP Software Service Manager, "HeartBleed" OpenSSL Vulnerability, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04248997-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ UPDATE: HPSBMU02999 rev.2 - HP Software Autonomy WorkSite Server (On-Premises Software), Running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04239374-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ UPDATE: HPSBMU02998 rev.2 - HP System Management Homepage (SMH) running OpenSSL on Linux and Windows, Remote Disclosure of Information, Denial of Service (DoS)
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04239372-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ UPDATE: HPSBMU02995 rev.3 - HP Software HP Service Manager, Asset Manager, UCMDB Browser, UCMDB Configuration Manager, Executive Scorecard, Server Automation, Diagnostics, LoadRunner, and Performance Center, running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04236102-3%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HPSBMU02988 rev.1 - HP Universal Configuration Management Database, Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04220407-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6214
+ HPSBMU02987 rev.1 - HP Universal Configuration Management Database Integration Service, Remote Code Execution
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04219959-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6215
+ HPSBMU02982 rev.1 - HP Database and Middleware Automation, Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04201408-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6212
+ UPDATE: HPSBMU02935 rev.1 - HP LoadRunner Virtual User Generatorで、コードがリモート実行される
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04023666-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HPSBMU03009 rev.1 - HP CloudSystem Foundation and Enterprise software v8.0 running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04249113-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ CVE-2013-5211 Input Validation vulnerability in NTP
https://blogs.oracle.com/sunsecurity/entry/cve_2013_5211_input_validation
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5211
+ Samba 4.1.7 Available for Download
http://samba.org/samba/history/samba-4.1.7.html
+ OpenSSL 1.0.1 Missing critical flag for extended key usage
http://cxsecurity.com/issue/WLB-2014040111
Kindle向けウイルスバスターモバイル5.0非公開のお知らせ
http://app.trendmicro.co.jp/support/news.asp?id=2116
ServerProtect for NetApp 5.8 Service Pack 1 build 1164 公開のお知らせ
http://app.trendmicro.co.jp/support/news.asp?id=2108
OpenSSL Vulnerability (Heartbleed bug) for SAP/Sybase products
http://www.sybase.com/detail?id=1099387
OpenSSLの「心臓出血」はクライアントにも影響、サーバーに情報を盗まれる
http://itpro.nikkeibp.co.jp/article/NEWS/20140417/551443/?ST=security
Apache Struts 2の脆弱性対策が急務、攻撃プログラムが出回る
http://itpro.nikkeibp.co.jp/article/NEWS/20140417/551263/?ST=security
トレンドマイクロのパスワード管理ソフトでOpenSSL脆弱性による漏えいか
http://itpro.nikkeibp.co.jp/article/NEWS/20140417/551222/?ST=security
OpenSSLの「心臓出血」脆弱性、悪用の疑いで逮捕者
http://itpro.nikkeibp.co.jp/article/NEWS/20140417/551223/?ST=security
JVNVU#94401838 OpenSSL の heartbeat 拡張に情報漏えいの脆弱性
http://jvn.jp/vu/JVNVU94401838/index.html
JVNVU#93450631 Openfire にサービス運用妨害 (DoS) の脆弱性
http://jvn.jp/vu/JVNVU93450631/index.html
https://wiki.ubuntu.com/TrustyTahr/ReleaseNotes
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ HPSBGN03010 rev.1 - HP Software Server Automation, "HeartBleed" OpenSSL Vulnerability, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04250814-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBGN03008 rev.1 - HP Software Service Manager, "HeartBleed" OpenSSL Vulnerability, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04248997-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ UPDATE: HPSBMU02999 rev.2 - HP Software Autonomy WorkSite Server (On-Premises Software), Running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04239374-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ UPDATE: HPSBMU02998 rev.2 - HP System Management Homepage (SMH) running OpenSSL on Linux and Windows, Remote Disclosure of Information, Denial of Service (DoS)
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04239372-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ UPDATE: HPSBMU02995 rev.3 - HP Software HP Service Manager, Asset Manager, UCMDB Browser, UCMDB Configuration Manager, Executive Scorecard, Server Automation, Diagnostics, LoadRunner, and Performance Center, running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04236102-3%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HPSBMU02988 rev.1 - HP Universal Configuration Management Database, Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04220407-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6214
+ HPSBMU02987 rev.1 - HP Universal Configuration Management Database Integration Service, Remote Code Execution
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04219959-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6215
+ HPSBMU02982 rev.1 - HP Database and Middleware Automation, Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04201408-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6212
+ UPDATE: HPSBMU02935 rev.1 - HP LoadRunner Virtual User Generatorで、コードがリモート実行される
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04023666-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HPSBMU03009 rev.1 - HP CloudSystem Foundation and Enterprise software v8.0 running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04249113-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ CVE-2013-5211 Input Validation vulnerability in NTP
https://blogs.oracle.com/sunsecurity/entry/cve_2013_5211_input_validation
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5211
+ Samba 4.1.7 Available for Download
http://samba.org/samba/history/samba-4.1.7.html
+ OpenSSL 1.0.1 Missing critical flag for extended key usage
http://cxsecurity.com/issue/WLB-2014040111
Kindle向けウイルスバスターモバイル5.0非公開のお知らせ
http://app.trendmicro.co.jp/support/news.asp?id=2116
ServerProtect for NetApp 5.8 Service Pack 1 build 1164 公開のお知らせ
http://app.trendmicro.co.jp/support/news.asp?id=2108
OpenSSL Vulnerability (Heartbleed bug) for SAP/Sybase products
http://www.sybase.com/detail?id=1099387
OpenSSLの「心臓出血」はクライアントにも影響、サーバーに情報を盗まれる
http://itpro.nikkeibp.co.jp/article/NEWS/20140417/551443/?ST=security
Apache Struts 2の脆弱性対策が急務、攻撃プログラムが出回る
http://itpro.nikkeibp.co.jp/article/NEWS/20140417/551263/?ST=security
トレンドマイクロのパスワード管理ソフトでOpenSSL脆弱性による漏えいか
http://itpro.nikkeibp.co.jp/article/NEWS/20140417/551222/?ST=security
OpenSSLの「心臓出血」脆弱性、悪用の疑いで逮捕者
http://itpro.nikkeibp.co.jp/article/NEWS/20140417/551223/?ST=security
JVNVU#94401838 OpenSSL の heartbeat 拡張に情報漏えいの脆弱性
http://jvn.jp/vu/JVNVU94401838/index.html
JVNVU#93450631 Openfire にサービス運用妨害 (DoS) の脆弱性
http://jvn.jp/vu/JVNVU93450631/index.html
2014年4月17日木曜日
17日 木曜日、友引
+ RHSA-2014:0406 Critical: java-1.7.0-openjdk security update
http://rhn.redhat.com/errata/RHSA-2014-0406.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0429
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0446
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0451
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0452
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0453
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0454
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0455
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0456
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0457
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0458
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0459
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0460
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0461
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1876
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2397
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2398
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2402
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2403
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2412
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2413
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2414
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2421
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2423
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2427
+ RHSA-2014:0408 Important: java-1.6.0-openjdk security and bug fix update
http://rhn.redhat.com/errata/RHSA-2014-0408.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0429
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0446
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0451
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0452
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0453
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0456
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0457
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0458
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0460
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0461
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1876
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2397
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2398
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2403
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2412
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2414
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2421
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2423
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2427
+ CESA-2014:0408 Important CentOS 6 java-1.6.0-openjdk Update
http://lwn.net/Alerts/594994/
+ CESA-2014:0408 Important CentOS 5 java-1.6.0-openjdk Update
http://lwn.net/Alerts/594995/
+ CESA-2014:0406 Critical CentOS 6 java-1.7.0-openjdk Update
http://lwn.net/Alerts/594996/
+ CESA-2014:0407 Important CentOS 5 java-1.7.0-openjdk Update
http://lwn.net/Alerts/594997/
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ HPSBMU02999 rev.1 - HP Software Autonomy WorkSite Server (On-Premises Software), Running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04239374-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBMU02996 rev.1 - HP Network Node Manager I (NNMi) for HP-UX, Linux, Solaris, and Windows, Remote Unauthorized Access, Execution of Arbitrary Code
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04026039-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6218
+ HPSBNS03003 rev.1 - HP NonStop Volume Level Encryption (VLE) running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04242672-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ RHSA-2014:0407 Important: java-1.7.0-openjdk security update
http://rhn.redhat.com/errata/RHSA-2014-0407.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0429
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0446
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0451
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0452
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0453
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0454
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0455
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0456
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0457
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0458
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0459
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0460
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0461
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1876
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2397
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2398
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2402
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2403
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2412
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2413
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2414
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2421
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2423
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2427
+ VMware Workstation and Player IOCTL Pointer Dereference Lets Local Users Deny Service
http://www.securitytracker.com/id/1030103
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2384
+ MySQL Multiple Bugs Let Remote Authenticated Users Partially Access and Modify Data and Remote Users Partially Deny Service
http://www.securitytracker.com/id/1030102
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0384
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2419
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2430
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2431
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2432
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2434
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2435
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2436
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2438
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2440
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2442
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2444
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2450
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2451
+ REMOTE: MS14-012 Microsoft Internet Explorer CMarkup Use-After-Free
http://www.exploit-db.com/exploits/32904
+ OpenSSL 1.0.1 Missing critical flag for extended key usage
http://cxsecurity.com/issue/WLB-2014040111
+ Microsoft Internet Explorer CMarkup Use-After-Free Metasploit
http://cxsecurity.com/issue/WLB-2014040108
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0322
+ OpenSSL use-after-free race condition read buffer
http://cxsecurity.com/issue/WLB-2014040079
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-5298
+ Apache HTTPD 2.2.22/ModSecurity 2.7.5 bypass RequestHeader unset
http://cxsecurity.com/issue/WLB-2014040107
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5704
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5705
JVNDB-2014-000041 Redmine におけるオープンリダイレクトの脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000041.html
東京地裁がMTGOXの再生手続開始の申立てを棄却、破産手続きへ
http://itpro.nikkeibp.co.jp/article/NEWS/20140417/551102/?ST=security
Javaに危険な脆弱性が複数、最新版にアップデートを
http://itpro.nikkeibp.co.jp/article/NEWS/20140416/551064/?ST=security
2013年は大規模データ侵害の年、シマンテックがセキュリティ脅威発表
http://itpro.nikkeibp.co.jp/article/NEWS/20140416/551026/?ST=security
OpenSSLの「心臓出血」脆弱性、被害報告が相次ぐ
http://itpro.nikkeibp.co.jp/article/NEWS/20140416/550986/?ST=security
2014年4月 Oracle Java SE のクリティカルパッチアップデートに関する注意喚起
http://www.jpcert.or.jp/at/2014/at140017.html
JVNVU#94401838 OpenSSL の heartbeat 拡張に情報漏えいの脆弱性
http://jvn.jp/vu/JVNVU94401838/index.html
JVNVU#800113 複数の DNS 実装にキャッシュポイズニングの脆弱性
http://jvn.jp/vu/JVNVU800113/index.html
JVN#93004610 Redmine におけるオープンリダイレクトの脆弱性
http://jvn.jp/jp/JVN93004610/index.html
VU#495476 Openfire contains an uncontrolled resource consumption vulnerability
http://www.kb.cert.org/vuls/id/495476
http://rhn.redhat.com/errata/RHSA-2014-0406.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0429
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0446
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0451
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0452
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0453
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0454
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0455
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0456
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0457
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0458
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0459
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0460
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0461
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1876
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2397
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2398
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2402
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2403
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2412
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2413
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2414
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2421
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2423
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2427
+ RHSA-2014:0408 Important: java-1.6.0-openjdk security and bug fix update
http://rhn.redhat.com/errata/RHSA-2014-0408.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0429
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0446
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0451
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0452
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0453
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0456
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0457
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0458
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0460
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0461
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1876
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2397
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2398
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2403
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2412
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2414
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2421
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2423
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2427
+ CESA-2014:0408 Important CentOS 6 java-1.6.0-openjdk Update
http://lwn.net/Alerts/594994/
+ CESA-2014:0408 Important CentOS 5 java-1.6.0-openjdk Update
http://lwn.net/Alerts/594995/
+ CESA-2014:0406 Critical CentOS 6 java-1.7.0-openjdk Update
http://lwn.net/Alerts/594996/
+ CESA-2014:0407 Important CentOS 5 java-1.7.0-openjdk Update
http://lwn.net/Alerts/594997/
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ HPSBMU02999 rev.1 - HP Software Autonomy WorkSite Server (On-Premises Software), Running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04239374-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBMU02996 rev.1 - HP Network Node Manager I (NNMi) for HP-UX, Linux, Solaris, and Windows, Remote Unauthorized Access, Execution of Arbitrary Code
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04026039-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6218
+ HPSBNS03003 rev.1 - HP NonStop Volume Level Encryption (VLE) running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04242672-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ RHSA-2014:0407 Important: java-1.7.0-openjdk security update
http://rhn.redhat.com/errata/RHSA-2014-0407.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0429
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0446
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0451
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0452
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0453
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0454
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0455
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0456
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0457
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0458
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0459
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0460
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0461
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1876
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2397
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2398
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2402
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2403
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2412
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2413
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2414
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2421
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2423
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2427
+ VMware Workstation and Player IOCTL Pointer Dereference Lets Local Users Deny Service
http://www.securitytracker.com/id/1030103
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2384
+ MySQL Multiple Bugs Let Remote Authenticated Users Partially Access and Modify Data and Remote Users Partially Deny Service
http://www.securitytracker.com/id/1030102
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0384
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2419
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2430
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2431
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2432
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2434
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2435
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2436
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2438
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2440
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2442
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2444
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2450
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2451
+ REMOTE: MS14-012 Microsoft Internet Explorer CMarkup Use-After-Free
http://www.exploit-db.com/exploits/32904
+ OpenSSL 1.0.1 Missing critical flag for extended key usage
http://cxsecurity.com/issue/WLB-2014040111
+ Microsoft Internet Explorer CMarkup Use-After-Free Metasploit
http://cxsecurity.com/issue/WLB-2014040108
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0322
+ OpenSSL use-after-free race condition read buffer
http://cxsecurity.com/issue/WLB-2014040079
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-5298
+ Apache HTTPD 2.2.22/ModSecurity 2.7.5 bypass RequestHeader unset
http://cxsecurity.com/issue/WLB-2014040107
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5704
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-5705
JVNDB-2014-000041 Redmine におけるオープンリダイレクトの脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000041.html
東京地裁がMTGOXの再生手続開始の申立てを棄却、破産手続きへ
http://itpro.nikkeibp.co.jp/article/NEWS/20140417/551102/?ST=security
Javaに危険な脆弱性が複数、最新版にアップデートを
http://itpro.nikkeibp.co.jp/article/NEWS/20140416/551064/?ST=security
2013年は大規模データ侵害の年、シマンテックがセキュリティ脅威発表
http://itpro.nikkeibp.co.jp/article/NEWS/20140416/551026/?ST=security
OpenSSLの「心臓出血」脆弱性、被害報告が相次ぐ
http://itpro.nikkeibp.co.jp/article/NEWS/20140416/550986/?ST=security
2014年4月 Oracle Java SE のクリティカルパッチアップデートに関する注意喚起
http://www.jpcert.or.jp/at/2014/at140017.html
JVNVU#94401838 OpenSSL の heartbeat 拡張に情報漏えいの脆弱性
http://jvn.jp/vu/JVNVU94401838/index.html
JVNVU#800113 複数の DNS 実装にキャッシュポイズニングの脆弱性
http://jvn.jp/vu/JVNVU800113/index.html
JVN#93004610 Redmine におけるオープンリダイレクトの脆弱性
http://jvn.jp/jp/JVN93004610/index.html
VU#495476 Openfire contains an uncontrolled resource consumption vulnerability
http://www.kb.cert.org/vuls/id/495476
2014年4月16日水曜日
16日 水曜日、先勝
+ APSB14-12 Security update available for Adobe Reader Mobile
http://helpx.adobe.com/security/products/reader-mobile/apsb14-12.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0514
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ HPSBST03001 rev.1 - HP XP P9500 Disk Array running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04240206-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ CVE-2013-4496 Credentials Management vulnerability in Samba
https://blogs.oracle.com/sunsecurity/entry/cve_2013_4496_credentials_management
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4496
+ CVE-2014-0092 Cryptographic Issues vulnerability in GnuTLS
https://blogs.oracle.com/sunsecurity/entry/cve_2014_0092_cryptographic_issues
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0092
+ Multiple symlink attack vulnerabilities in logilab-commons
https://blogs.oracle.com/sunsecurity/entry/multiple_symlink_attack_vulnerabilities_in
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1838
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1839
+ CVE-2007-0227 Information Disclosure vulnerability in slocate
https://blogs.oracle.com/sunsecurity/entry/cve_2007_0227_information_disclosure
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-0227
+ CVE-2014-0015 Authentication Issues vulnerability in libcurl
https://blogs.oracle.com/sunsecurity/entry/cve_2014_0015_authentication_issues
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0015
+ CVE-2013-4545 Cryptographic Issues vulnerability in libcurl
https://blogs.oracle.com/sunsecurity/entry/cve_2013_4545_cryptographic_issues
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4545
+ CVE-2013-1944 Information Disclosure vulnerability in libcurl
https://blogs.oracle.com/sunsecurity/entry/cve_2013_1944_information_disclosure
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1944
+ CVE-2013-2174 Buffer Errors vulnerability in libcurl
https://blogs.oracle.com/sunsecurity/entry/cve_2013_2174_buffer_errors
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2174
+ CVE-2012-1833 Permissions, Privileges, and Access Controls vulnerability in Grails
https://blogs.oracle.com/sunsecurity/entry/cve_2012_1833_permissions_privileges
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1833
+ CVE-2013-4242 Information Disclosure vulnerability in libgcrypt
https://blogs.oracle.com/sunsecurity/entry/cve_2013_4242_information_disclosure
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4242
+ CVE-2014-0591 Buffer Errors vulnerability in Bind
https://blogs.oracle.com/sunsecurity/entry/cve_2014_0591_buffer_errors
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0591
+ CVE-2007-1859 Improper Authentication vulnerability in XScreenSaver
https://blogs.oracle.com/sunsecurity/entry/cve_2007_1859_improper_authentication
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-1859
+ Multiple Buffer Errors vulnerabilities in FreeType
https://blogs.oracle.com/sunsecurity/entry/multiple_buffer_errors_vulnerabilities_in
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5668
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5669
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5670
+ Oracle Critical Patch Update Advisory - April 2014
http://www.oracle.com/technetwork/topics/security/cpuapr2014-1972952.html
+ Tomcat Connectors 1.2.40 Released
http://tomcat.apache.org/connectors-doc/miscellaneous/changelog.html
+ Tomcat Native 1.1.30 Released
http://tomcat.apache.org/native-doc/miscellaneous/changelog.html
+ Java SE 8u5, 7u55 Released
http://www.oracle.com/technetwork/java/javase/8train-relnotes-latest-2153846.html
http://www.oracle.com/technetwork/java/javase/7u55-relnotes-2177812.html
+ JK-1.2.40 released
http://tomcat.apache.org/connectors-doc/news/20140201.html#1 March - JK-1.2.40 released
+ Samba 4.0.17 Available for Download
http://samba.org/samba/history/samba-4.0.17.html
+ Adobe Reader Mobile Flaw in Javascript API Lets Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1030090
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0514
+ HP-UX Whitelisting (WLI) Unspecified Flaw Lets Local Users Modify Data
http://www.securitytracker.com/id/1030089
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6219
+ VMware Horizon Workspace Server OpenSSL TLS Heartbeat Buffer Overread Lets Remote Users Obtain Potentially Sensitive Information
http://www.securitytracker.com/id/1030088
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ LOCAL: Adobe Reader for Android 11.1.3 - Arbitrary JavaScript Execution
http://www.exploit-db.com/exploits/32884
+ Adobe Reader For Android Javascript Insecure
http://cxsecurity.com/issue/WLB-2014040097
ウイルスバスター ビジネスセキュリティ 9.0 公開のお知らせ
http://app.trendmicro.co.jp/support/news.asp?id=2107
Trend Micro Safe Lock 2.0(仮称)ベータテスト事前登録開始のお知らせ
http://app.trendmicro.co.jp/support/news.asp?id=2112
Database .NET 11 released!
http://www.postgresql.org/about/news/1515/
DNSキャッシュポイズニング攻撃が増加中、管理者はすぐに確認を
http://itpro.nikkeibp.co.jp/article/NEWS/20140415/550823/?ST=security
JVNVU#93935078 Xangati ソフトウェア製品に複数の脆弱性
http://jvn.jp/vu/JVNVU93935078/
JVNVU#91319001 Ontario Systems Artiva Agency に認証不備の脆弱性
http://jvn.jp/vu/JVNVU91319001/
JVNVU#93939159 PaperThin CommonSpot に複数の脆弱性
http://jvn.jp/vu/JVNVU93939159/
REMOTE: Unitrends Enterprise Backup 7.3.0 - Unauthenticated Root RCE
http://www.exploit-db.com/exploits/32885
http://helpx.adobe.com/security/products/reader-mobile/apsb14-12.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0514
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ HPSBST03001 rev.1 - HP XP P9500 Disk Array running OpenSSL, Remote Disclosure of Information
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04240206-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ CVE-2013-4496 Credentials Management vulnerability in Samba
https://blogs.oracle.com/sunsecurity/entry/cve_2013_4496_credentials_management
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4496
+ CVE-2014-0092 Cryptographic Issues vulnerability in GnuTLS
https://blogs.oracle.com/sunsecurity/entry/cve_2014_0092_cryptographic_issues
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0092
+ Multiple symlink attack vulnerabilities in logilab-commons
https://blogs.oracle.com/sunsecurity/entry/multiple_symlink_attack_vulnerabilities_in
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1838
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1839
+ CVE-2007-0227 Information Disclosure vulnerability in slocate
https://blogs.oracle.com/sunsecurity/entry/cve_2007_0227_information_disclosure
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-0227
+ CVE-2014-0015 Authentication Issues vulnerability in libcurl
https://blogs.oracle.com/sunsecurity/entry/cve_2014_0015_authentication_issues
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0015
+ CVE-2013-4545 Cryptographic Issues vulnerability in libcurl
https://blogs.oracle.com/sunsecurity/entry/cve_2013_4545_cryptographic_issues
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4545
+ CVE-2013-1944 Information Disclosure vulnerability in libcurl
https://blogs.oracle.com/sunsecurity/entry/cve_2013_1944_information_disclosure
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1944
+ CVE-2013-2174 Buffer Errors vulnerability in libcurl
https://blogs.oracle.com/sunsecurity/entry/cve_2013_2174_buffer_errors
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2174
+ CVE-2012-1833 Permissions, Privileges, and Access Controls vulnerability in Grails
https://blogs.oracle.com/sunsecurity/entry/cve_2012_1833_permissions_privileges
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-1833
+ CVE-2013-4242 Information Disclosure vulnerability in libgcrypt
https://blogs.oracle.com/sunsecurity/entry/cve_2013_4242_information_disclosure
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4242
+ CVE-2014-0591 Buffer Errors vulnerability in Bind
https://blogs.oracle.com/sunsecurity/entry/cve_2014_0591_buffer_errors
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0591
+ CVE-2007-1859 Improper Authentication vulnerability in XScreenSaver
https://blogs.oracle.com/sunsecurity/entry/cve_2007_1859_improper_authentication
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-1859
+ Multiple Buffer Errors vulnerabilities in FreeType
https://blogs.oracle.com/sunsecurity/entry/multiple_buffer_errors_vulnerabilities_in
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5668
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5669
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-5670
+ Oracle Critical Patch Update Advisory - April 2014
http://www.oracle.com/technetwork/topics/security/cpuapr2014-1972952.html
+ Tomcat Connectors 1.2.40 Released
http://tomcat.apache.org/connectors-doc/miscellaneous/changelog.html
+ Tomcat Native 1.1.30 Released
http://tomcat.apache.org/native-doc/miscellaneous/changelog.html
+ Java SE 8u5, 7u55 Released
http://www.oracle.com/technetwork/java/javase/8train-relnotes-latest-2153846.html
http://www.oracle.com/technetwork/java/javase/7u55-relnotes-2177812.html
+ JK-1.2.40 released
http://tomcat.apache.org/connectors-doc/news/20140201.html#1 March - JK-1.2.40 released
+ Samba 4.0.17 Available for Download
http://samba.org/samba/history/samba-4.0.17.html
+ Adobe Reader Mobile Flaw in Javascript API Lets Remote Users Execute Arbitrary Code
http://www.securitytracker.com/id/1030090
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0514
+ HP-UX Whitelisting (WLI) Unspecified Flaw Lets Local Users Modify Data
http://www.securitytracker.com/id/1030089
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6219
+ VMware Horizon Workspace Server OpenSSL TLS Heartbeat Buffer Overread Lets Remote Users Obtain Potentially Sensitive Information
http://www.securitytracker.com/id/1030088
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ LOCAL: Adobe Reader for Android 11.1.3 - Arbitrary JavaScript Execution
http://www.exploit-db.com/exploits/32884
+ Adobe Reader For Android Javascript Insecure
http://cxsecurity.com/issue/WLB-2014040097
ウイルスバスター ビジネスセキュリティ 9.0 公開のお知らせ
http://app.trendmicro.co.jp/support/news.asp?id=2107
Trend Micro Safe Lock 2.0(仮称)ベータテスト事前登録開始のお知らせ
http://app.trendmicro.co.jp/support/news.asp?id=2112
Database .NET 11 released!
http://www.postgresql.org/about/news/1515/
DNSキャッシュポイズニング攻撃が増加中、管理者はすぐに確認を
http://itpro.nikkeibp.co.jp/article/NEWS/20140415/550823/?ST=security
JVNVU#93935078 Xangati ソフトウェア製品に複数の脆弱性
http://jvn.jp/vu/JVNVU93935078/
JVNVU#91319001 Ontario Systems Artiva Agency に認証不備の脆弱性
http://jvn.jp/vu/JVNVU91319001/
JVNVU#93939159 PaperThin CommonSpot に複数の脆弱性
http://jvn.jp/vu/JVNVU93939159/
REMOTE: Unitrends Enterprise Backup 7.3.0 - Unauthenticated Root RCE
http://www.exploit-db.com/exploits/32885
2014年4月15日火曜日
15日 火曜日、赤口
+ TortoiseSVN 1.8.6 released
http://tortoisesvn.net/tsvn_1.8_releasenotes.html
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ HPSBUX03001 SSRT101382 rev.1 - HP-UX Whitelisting (WLI), Local Unauthorized Access
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04227671-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6219
+ Linux kernel 3.14.1, 3.13.10, 3.10.37, 3.4.87 released
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.14.1
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.13.10
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.10.37
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.4.87
+ UltraMonkey-L7 3.1.1-1 released
http://sourceforge.jp/projects/ultramonkey-l7/releases/
+ LOCAL: Internet Explorer 10 & Adobe Flash Player (12.0.0.70, 12.0.0.77) - CMarkup Use-After-Free
http://www.exploit-db.com/exploits/32851
+ SA57770 VMware Multiple Products OpenSSL TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57770/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ SA57910 NetScreen ScreenOS SSL/TLS Protocol Packet Handling Denial of Service Vulnerability
http://secunia.com/advisories/57910/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2842
+ SA57738 McAfee Email Gateway OpenSSL Multiple Vulnerabilities
http://secunia.com/advisories/57738/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4353
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6449
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6450
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0076
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ Juniper Networks ScreenOS SSL/TLS Protocol Packet Handling Denial of Service Vulnerability
http://www.securityfocus.com/bid/66802
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2842
+ OpenSSL 'ssl3_release_read_buffer()' Use-After-Free Memory Corruption Vulnerability
http://www.securityfocus.com/bid/66801
+ VMware Player and Workstation CVE-2014-2384 Local Denial of Service Vulnerability
http://www.securityfocus.com/bid/66784
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2384
Barman 1.3.1 released
http://www.postgresql.org/about/news/1514/
JVNDB-2014-000036 Android 版 CamiApp における Content Provider のアクセス制限不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000036.html
JVNDB-2014-000035 SD Card Manager におけるディレクトリトラバーサルの脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000035.html
サポート終了後もWindows Server2003を保護、日立ソリューションズが開始
http://itpro.nikkeibp.co.jp/article/NEWS/20140414/550482/?ST=security
マカフィー、マルウエア断片化対策を備えた次世代ファイアウォール
http://itpro.nikkeibp.co.jp/article/NEWS/20140414/550442/?ST=security
米政府、「Heartbleedを情報収集活動に利用」との報道を否定
http://itpro.nikkeibp.co.jp/article/NEWS/20140414/550283/?ST=security
JVNVU#98943832 PivotX に複数の脆弱性
http://jvn.jp/vu/JVNVU98943832/index.html
JVNVU#97596800 Amtelco miSecureMessages に認証不備の脆弱性
http://jvn.jp/vu/JVNVU97596800/index.html
JVNVU#98858887 Fortinet FortiADC にクロスサイトスクリプティングの脆弱性
http://jvn.jp/vu/JVNVU98858887/index.html
JVNVU#94935747 ZyXEL Wireless N300 NetUSB Router に複数の脆弱性
http://jvn.jp/vu/JVNVU94935747/index.html
JVN#55438786 Android 版 CamiApp における Content Provider のアクセス制限不備の脆弱性
http://jvn.jp/jp/JVN55438786/index.html
VU#657622 Xangati software release contains relative path traversal and command injection vulnerabilities
http://www.kb.cert.org/vuls/id/657622
VU#215284 Artiva Agency Single Sign-On (SSO) feature vulnerability
http://www.kb.cert.org/vuls/id/215284
VU#437385 PaperThin CommonSpot CMS contains multiple vulnerabilities
http://www.kb.cert.org/vuls/id/437385
DoS/PoC: WhatsApp < v2.11.7 - Remote Crash
http://www.exploit-db.com/exploits/32865
http://tortoisesvn.net/tsvn_1.8_releasenotes.html
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ HPSBUX03001 SSRT101382 rev.1 - HP-UX Whitelisting (WLI), Local Unauthorized Access
https://h20566.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04227671-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6219
+ Linux kernel 3.14.1, 3.13.10, 3.10.37, 3.4.87 released
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.14.1
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.13.10
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.10.37
https://www.kernel.org/pub/linux/kernel/v3.x/ChangeLog-3.4.87
+ UltraMonkey-L7 3.1.1-1 released
http://sourceforge.jp/projects/ultramonkey-l7/releases/
+ LOCAL: Internet Explorer 10 & Adobe Flash Player (12.0.0.70, 12.0.0.77) - CMarkup Use-After-Free
http://www.exploit-db.com/exploits/32851
+ SA57770 VMware Multiple Products OpenSSL TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57770/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ SA57910 NetScreen ScreenOS SSL/TLS Protocol Packet Handling Denial of Service Vulnerability
http://secunia.com/advisories/57910/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2842
+ SA57738 McAfee Email Gateway OpenSSL Multiple Vulnerabilities
http://secunia.com/advisories/57738/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-4353
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6449
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-6450
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0076
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ Juniper Networks ScreenOS SSL/TLS Protocol Packet Handling Denial of Service Vulnerability
http://www.securityfocus.com/bid/66802
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2842
+ OpenSSL 'ssl3_release_read_buffer()' Use-After-Free Memory Corruption Vulnerability
http://www.securityfocus.com/bid/66801
+ VMware Player and Workstation CVE-2014-2384 Local Denial of Service Vulnerability
http://www.securityfocus.com/bid/66784
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2384
Barman 1.3.1 released
http://www.postgresql.org/about/news/1514/
JVNDB-2014-000036 Android 版 CamiApp における Content Provider のアクセス制限不備の脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000036.html
JVNDB-2014-000035 SD Card Manager におけるディレクトリトラバーサルの脆弱性
http://jvndb.jvn.jp/ja/contents/2014/JVNDB-2014-000035.html
サポート終了後もWindows Server2003を保護、日立ソリューションズが開始
http://itpro.nikkeibp.co.jp/article/NEWS/20140414/550482/?ST=security
マカフィー、マルウエア断片化対策を備えた次世代ファイアウォール
http://itpro.nikkeibp.co.jp/article/NEWS/20140414/550442/?ST=security
米政府、「Heartbleedを情報収集活動に利用」との報道を否定
http://itpro.nikkeibp.co.jp/article/NEWS/20140414/550283/?ST=security
JVNVU#98943832 PivotX に複数の脆弱性
http://jvn.jp/vu/JVNVU98943832/index.html
JVNVU#97596800 Amtelco miSecureMessages に認証不備の脆弱性
http://jvn.jp/vu/JVNVU97596800/index.html
JVNVU#98858887 Fortinet FortiADC にクロスサイトスクリプティングの脆弱性
http://jvn.jp/vu/JVNVU98858887/index.html
JVNVU#94935747 ZyXEL Wireless N300 NetUSB Router に複数の脆弱性
http://jvn.jp/vu/JVNVU94935747/index.html
JVN#55438786 Android 版 CamiApp における Content Provider のアクセス制限不備の脆弱性
http://jvn.jp/jp/JVN55438786/index.html
VU#657622 Xangati software release contains relative path traversal and command injection vulnerabilities
http://www.kb.cert.org/vuls/id/657622
VU#215284 Artiva Agency Single Sign-On (SSO) feature vulnerability
http://www.kb.cert.org/vuls/id/215284
VU#437385 PaperThin CommonSpot CMS contains multiple vulnerabilities
http://www.kb.cert.org/vuls/id/437385
DoS/PoC: WhatsApp < v2.11.7 - Remote Crash
http://www.exploit-db.com/exploits/32865
2014年4月14日月曜日
14日 月曜日、大安
+ phpMyAdmin 4.1.13 released
http://sourceforge.net/p/phpmyadmin/news/2014/04/phpmyadmin-4113-is-released/
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ HPSBMU02997 rev.1 - HP Smart Update Manager (SUM) running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04239375-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBMU02998 rev.1 - HP System Management Homepage (SMH) running OpenSSL on Linux and Windows, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04239372-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ UPDATE: HPSBMU02995 rev.2 - HP Software HP Service Manager, Asset Manager, UCMDB Browser, UCMDB Configuration Manager, Executive Scorecard, Server Automation, Diagnostics, LoadRunner, and Performance Center, running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04236102-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HPSBMU02994 rev.1 - HP BladeSystem c-Class Onboard Administrator (OA) running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04236062-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ VMSA-2014-0003 VMware vSphere Client updates address security vulnerabilities
http://www.vmware.com/security/advisories/VMSA-2014-0003.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1209
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1210
+ MySQL 5.6.18 released
http://dev.mysql.com/doc/relnotes/mysql/5.6/en/news-5-6-18.html
+ Juniper Junos IGMP Processing Flaw Lets Remote Users Deny Service
http://www.securitytracker.com/id/1030062
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0614
+ Juniper Junos Input Validation Flaw in J-Web Permits Cross-Site Scripting Attacks
http://www.securitytracker.com/id/1030061
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2711
+ Juniper Junos SRX Series Enhanced Web Filtering Bug Lets Remote Users Deny Service
http://www.securitytracker.com/id/1030060
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2714
+ Juniper Junos MX Series and T4000 IP Packet Processing Flaw Lets Remote Users Deny Service
http://www.securitytracker.com/id/1030059
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2713
+ Juniper Junos Input Validation Flaw in J-Web Permits Cross-Site Scripting Attacks
http://www.securitytracker.com/id/1030058
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2712
+ Juniper Junos Branch SRX Series Dynamic VPN Flaw Lets Remote Authenticated Users Deny Service
http://www.securitytracker.com/id/1030057
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0612
+ VMware vSphere Client Bugs Let Remote Users Execute Arbitrary Code and Spoof Servers
http://www.securitytracker.com/id/1030055
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1209
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1210
+ SA57891 VMware vSphere Client Update Spoofing Vulnerability
http://secunia.com/advisories/57891/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1209
+ SA57885 VMware vSphere Client Two Spoofing Vulnerabilities
http://secunia.com/advisories/57885/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1209
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1210
+ SA57881 LibreOffice OpenSSL TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57881/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ SA57730 Linux Kernel RDMA MAC Resolve Random Memory Pointer Dereference Denial of Service Vulnerability
http://secunia.com/advisories/57730/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2739
+ LOCAL: Apple Mac OS X Lion Kernel <= xnu-1699.32.7 except xnu-1699.24.8 NFS Mount - Privilege Escalation Exploit
http://www.exploit-db.com/exploits/32813
+ OpenSSL use-after-free race condition read buffer
http://cxsecurity.com/issue/WLB-2014040079
+ VMware Workstation / Player Invalid Pointer Dereference
http://cxsecurity.com/issue/WLB-2014040078
+ Linux Kernel net/ping refcount issue in ping_init_sock() function
http://cxsecurity.com/issue/WLB-2014040072
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2851
+ Mac OS X Lion Kernel <= xnu-1699.32.7 NFS Mount Local Root
http://cxsecurity.com/issue/WLB-2014040070
+ OpenSSL information leak client/server exploit
http://cxsecurity.com/issue/WLB-2014040061
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ Linux Kernel 'ping_init_sock()' Local Privilege Escalation Vulnerability
http://www.securityfocus.com/bid/66779
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2851
+ Linux Kernel Random Memory Pointer Dereference Denial of Service Vulnerability
http://www.securityfocus.com/bid/66775
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2739
+ Juniper Junos J-Web CVE-2014-2712 Multiple Cross Site Scripting Vulnerabilities
http://www.securityfocus.com/bid/66767
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2712
+ Juniper Junos CVE-2014-2713 Denial of Service Vulnerability
http://www.securityfocus.com/bid/66764
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2713
+ Juniper Junos CVE-2014-0614 Denial of Service Vulnerability
http://www.securityfocus.com/bid/66762
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0614
+ Juniper Junos J-Web CVE-2014-2711 HTML Injection Vulnerability
http://www.securityfocus.com/bid/66770
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2711
定期サーバメンテナンスのお知らせ(2014/4/18)
http://app.trendmicro.co.jp/support/news.asp?id=2111
KADOKAWA、2度の不正アクセス被害で閉鎖していたサイトを3週間ぶりに再開
http://itpro.nikkeibp.co.jp/article/NEWS/20140411/550143/?ST=security
JVNVU#94401838 OpenSSL の heartbeat 拡張に情報漏えいの脆弱性
http://jvn.jp/vu/JVNVU94401838/
JVNVU#96484185 Microsoft Office file format converter にメモリ破損の脆弱性
http://jvn.jp/vu/JVNVU96484185/
JVN#47386847 SD Card Manager におけるディレクトリトラバーサルの脆弱性
http://jvn.jp/jp/JVN47386847/
VU#901156 PivotX 2.3.8 contains multiple vulnerabilities
http://www.kb.cert.org/vuls/id/901156
VU#251628 Amtelco miSecureMessages app lacks authentication
http://www.kb.cert.org/vuls/id/251628
VU#667340 Fortinet FortiADC contains a cross-site scripting vulnerability
http://www.kb.cert.org/vuls/id/667340
VU#939260 ZyXEL Wireless N300 NetUSB Router NBG-419N devices contain multiple
http://www.kb.cert.org/vuls/id/939260
http://sourceforge.net/p/phpmyadmin/news/2014/04/phpmyadmin-4113-is-released/
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ HPSBMU02997 rev.1 - HP Smart Update Manager (SUM) running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04239375-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ HPSBMU02998 rev.1 - HP System Management Homepage (SMH) running OpenSSL on Linux and Windows, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04239372-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ UPDATE: HPSBMU02995 rev.2 - HP Software HP Service Manager, Asset Manager, UCMDB Browser, UCMDB Configuration Manager, Executive Scorecard, Server Automation, Diagnostics, LoadRunner, and Performance Center, running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04236102-2%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
+ HPSBMU02994 rev.1 - HP BladeSystem c-Class Onboard Administrator (OA) running OpenSSL, Remote Disclosure of Information
https://h20565.www2.hp.com/portal/site/hpsc/template.PAGE/public/kb/docDisplay/?spf_p.tpst=kbDocDisplay&spf_p.prp_kbDocDisplay=wsrp-navigationalState%3DdocId%253Demr_na-c04236062-1%257CdocLocale%253Dja_JP%257CcalledBy%253D&javax.portlet.begCacheTok=com.vignette.cachetoken&javax.portlet.endCacheTok=com.vignette.cachetoken
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ VMSA-2014-0003 VMware vSphere Client updates address security vulnerabilities
http://www.vmware.com/security/advisories/VMSA-2014-0003.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1209
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1210
+ MySQL 5.6.18 released
http://dev.mysql.com/doc/relnotes/mysql/5.6/en/news-5-6-18.html
+ Juniper Junos IGMP Processing Flaw Lets Remote Users Deny Service
http://www.securitytracker.com/id/1030062
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0614
+ Juniper Junos Input Validation Flaw in J-Web Permits Cross-Site Scripting Attacks
http://www.securitytracker.com/id/1030061
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2711
+ Juniper Junos SRX Series Enhanced Web Filtering Bug Lets Remote Users Deny Service
http://www.securitytracker.com/id/1030060
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2714
+ Juniper Junos MX Series and T4000 IP Packet Processing Flaw Lets Remote Users Deny Service
http://www.securitytracker.com/id/1030059
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2713
+ Juniper Junos Input Validation Flaw in J-Web Permits Cross-Site Scripting Attacks
http://www.securitytracker.com/id/1030058
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2712
+ Juniper Junos Branch SRX Series Dynamic VPN Flaw Lets Remote Authenticated Users Deny Service
http://www.securitytracker.com/id/1030057
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0612
+ VMware vSphere Client Bugs Let Remote Users Execute Arbitrary Code and Spoof Servers
http://www.securitytracker.com/id/1030055
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1209
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1210
+ SA57891 VMware vSphere Client Update Spoofing Vulnerability
http://secunia.com/advisories/57891/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1209
+ SA57885 VMware vSphere Client Two Spoofing Vulnerabilities
http://secunia.com/advisories/57885/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1209
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1210
+ SA57881 LibreOffice OpenSSL TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57881/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ SA57730 Linux Kernel RDMA MAC Resolve Random Memory Pointer Dereference Denial of Service Vulnerability
http://secunia.com/advisories/57730/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2739
+ LOCAL: Apple Mac OS X Lion Kernel <= xnu-1699.32.7 except xnu-1699.24.8 NFS Mount - Privilege Escalation Exploit
http://www.exploit-db.com/exploits/32813
+ OpenSSL use-after-free race condition read buffer
http://cxsecurity.com/issue/WLB-2014040079
+ VMware Workstation / Player Invalid Pointer Dereference
http://cxsecurity.com/issue/WLB-2014040078
+ Linux Kernel net/ping refcount issue in ping_init_sock() function
http://cxsecurity.com/issue/WLB-2014040072
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2851
+ Mac OS X Lion Kernel <= xnu-1699.32.7 NFS Mount Local Root
http://cxsecurity.com/issue/WLB-2014040070
+ OpenSSL information leak client/server exploit
http://cxsecurity.com/issue/WLB-2014040061
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ Linux Kernel 'ping_init_sock()' Local Privilege Escalation Vulnerability
http://www.securityfocus.com/bid/66779
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2851
+ Linux Kernel Random Memory Pointer Dereference Denial of Service Vulnerability
http://www.securityfocus.com/bid/66775
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2739
+ Juniper Junos J-Web CVE-2014-2712 Multiple Cross Site Scripting Vulnerabilities
http://www.securityfocus.com/bid/66767
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2712
+ Juniper Junos CVE-2014-2713 Denial of Service Vulnerability
http://www.securityfocus.com/bid/66764
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2713
+ Juniper Junos CVE-2014-0614 Denial of Service Vulnerability
http://www.securityfocus.com/bid/66762
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0614
+ Juniper Junos J-Web CVE-2014-2711 HTML Injection Vulnerability
http://www.securityfocus.com/bid/66770
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2711
定期サーバメンテナンスのお知らせ(2014/4/18)
http://app.trendmicro.co.jp/support/news.asp?id=2111
KADOKAWA、2度の不正アクセス被害で閉鎖していたサイトを3週間ぶりに再開
http://itpro.nikkeibp.co.jp/article/NEWS/20140411/550143/?ST=security
JVNVU#94401838 OpenSSL の heartbeat 拡張に情報漏えいの脆弱性
http://jvn.jp/vu/JVNVU94401838/
JVNVU#96484185 Microsoft Office file format converter にメモリ破損の脆弱性
http://jvn.jp/vu/JVNVU96484185/
JVN#47386847 SD Card Manager におけるディレクトリトラバーサルの脆弱性
http://jvn.jp/jp/JVN47386847/
VU#901156 PivotX 2.3.8 contains multiple vulnerabilities
http://www.kb.cert.org/vuls/id/901156
VU#251628 Amtelco miSecureMessages app lacks authentication
http://www.kb.cert.org/vuls/id/251628
VU#667340 Fortinet FortiADC contains a cross-site scripting vulnerability
http://www.kb.cert.org/vuls/id/667340
VU#939260 ZyXEL Wireless N300 NetUSB Router NBG-419N devices contain multiple
http://www.kb.cert.org/vuls/id/939260
2014年4月11日金曜日
11日 金曜日、友引
+ CESA-2014:0383 Moderate CentOS 6 samba4 Update
http://lwn.net/Alerts/594269/
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ Oracle Critical Patch Update Pre-Release Announcement - April 2014
http://www.oracle.com/technetwork/topics/security/cpuapr2014-1972952.html
+ VU#882841 Microsoft Office file format converter memory corruption vulnerability
http://www.kb.cert.org/vuls/id/882841
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1757
+ REMOTE: Heartbleed OpenSSL Information Leak Exploit
http://www.exploit-db.com/exploits/32791
+ LOCAL: MS14-017 Microsoft Word RTF Object Confusion
http://www.exploit-db.com/exploits/32793
+ OpenSSL information leak client/server exploit
http://cxsecurity.com/issue/WLB-2014040061
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ SA57788 Juniper JunOS J-Web System Monitoring Script Insertion Vulnerability
http://secunia.com/advisories/57788/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2711
+ SA57790 Juniper JunOS J-Web Multiple Cross-Site Scripting Vulnerabilities
http://secunia.com/advisories/57790/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2712
+ SA57794 Juniper JunOS MX-Series Routers IP Packet Handling Denial of Service Vulnerability
http://secunia.com/advisories/57794/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2713
+ SA57819 Juniper JunOS IGMP Packet Processing Denial of Service Vulnerability
http://secunia.com/advisories/57819/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0614
+ SA57835 Juniper JunOS SRX-Series Service Gateways flowd Denial of Service Vulnerability
http://secunia.com/advisories/57835/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2714
+ SA57849 McAfee SIEM OpenSSL TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57849/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ SA57772 Juniper Multiple Products OpenSSL TLS/DTLS Heartbeat Information Disclosure Vulnerabilities
http://secunia.com/advisories/57772/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ SA57801 Wireshark Libpcap CAP Files Parsing Memory Corruption Vulnerability
http://secunia.com/advisories/57801/
+ Wireshark 'CAP' File Memory Corruption Vulnerability
http://www.securityfocus.com/bid/66755
Advisory: Critical vulnerability found in OpenSSL affecting Sophos products
http://www.sophos.com/en-us/support/knowledgebase/120854.aspx
ウイルスバスター モバイル(iOS) バージョン1.0.1303リリースのお知らせ
http://app.trendmicro.co.jp/support/news.asp?id=2110
ウイルスバスター モバイル バージョン5.0.0.1225リリースのお知らせ
http://app.trendmicro.co.jp/support/news.asp?id=2109
Postgres Open 2014 - Opens the Call for Papers
http://www.postgresql.org/about/news/1512/
法人向けネットバンキングでも不正送金、シマンテックが注意喚起
http://itpro.nikkeibp.co.jp/article/NEWS/20140410/549842/?ST=security
UPDATE: JVNVU#94401838 OpenSSL の heartbeat 拡張に情報漏えいの脆弱性
http://jvn.jp/vu/JVNVU94401838/index.html
REMOTE: Sophos Web Protection Appliance Interface Authenticated Arbitrary Command Execution
http://www.exploit-db.com/exploits/32789
REMOTE: Vtiger Install Unauthenticated Remote Command Execution
http://www.exploit-db.com/exploits/32794
http://lwn.net/Alerts/594269/
+ UPDATE: OpenSSL Heartbeat Extension Vulnerability in Multiple Cisco Products
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
+ Oracle Critical Patch Update Pre-Release Announcement - April 2014
http://www.oracle.com/technetwork/topics/security/cpuapr2014-1972952.html
+ VU#882841 Microsoft Office file format converter memory corruption vulnerability
http://www.kb.cert.org/vuls/id/882841
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1757
+ REMOTE: Heartbleed OpenSSL Information Leak Exploit
http://www.exploit-db.com/exploits/32791
+ LOCAL: MS14-017 Microsoft Word RTF Object Confusion
http://www.exploit-db.com/exploits/32793
+ OpenSSL information leak client/server exploit
http://cxsecurity.com/issue/WLB-2014040061
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ SA57788 Juniper JunOS J-Web System Monitoring Script Insertion Vulnerability
http://secunia.com/advisories/57788/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2711
+ SA57790 Juniper JunOS J-Web Multiple Cross-Site Scripting Vulnerabilities
http://secunia.com/advisories/57790/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2712
+ SA57794 Juniper JunOS MX-Series Routers IP Packet Handling Denial of Service Vulnerability
http://secunia.com/advisories/57794/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2713
+ SA57819 Juniper JunOS IGMP Packet Processing Denial of Service Vulnerability
http://secunia.com/advisories/57819/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0614
+ SA57835 Juniper JunOS SRX-Series Service Gateways flowd Denial of Service Vulnerability
http://secunia.com/advisories/57835/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-2714
+ SA57849 McAfee SIEM OpenSSL TLS/DTLS Heartbeat Two Information Disclosure Vulnerabilities
http://secunia.com/advisories/57849/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ SA57772 Juniper Multiple Products OpenSSL TLS/DTLS Heartbeat Information Disclosure Vulnerabilities
http://secunia.com/advisories/57772/
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
+ SA57801 Wireshark Libpcap CAP Files Parsing Memory Corruption Vulnerability
http://secunia.com/advisories/57801/
+ Wireshark 'CAP' File Memory Corruption Vulnerability
http://www.securityfocus.com/bid/66755
Advisory: Critical vulnerability found in OpenSSL affecting Sophos products
http://www.sophos.com/en-us/support/knowledgebase/120854.aspx
ウイルスバスター モバイル(iOS) バージョン1.0.1303リリースのお知らせ
http://app.trendmicro.co.jp/support/news.asp?id=2110
ウイルスバスター モバイル バージョン5.0.0.1225リリースのお知らせ
http://app.trendmicro.co.jp/support/news.asp?id=2109
Postgres Open 2014 - Opens the Call for Papers
http://www.postgresql.org/about/news/1512/
法人向けネットバンキングでも不正送金、シマンテックが注意喚起
http://itpro.nikkeibp.co.jp/article/NEWS/20140410/549842/?ST=security
UPDATE: JVNVU#94401838 OpenSSL の heartbeat 拡張に情報漏えいの脆弱性
http://jvn.jp/vu/JVNVU94401838/index.html
REMOTE: Sophos Web Protection Appliance Interface Authenticated Arbitrary Command Execution
http://www.exploit-db.com/exploits/32789
REMOTE: Vtiger Install Unauthenticated Remote Command Execution
http://www.exploit-db.com/exploits/32794
登録:
投稿 (Atom)